Introduction
Bouncy Castle is one of the most widely used open source cryptographic APIs for Java and C#. It implements a comprehensive set of resources spanning over major security areas, including cryptography, public key infrastructure, digital signatures, authentication, and secure communication. For those needing a high level of assurance and compliance, there are also FIPS-certified versions of the APIs for both Java and C#.
Background
The Bouncy Castle Cryptography project had its first official release in May 2000. The initial release was in Java and featured a low-level API for small and embedded devices, as well as a provider for the Java Cryptographic Architecture (JCA) for developers working on the general purpose JVMs. The C# APIs were added in 2003 and as the APIs grew in size, a Software Charity, Legion of the Bouncy Castle Inc., was set up to manage and maintain ownership on the codebase. In 2012 a consulting firm, Crypto Workshop, was established by members of the Bouncy Castle Development teams and this led to the efforts resulting in the first FIPS 140-2 certifications for both the Java and C# APIs.
Work on the APIs continues and with Crypto Workshop's acquisition by PrimeKey, now Keyfactor, the core development team is now expanding and the extra resources that being part of a larger organization provides have seen improvements in the quality, maintenance, and certainty about the future of the APIs. The project is still Open Source, and still owned by the Charity.
Capabilities
The Bouncy Castle project provides a set of libraries that cover core cryptographic primitives, such as ciphers, key transport, key agreement, MACs, message digests, and signatures as well as higher-level protocols.
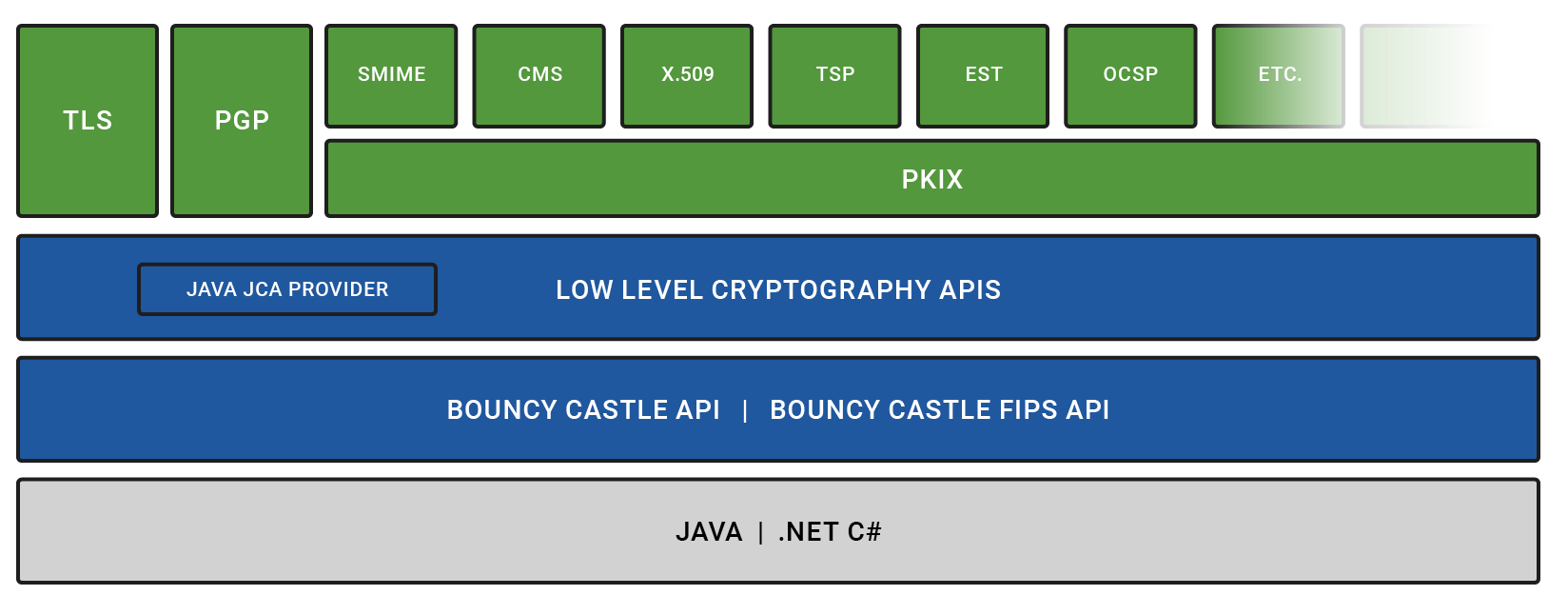
Examples of ciphers include national standards such as AES, ARIA, Camellia, and SM3. Signature algorithms include those based on Elliptic Curve (EC), Edwards Curve, DSA, and RSA. In addition to RSA and EC, additional public key algorithms such as ElGamal and Diffie-Hellman are also provided for key transport and key agreement as well. NIST standard MAC algorithms such as CMAC, HMAC, as well as the newer KMAC, are supported, as well as the SHA-2 family of digests, the SHA-3 family (including SHAKE128/SHAKE256), in addition to other digest algorithms such as Whirlpool, RIPEMD, and Tiger, together with Blake2 and Blake3.
High-level APIs are provided for X.509 certificate generation and processing involving CRMF, CMC, CMP, EST, and PKCS#10. There are also APIs for supporting additional protocols such as CMS, DANE, PEM, S/MIME, Time-Stamp Protocol, and OpenPGP. A Transport Layer Security (TLS) API, with a JSSE provider for Java, is also available and provides support up to TLS 1.3, together with the PSK and SRP extensions.
For an overview of Bouncy Castle's capabilities and support, see Interoperability.
What does Bouncy Castle mean to you?
As Bouncy Castle is a set of APIs, the project itself is really targeted at users wanting to build applications making use of cryptographic services.
Both the Java and C# libraries come in two types, a general public API, and certified versions. Both types are open source, but early access to the certified versions, together with access to the testing tools required to certify them is only available to holders of Bouncy Castle support contracts. The decision to use a certified or uncertified version of the APIs is largely determined by the target audience for your application. For more information about the FIPS early access program, refer to Bouncy Castle Support & Maintenance.
Getting Started with Bouncy Castle
If you are a developer, we recommend the following resources to help you get started:
- For information on the latest Bouncy Castle Java releases, with links to source and Javadoc, see Latest Releases at bouncycastle.org.
- For more information and Bouncy Castle example code, refer to Documentation at bouncycastle.org.
- To learn more about the Bouncy Castle FIPS Java API and how it presents cryptography, see the The Bouncy Castle FIPS Java API in 100 Examples PDF and code example tar file.
- Watch a training on how to use the Bouncy Castle APIs for generating certificates and certification requests on: Training: PKI at the Edge.
If you are a development manager or someone looking for technology for your team, see the following overviews:
To find out what the Bouncy Castle team is currently doing and talking about, see our latest posts:
→ Hardcore Crypto: NIST Post Quantum Competition and more
→ Bouncy Castle Wiki on GitHub