HSM
In the HSM tab and subtabs, you can configure the Hardware Security Module (HSM) of the Hardware Appliance.
The HSM configuration options offer the following:
- Change the authentication codes of the PKCS#11 slots
- Change the PIN of BackupKeyShareSmartCards
- Make one- to-one copies of backup protection cards
- Change the PIN of user credentials on smart cards for slot activation
- Download a full protected backup of the HSM's key material
- Handle HSM key synchronization across a cluster.
Please note that the functionality displayed might differ depending on your setup.
Overview
This tab provides you with an overview of the HSM configuration.
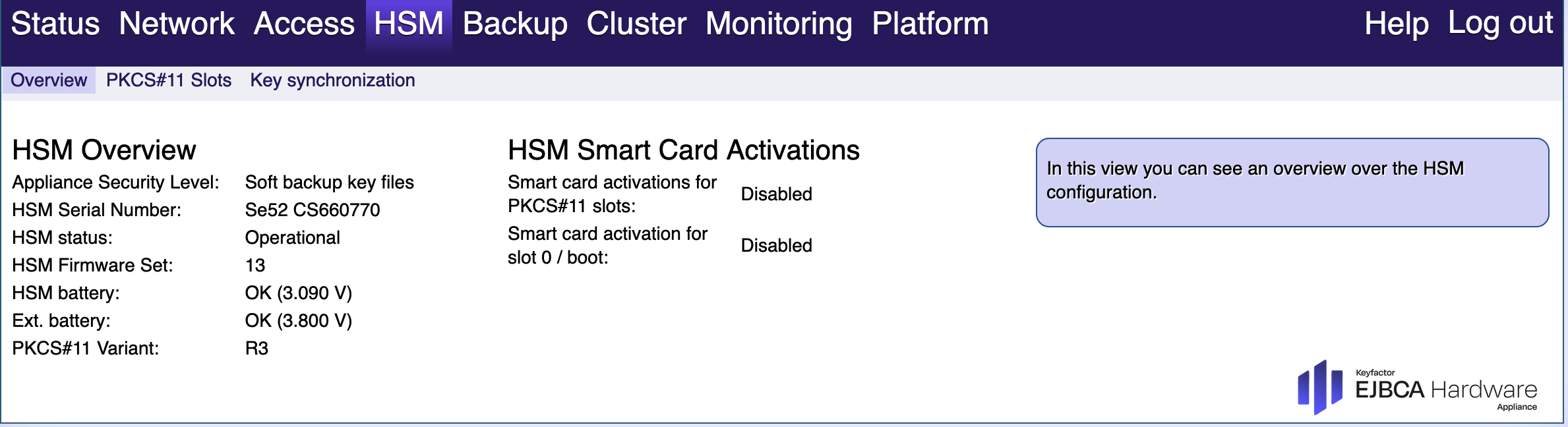
PKCS#11 Slots
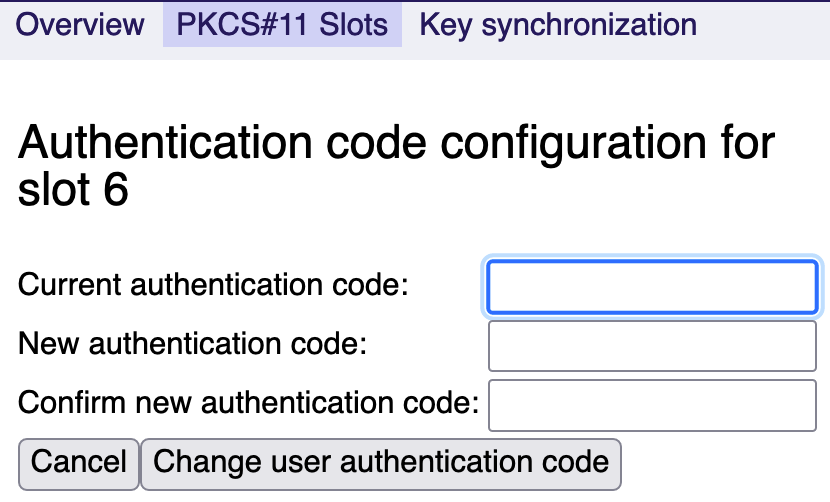
You can switch between automatically generated or manually specified authentication codes. By default, all slots are configured to be used with automatically generated authentication codes. Those are stored in EJBCA and have auto-activation enabled.
A PKCS#11 slot authentication code must have at least 8 characters!
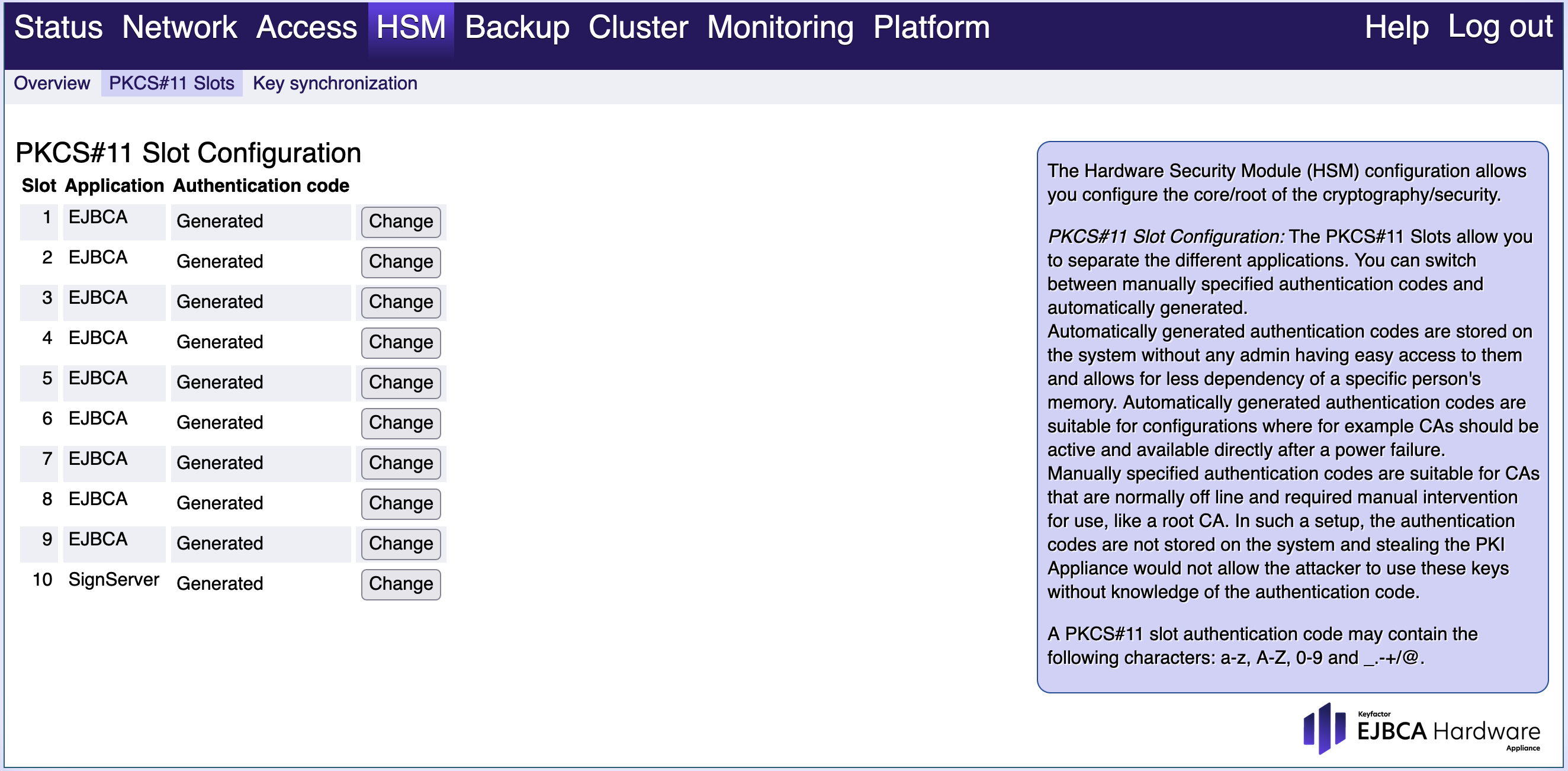
Switching from generated to manually entered authentication code
Manually entered authentication codes are not stored on the system, but known by the administrator, administrators or m out of n administrators in conjunction.
Pros: Key material is not necessarily compromised in the case of lost physical access of the box.
Cons: After a reboot, the PKCS#11 slot must be manually activated using the authentication code.
Changing a manually entered authentication code
Manually entered authentication codes can be updated in the WebConf by selecting Change. Note that this might destroy existing sessions to the slot and could require a re-authentication.
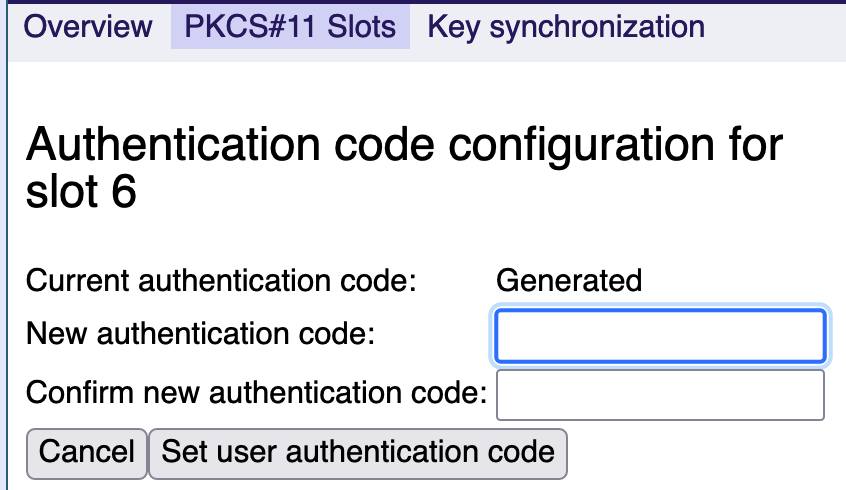
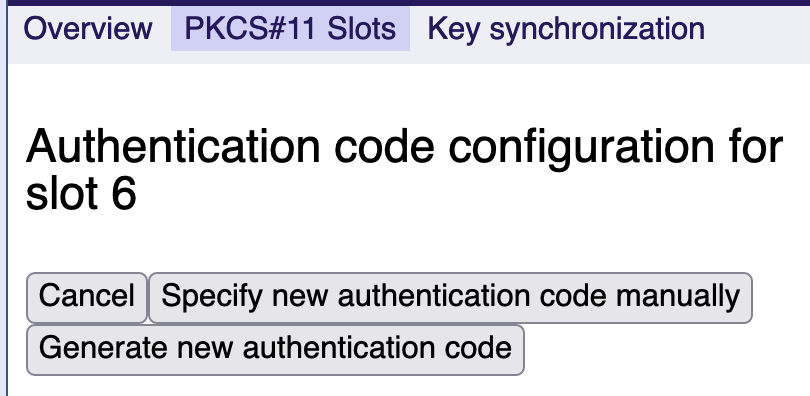
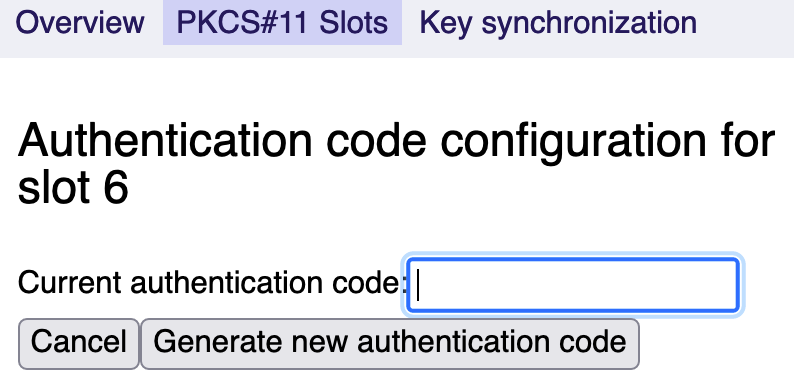
Switching to auto-generated authentication code
Auto-generated authentication codes are stored on the system and never shown to the user/administrator. When switching to a generated authentication code, EJBCA is re-configured to automatically activate the slot on startup.
Pros: Highly available. Authentication code is very hard to brute force. Authentication code cannot be disclosed by administrators.
Cons: Possible to extract given physical access to the machine (theft of the Hardware Appliance could not rule out that the key material of the slot could not be freely accessed).
Key Synchronization
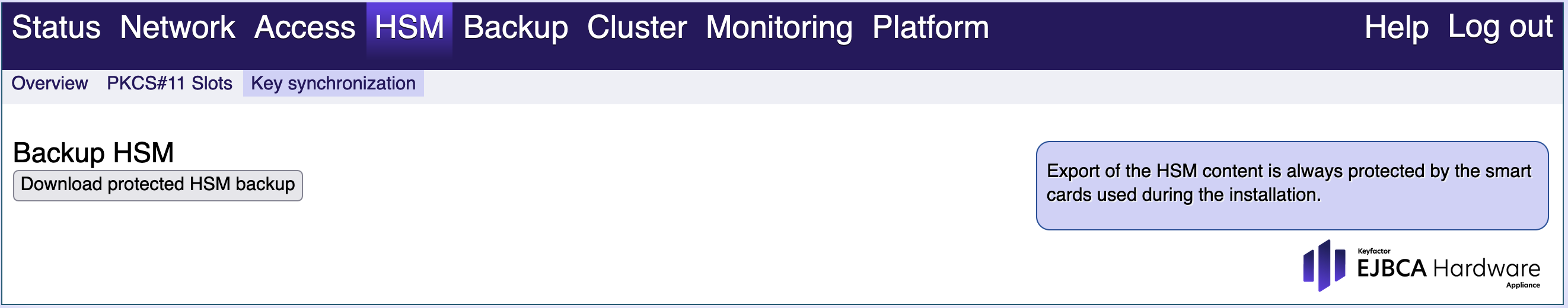
Download protected HSM export
This will download the HSM key material so that you can migrate your data into another, external system. The format of the files is specific to the HSM vendor. The export is protected using the Backup Key for the higher Appliance Security Levels.
Smart Card Operations
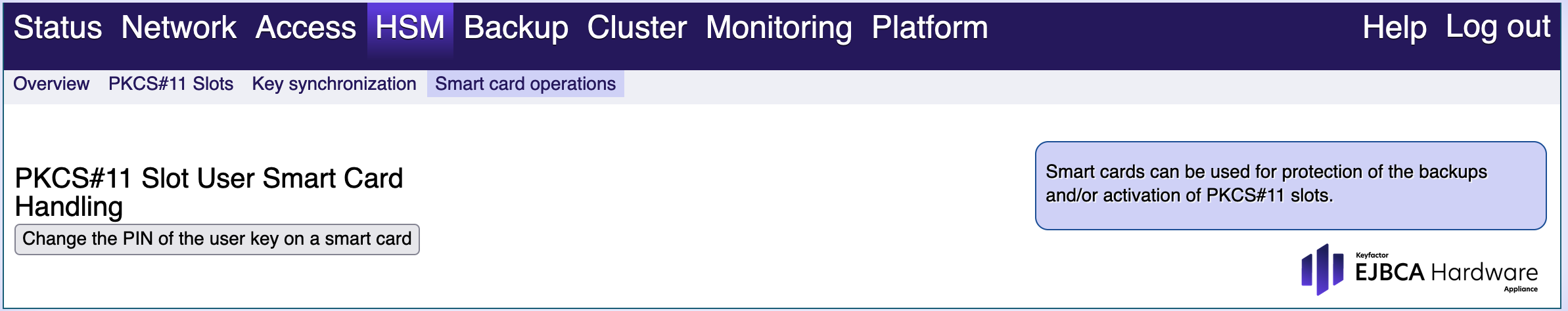
These options are only available if you initialized the Hardware Appliance using smart cards for backup protection. To use these functions, connect the PIN pad to a USB port of the Hardware Appliance. Please note that the USB port of the HSM (the USB port on the PCI card, only accessible from the back) will not work. Use the USB ports on the front of the Hardware Appliance.
Change the PIN of the Backup Key Share on a smart card
Use this function for the following:
- Change the PIN of the backup key share on a smart card. This is strongly recommended for each of the backup key share smart cards. It prevents a mixup or accidental overwriting of the contents of a smart card.
- Assign the card to another person of the company.
- Change the PIN on a smart card that comes originally from another Hardware Appliance.
If you have additionally secured your PKCS#11 slots with smart card authentication, a similar functionality is offered to change the PIN of a PKCS#11 slot user on a smart card. That function can also be used to change the PIN of an HSM Admin User credential on a smart card.
Cluster Key Synchronization Packages
Only available in a cluster environment, these sections allow you to download (and upload) an (encrypted) package with all information needed to deploy your latest key material changes to the other nodes of your cluster environment.
If you create a new key in the HSM through EJBCA (e.g. creating a new CA), the knowledge about its existence will synchronize through the database, but the key itself will not synchronize automatically. Hence, you will have to manually distribute this new key data by downloading a Key Synchronization Package on the Node where you created the new CA and uploading it to each of the other nodes. The applications (EJBCA, SignServer) will automatically be restarted, so that the key material can be used.