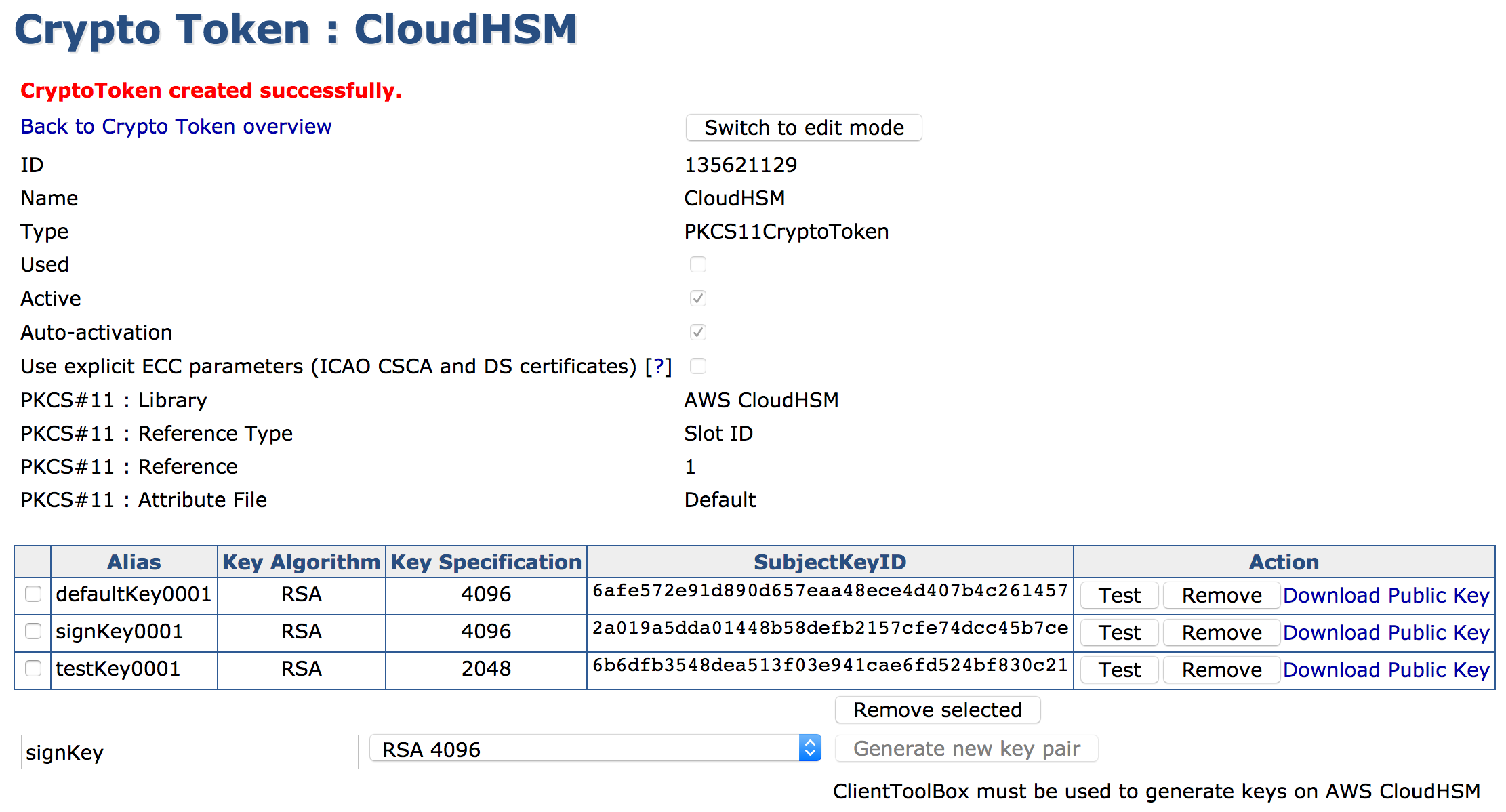
NOTE If you have already performed these steps before creating the keys with the clientToolBox, restart EJBCA using the command service wildfly restart.
If you are creating the crypto token for the first time, proceed with the following steps:
- Login to EJBCA as Superadmin.
- Select Crypto Tokens and click Create new:
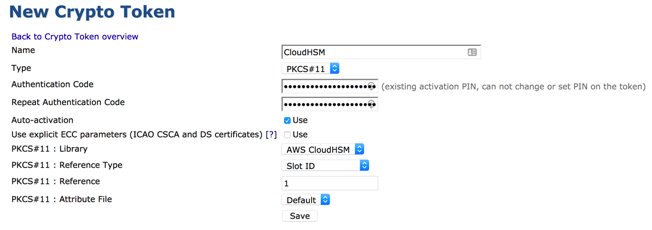
Specify the values as follows:
For EJBCA 7.5 and above:
Name: <anything> (For example "CloudHSM Root Slot")
Type: PKCS#11 NG
Authentication Code: <HSM_CryptoUser>:<password> (ex. CryptoUser:CUPassword123!)
AutoActivation: Checked for all but Root CAs, generally
Use Explicit ECC parameters: Clear
PKCS#11: Library: AWS CloudHSM
PKCS#11: Reference Type: Slot/Token Label
PKCS#11: Reference: cavium
- PKCS#11: Attribute Type: Default
For EJBCA 7.4.3.3 and below:Name: <anything> (For example "CloudHSM Root Slot")
Type: PKCS#11
Authentication Code: <HSM_CryptoUser>:<password> (ex. CryptoUser:CUPassword123!)
AutoActivation: Checked for all but Root CAs, generally
Use Explicit ECC parameters: Clear
PKCS#11: Library: AWS CloudHSM PrimeKey
PKCS#11: Reference Type: Slot ID
PKCS#11: Reference: 1
PKCS#11: Attribute Type: Default
Click Save.
All keys in the slot created by ClientToolBox display in the Crypto Token: