Galera replication uses the following ports for communication:
To create a security group that allows for Galera traffic within the VPCs, follow the steps below.
In this example, the VPC internal address space is 172.16.0.0/16 in US-East-1. The address space in US-East-2 is 172.31.0.0/16.
- Create a Security Group called "All Galera Traffic" with the following rules:
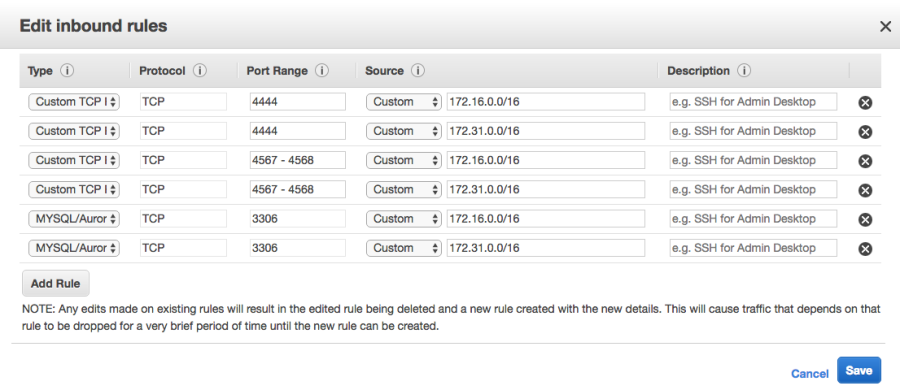
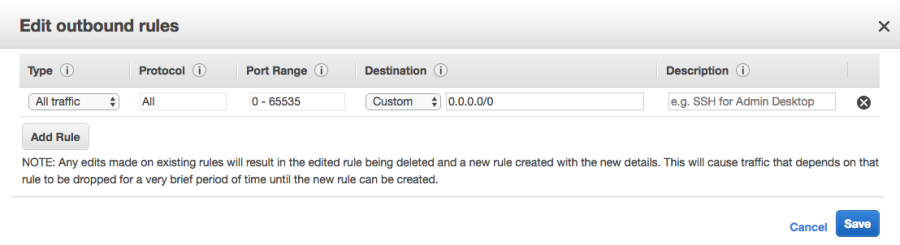
This will allow any connections outbound to any address and any inbound connection on ports 3306, 4567, 4568 and 4444 from any address on the 172.16.0.0/16 and 172.31.0.0/16 subnets. The same rule in the other VPC will also need the same rule configured. These rules may be tightened as required for the organization.
- To apply these Security Groups to the EJBCA Enterprise Cloud Nodes in each of the VPCs, right-click the node, select Networking and then ChangeSecurityGroups.
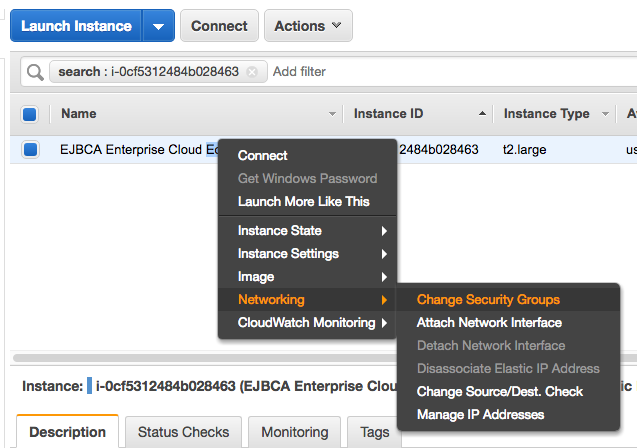
- Apply the security group to the instance so that it can communicate with the other nodes in the cluster.
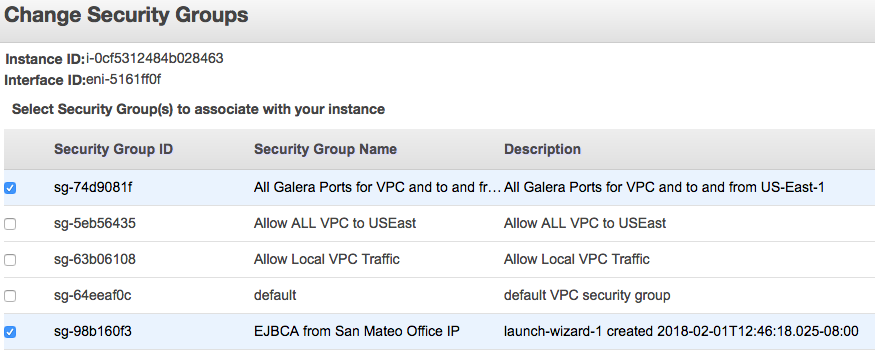
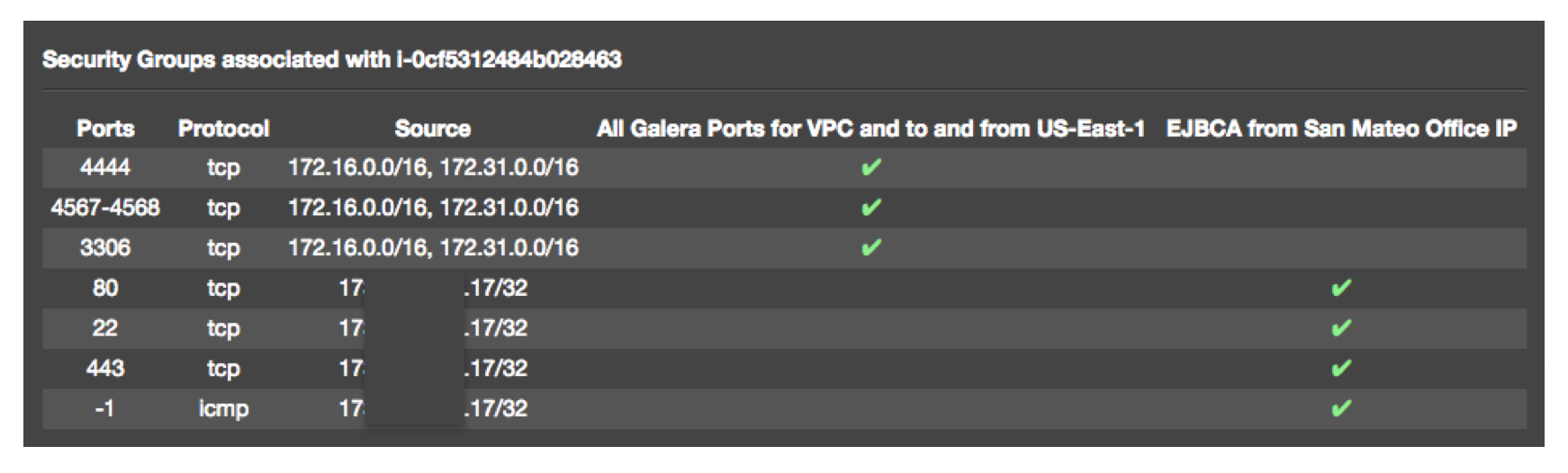
- In the node details there is a link to View Inbound Rules. The associated IPs should be something like this (modified for your IP ranges subnets).