To create a user and CLI key, do the following:
- Login to the AWS Console that contains your EJBCA Cloud Instance.
- Select Services, IAM.
- If a user does not already exist for access to S3, create one by clicking Users.
- Click Add User and add a username for this user, for example EJBCAS3CRLPublisher.
- Select the Access type Programmatic access to allow this user to use the CLI (as well as other APIs) only.
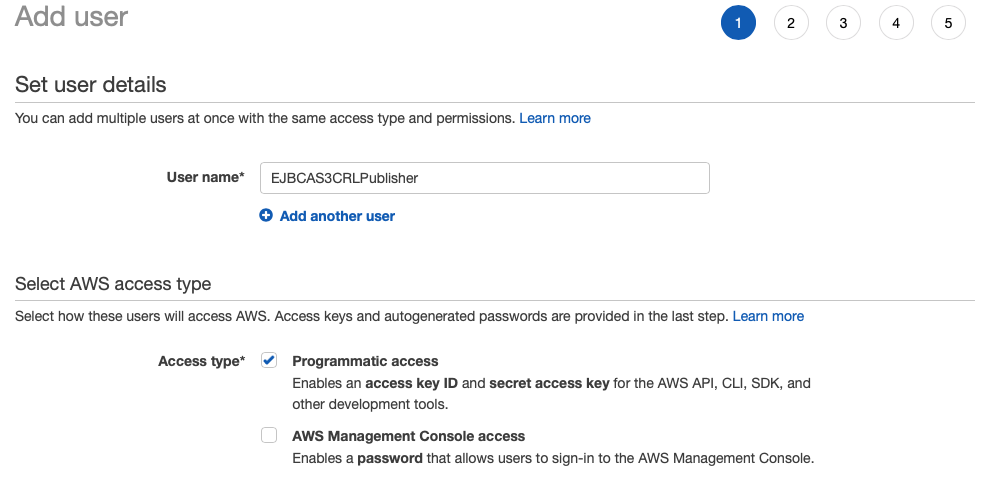
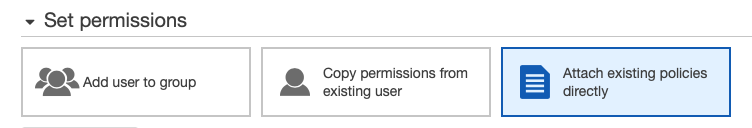
- Click Next: Permissions and select Attach existing policies directly.
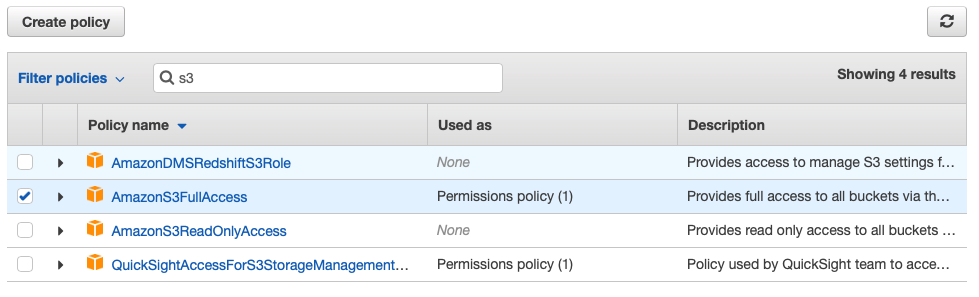
- In the Filter policies search box, enter S3 and then select AmazonS3FullAccess. If required, you may create more restricted access.
- Click Next: Tags.
- Add any optional tags and then click Next: Review.
- Click Create user.
- The confirmation screen shows successful user creation. Note the Access key ID and Secret access key. Download the CSV file that contains these items or store them in a secure place such as KeyPass or LastPass. These credentials will be needed in the AWS CLI Configuration.
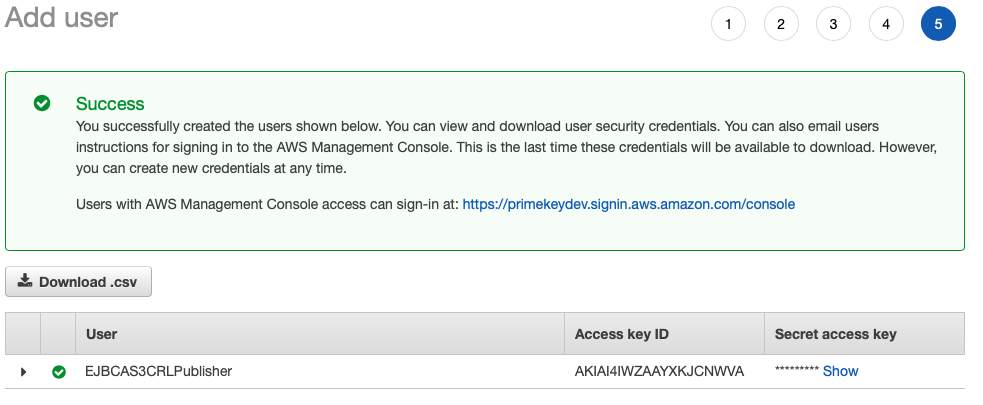
- Click Close.
Optional: Create a Role for the User
To optionally create a role for the user, do the following:
- If a role does not already exist for access to S3, create one by clicking Roles > Create Role.
- Select S3 under the section Choose the service that will use this role, and then click Next: Permissions.
- In the Filter policies search box, type S3 and then select AmazonS3FullAccess. If you would like to create more restricted access, you may do so. Click Next: Tags.

- Add any optional tags and click Next: Review.
- In Role name, enter a name for the role, for example, S3FullAccessForAWSCLI.
- Click Create Role and confirm that the following message is shown.
- You can then attach this role to a user instead of a policy.
Next, Configure the AWS CLI.