Occasionally, you need to generate new certificates for other hosts. This can be other EJBCA hosts or even a server running Apache. You can always use other EJBCA protocols such as ACME to do this, but you can also do it on the EJBCA Cloud host directly with the scripts provided.
To generate new certificates for other hosts, do the following:
- SSH into the CA server and navigate to the
/opt/PrimeKey/support directory. - To generate TLS certificates for another host on the EJBCA Cloud CA host, use the
create_ra_tls_certs.sh script.
Since many hosts will most likely have two IP addresses and two DNS addresses, those are indicated with the -d and -i flags. In this example, use the alternate name of webserver.domain.com simulating an alternate name to reference this host by. In this case, the IP and DNS names the host has are:- ec2-13-59-110-179.us-east-2.compute.amazonaws.com
- ip-172-31-0-115.ec2.internal
- 13.59.110.179
- 172.31.0.115
- webserver.domain.com
# /opt/PrimeKey/support/create_ra_tls_certs.sh -d ec2-13-59-110-179.us-east-2.compute.amazonaws.com -d webserver.domain.com -d ip-172-31-0-115.ec2.internal -i 13.59.110.179 -i 172.31.0.115
BASH
- The script will prompt to request to generate the certificates in the format that Apache will expect them on the RA.
- Choose Y and press Enter. It will output the following files into the /home/ec2-user/pem directory for easy copying.
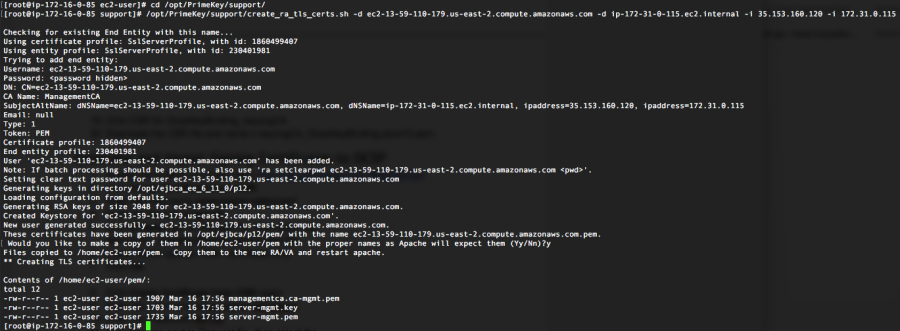
The following three files are output:- managementca.ca-mgmt.pem: The issuing CA certificate.
- server-mgmt.key: The private key for the device certificate.
- server-mgmt.pem: The device public certificate.
- Copy these files to the server they will be used on and put them into place for your particular use case.