CA and RA Configuration
The following describes how to generate an Apache certificate, configure TLS connections between the CA and RA, and the steps included in setting up peer systems.
Apache Certificate Generation for the RA
Generate the Apache Certificate for the RA by following the instructions for the CA and the RA Server below.
Step 1: On the CA
SSH into the CA server and navigate to the /opt/PrimeKey/support directory.
Start by taking a backup of the system:
# /opt/PrimeKey/support/system_backup.shGenerate TLS certificates for the RA server on the CA. Since an RA will most likely have two IP addresses (one internal and one external), those are indicated with the "-i" flag. In this case the IP addresses the host has are:
- 40.121.65.197
- 10.4.0.4
# /opt/PrimeKey/support/create_ra_tls_certs.sh -i 40.121.65.197 -i 10.4.0.4If you are using a load balancer you can include that VIP name in the command above by specifying a "-d". if the domain was ra.example.com the command would be:
# /opt/PrimeKey/support/create_ra_tls_certs.sh -i 40.121.65.197 -i 10.4.0.4 -d ra.example.comThe script will prompt to request to generate the certificates in the format that Apache will expect them on the RA.
Choose Y and press enter. It will output these files into the home directory of the user you provisioned the instance with. In this case the user is "azure-user" so the certificates will be in the /home/azure-user/pem directory for easy copying. If you would like to keep them with the hostname in the file for easy tracking, press N.
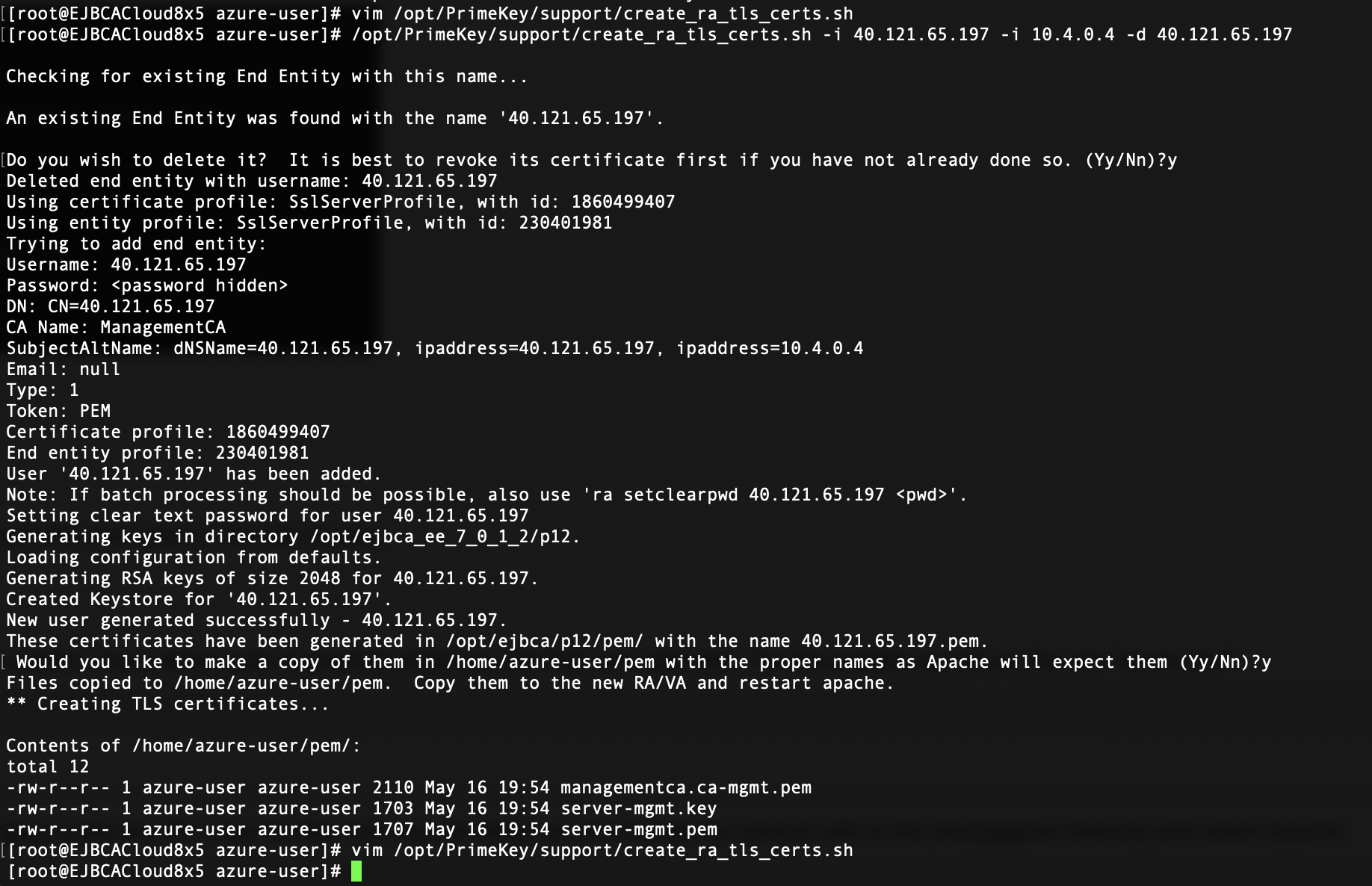
The three files output will be:
- managementca.ca-mgmt.pem
- server-mgmt.key
- server-mgmt.pem
Copy these files to the RA server and put them into place with the instructions in the next section.
Step 2: On the RA Server
SSH into the RA server and start by taking a backup of the system. Azure allows users to provision instances with their own username. For this example we will use the user "azure-user".
# /opt/PrimeKey/support/system_backup.shCopy the three files that were copied to /home/azure-user/pem to the new RA. Copy the files from the user folder you provisioned the instance with to the /etc/httpd/ssl directory and restart Apache:
# cp /home/azure-user/pem/* /etc/httpd/ssl/
# service httpd restartConvert the server to an RA using the install_ra.sh script. This script will import the ManagementCA certificate from the CA server so that the RA is managed by the same ManagementCA as the CA server.
# /opt/PrimeKey/support/install_ra.shThe script will ask for the path to the ManagementCA PEM file from the CA server.
Use the managementca PEM that was copied to the /etc/httpd/ssl directory or copy a new one. Use absolute paths.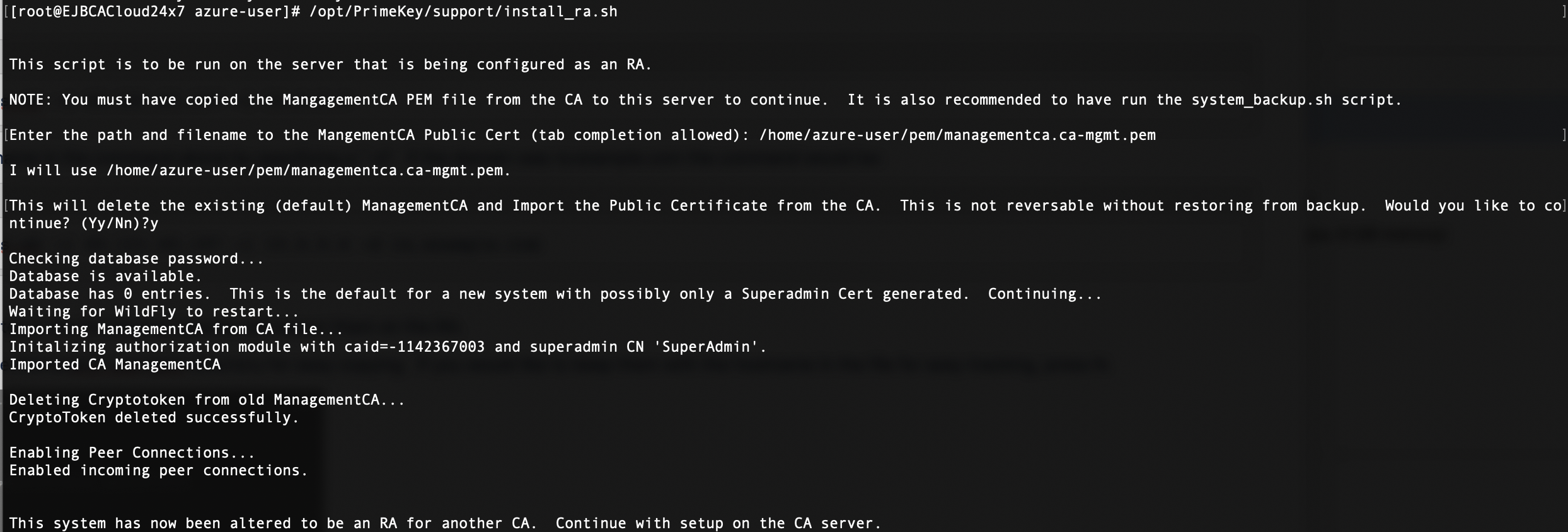
Access the RA Administration GUI with the same certificate used to access the CA server. Test this by going to the EJBCA Admin Web on the RA. Note that there is no Management CA configured, an external ManagementCA is used. 
Step 3. Import CA Certs to RA
On the CA, Click RA Web on the left side navigation and open the CAs RA web. Select CA Certificates and CRLs.
- Download the CA certificates from the CA, RA web in PEM format.
- Access the RA Servers administration UI and click Certification Authorities
- Click Import CA Certificate.
- Browse to the Root CA PEM file and select it.
- Enter the name of the CA in the CA Name field.
- Click Import CA Certificate.
- Repeat for any other CAs.
All imported CAs will show as an "External CA"
Configure TLS Connections Between the CA and RA
Step 1: Import Profiles on the CA
SSH into the CA server and import the profiles that are going to be used for generating the key binding and peer connection certificates.
# /opt/ejbca/bin/ejbca.sh ca importprofiles -d /opt/PrimeKey/ra_profiles/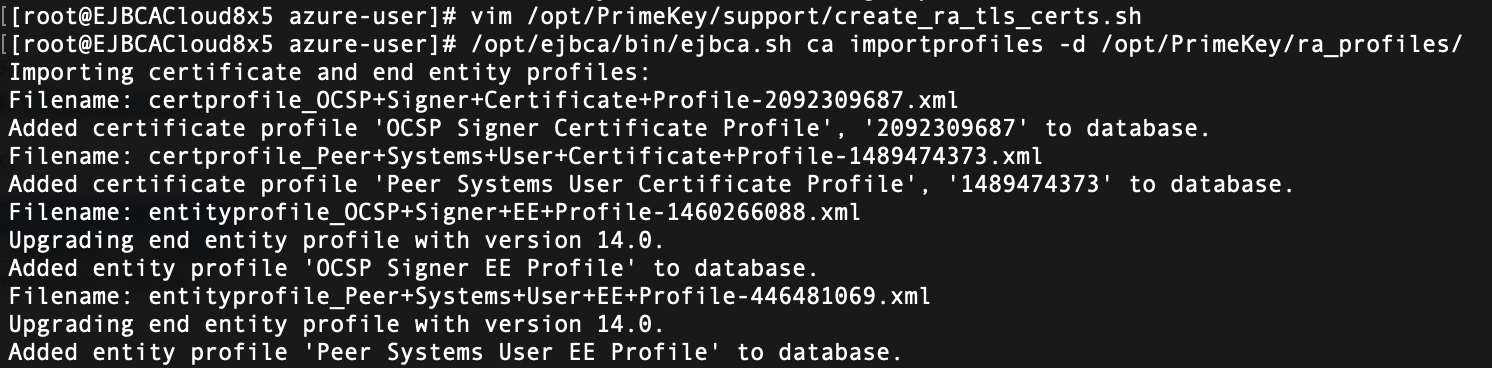
Step 2: Create Crypto Token to store Peer Systems authentication key on CA
Create a Crypto Token for the key binding to use. Navigate to Crypto Tokens and select Create new.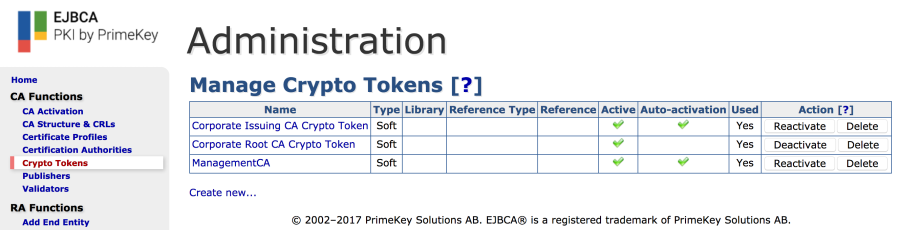
- Enter a name: Peer Systems Token.
- Select Type: Soft.
- Enter and repeat Authentication Code.
- Enable Auto-activation.
- Click Save.
- Generate new key pair:
- Alias: peer_systems_auth_key.
- Key Spec: RSA 4096.
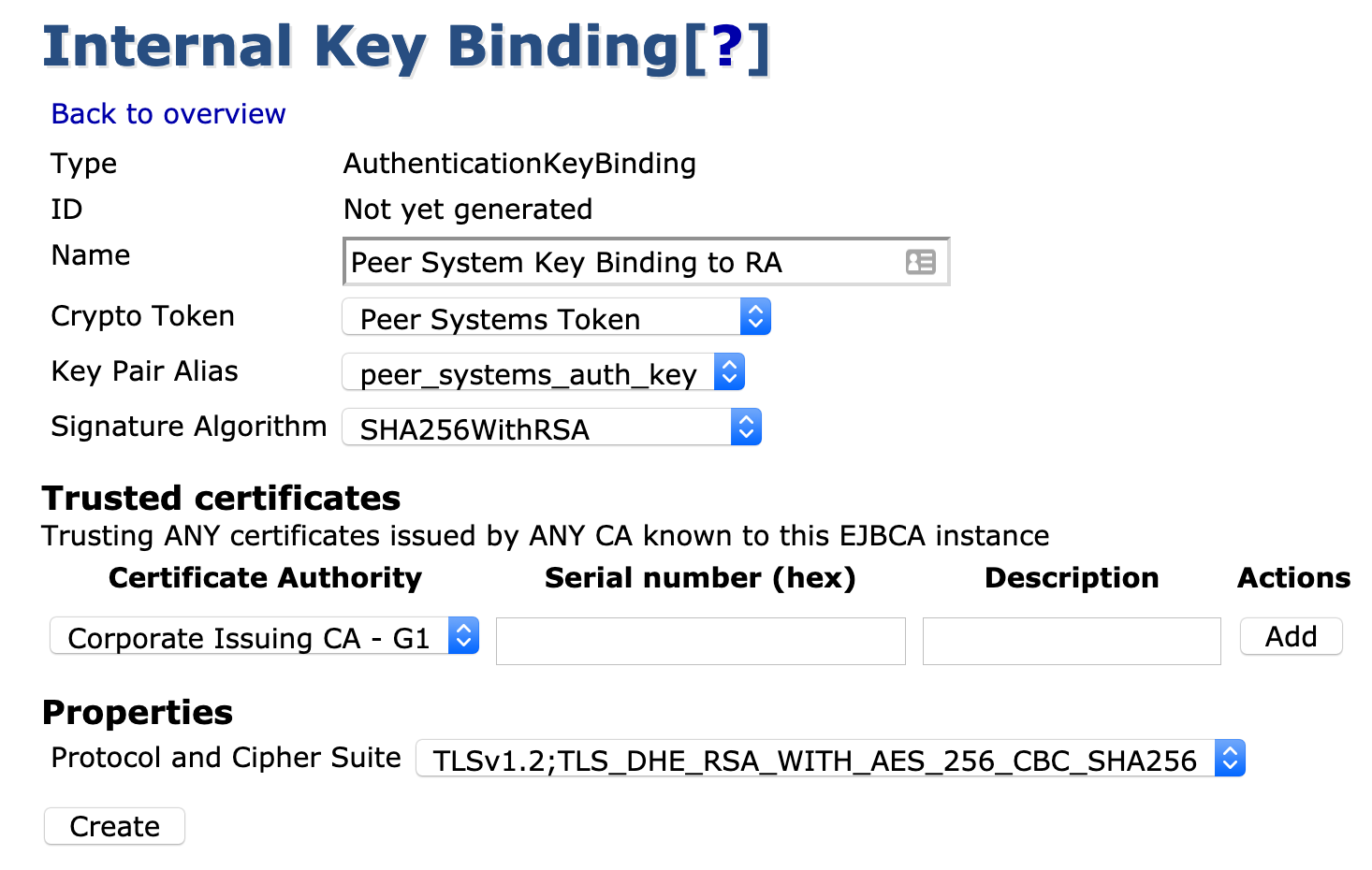
Step 3: Set up Authentication Key Binding for Mutual Authentication on CA
Create an internal key binding for authenticating the TLS connection to the RA. Start by selecting Internal Key Bindings on the CA. 
- Click Create new on the AuthenticationKeyBinding tab.
- Enter a name: Peer System Key Binding to RA.
- Select Crypto Token: "Peer Systems Token".
- Key Pair Alias: peer_systems_auth_key.
- Signature Algorithm: SHA256WithRSA.
- Click Create.
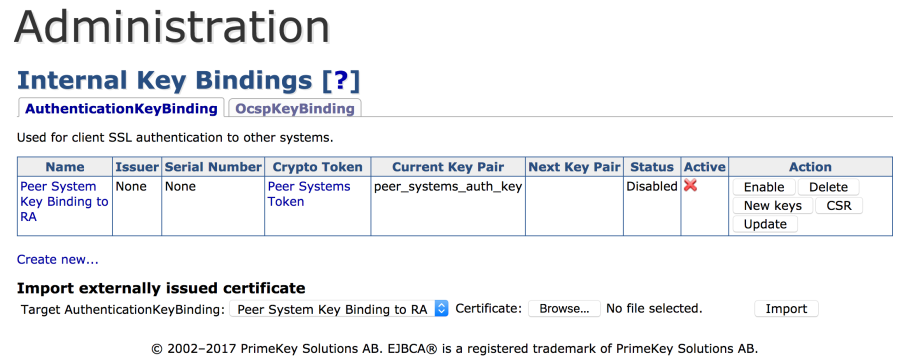
Click Back to overview to go back to the AuthenticationKeyBinding tab and select CSR under the Action column and save the file (Peer System Key Binding to RA.pkcs10.pem).
Step 4: Generate Certificate for TLS Connection
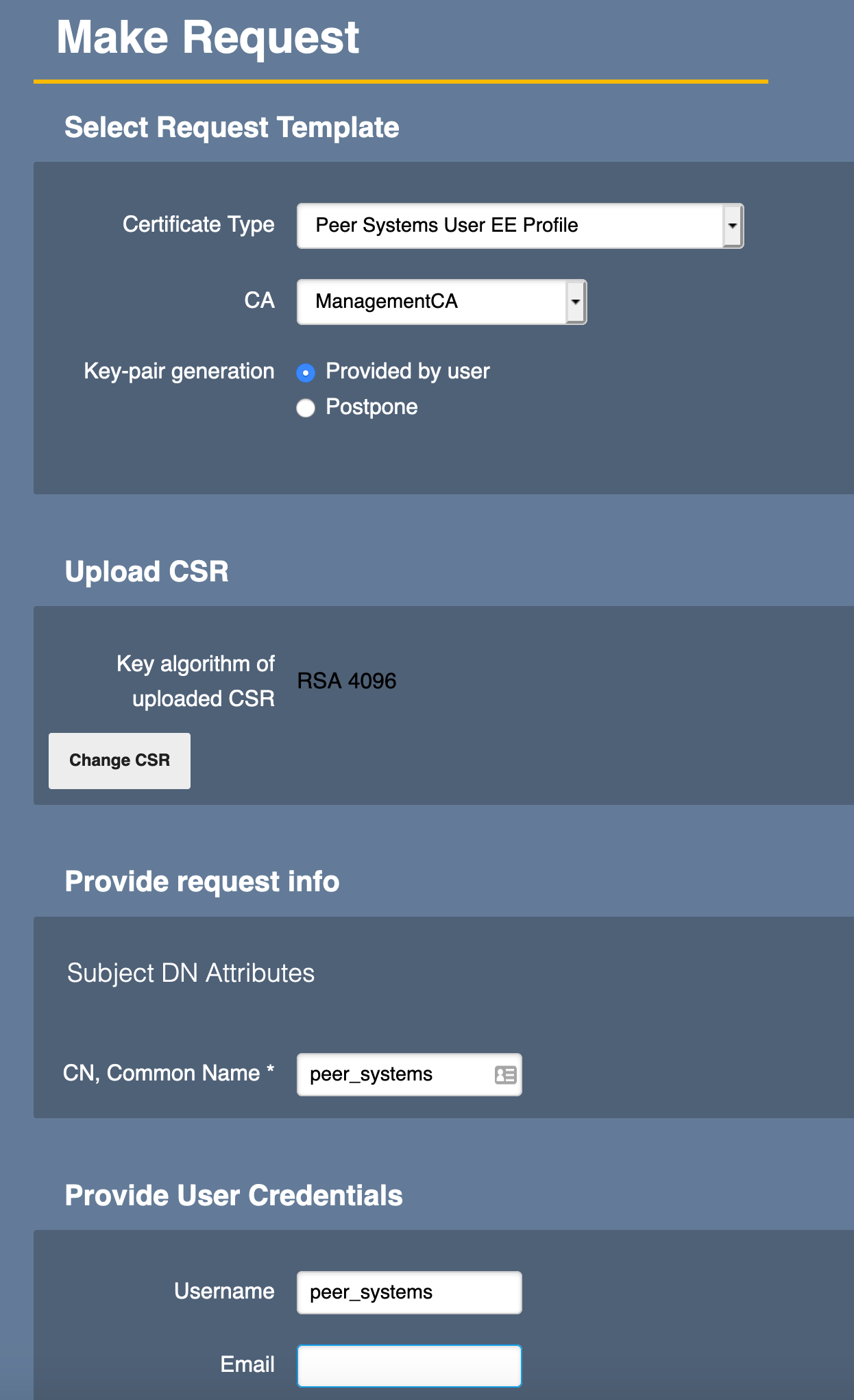
Click RA Web on the left side navigation and open the CAs RA web. Select Make New Request.
- Select Certificate Type: "Peer Systems User EE Profile"
- CA: "ManagementCA".
- Click Browse and select the "Peer System Key Binding to RA.pkcs10.pem" file.
- Change CN, Common Name to "peersystems".
- Change the Username to be the "peersystems"
- Click Download PEM.
- Save the file (peersystems.pem).
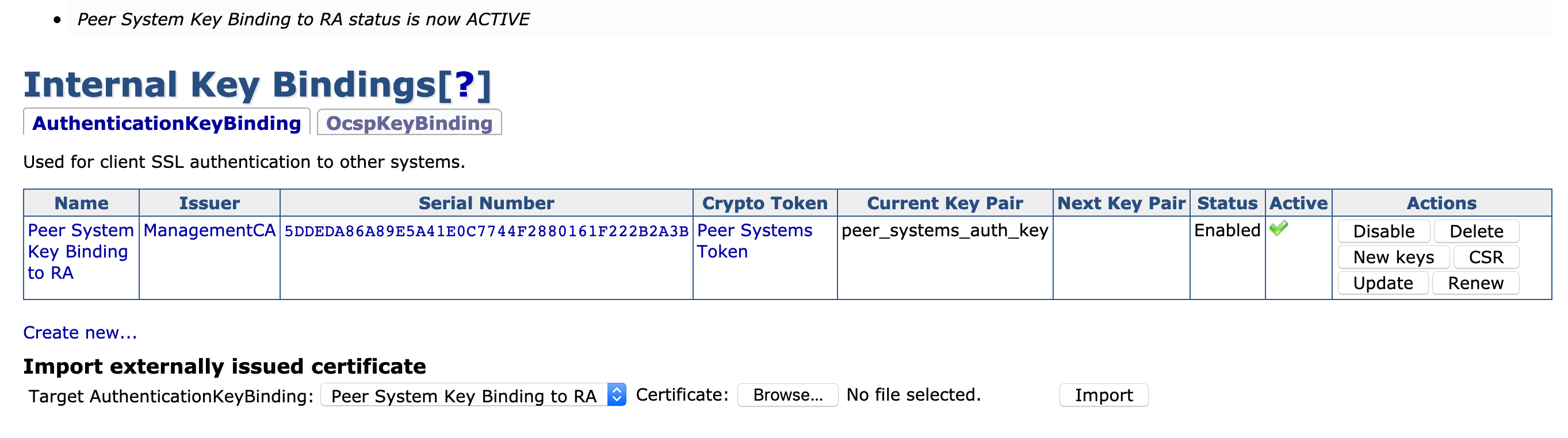
Step 5: Import Peer Systems certificate into Authentication Key Binding on CA
- Choose System Functions > Internal Key Bindings.
- Click the AuthenticationKeyBinding tab.
- Under Import externally issued certificate:
- Target AuthenticationKeyBinding: Peer System Key Binding to RA.
- Click Browse.
- Select the
peersystems.pemfile. - Click Import.
- Under Action:
- Click Enable.
- The Peer Systems Authentication Key Binding should now be Active.
Setup Peer Systems
Follow the steps below to setup Peer Systems:
Step 1: On the CA
- Choose System Functions > Peer Systems.
- Under Outgoing Peer Connectors, click Add.
- For Create Peer Connector, specify the following:
- Name: Peer Connection to RA
- URL: This should be the internal FQDN of the RA. For this example: "https://10.4.0.4/ejbca/peer/v1"
EJBCA Cloud Uses Apache and no port designation is necessary.
- In the Authentication Key Binding list menu, select Peer System Key Binding to RA.
- Select Enabled.
- Select Process Incoming Requests.
- Change Maximum parallel requests to 50.
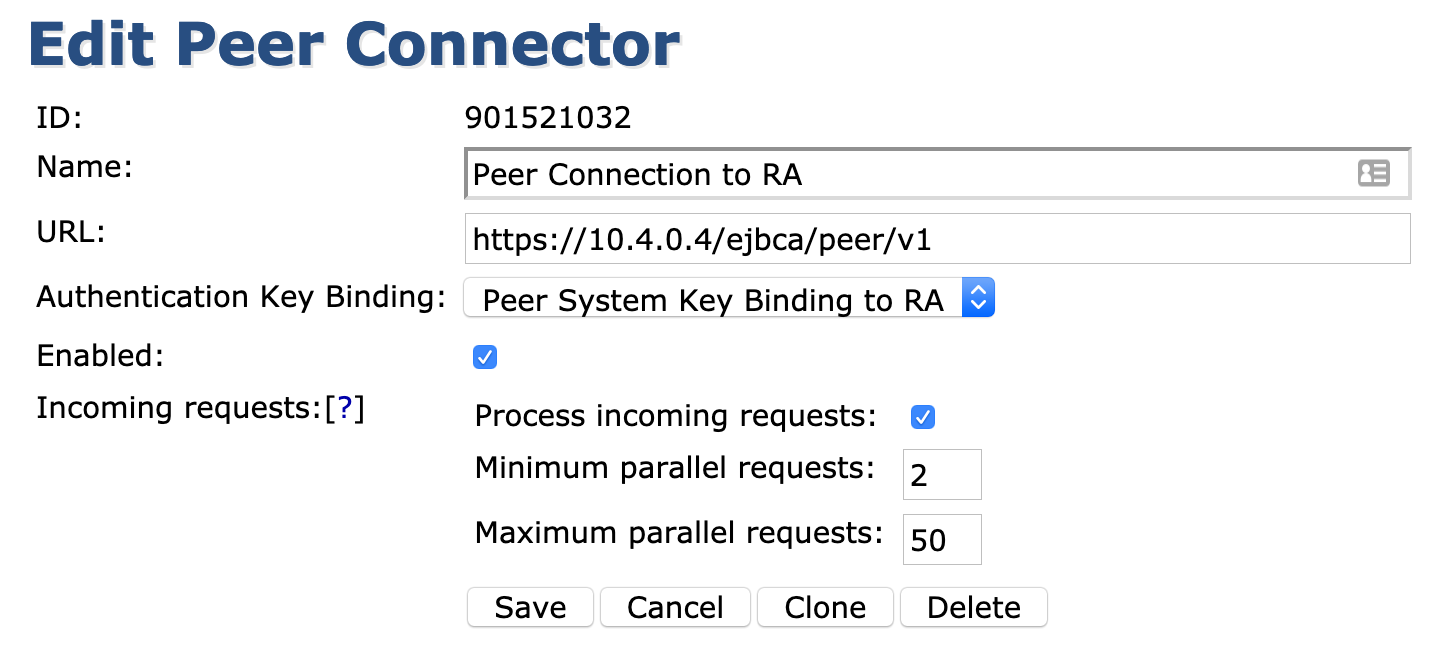
- Click Create.
- Click Ping. You should see the error Unable to connect to peer. Unauthorized
If the error Unable to connect to peer displays, this means you instances cannot communicate. Please check your VPN connection.
Also, make sure that the internal IP address is used and not an FQDN or external IP unless you have internal name resolution across vNets.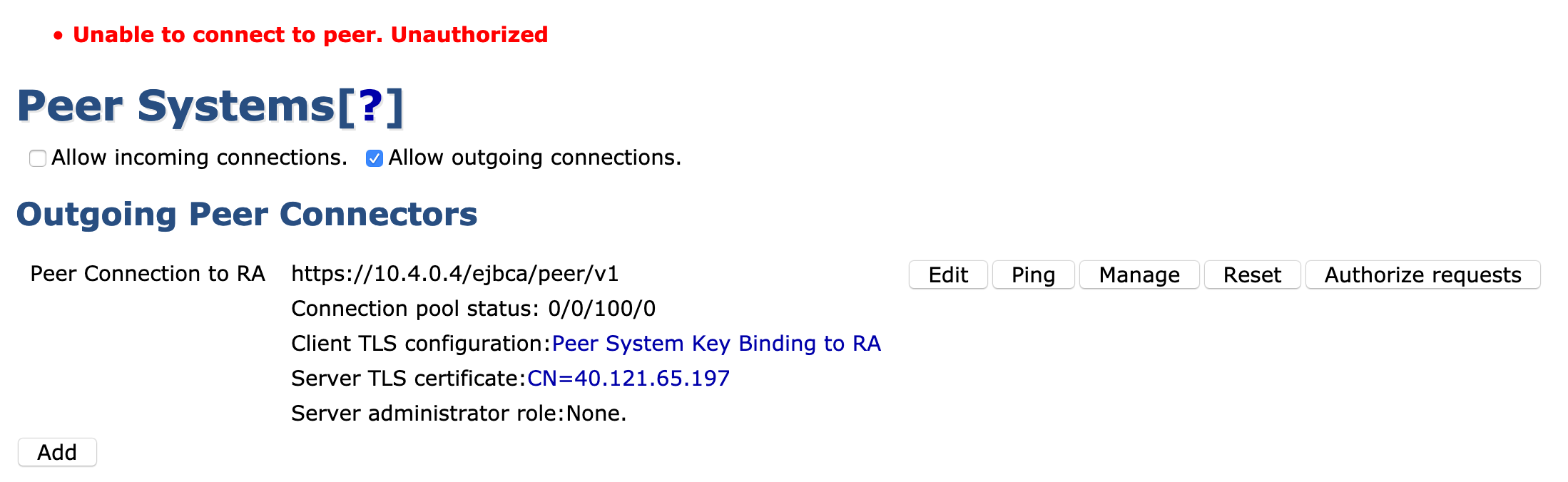
Step 2: On the RA
- Choose System Functions > Peer Systems.
- You should see a connection attempt from the CA under Incoming Connections.
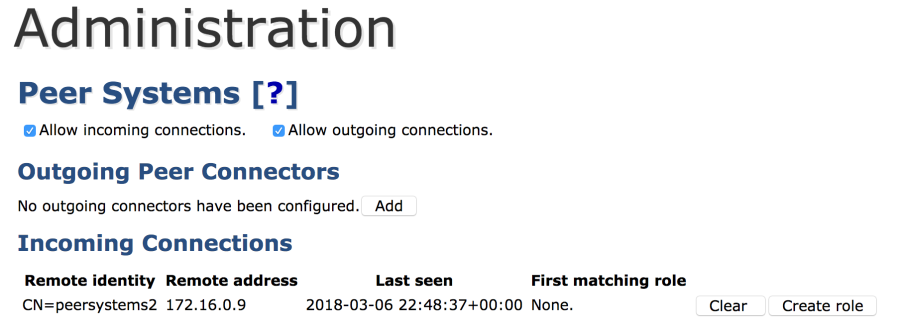
- Click Create Role.
- Ensure that Create new role is selected, and click Select.
- Additional properties will show. Change the Role name to "External RA Role".
- Ensure that Role is intended for peer connections is selected.
- Select Accept Long Hanging Connections.
- Select Access ManagementCA and any other CAs the RA needs to access.
- Select Publish Certificate.
- Select Compare certificate synchronization status.
- Click Create new role.
Step 3: On the CA
- Select System Functions > Peer Systems.
- Click Authorize Requests.
If you do not see the Create Role option, ensure Process incoming requests is selected in the peer connector on the RA side.
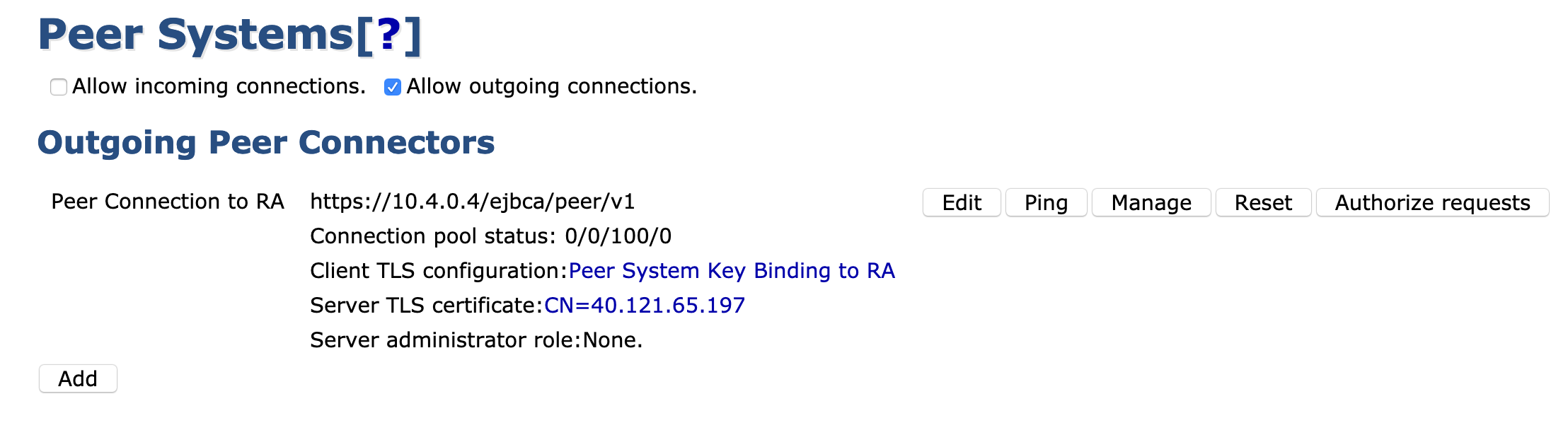
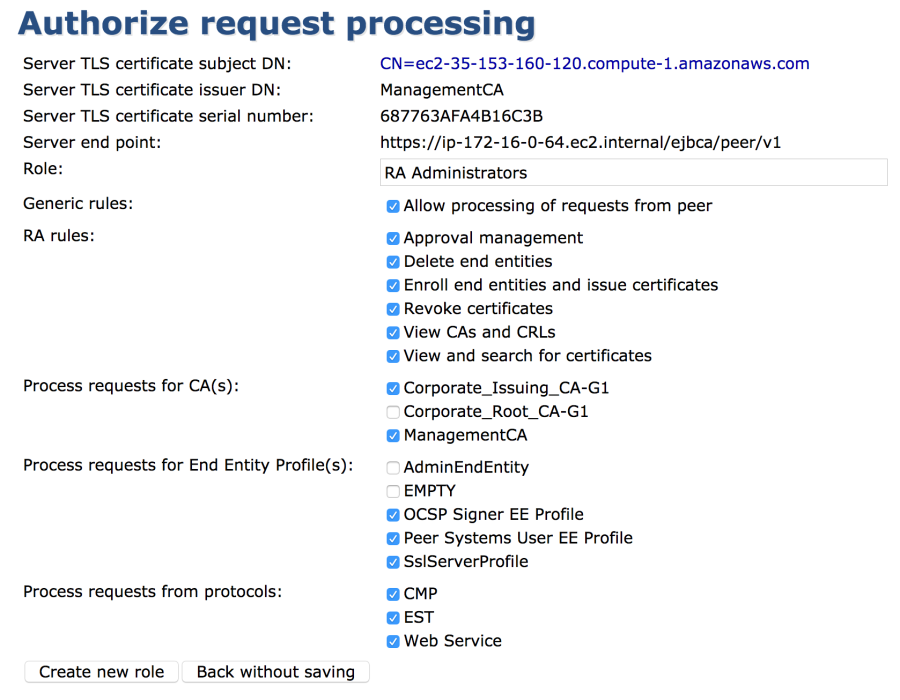
- Ensure that Create new role is selected and then click Select.
- Change the Role Name to something like "Peer role to 10.4.0.4 RA".
- Select the RA rules that apply to your environment based on the permissions needed for the RA and its administrators to have.
For a detailed explanation of RA Roles, see RA Administration. - Select which CAs the RA should handle requests for.
- Select the Profiles that the RA can use.
- Select the protocols that the RA can process requests from and click Create new role.
- Click Peer Systems.
Step 4. On the RA
Click Manage on the Peer Connection to RA peer connection.
Select Accept long hanging connections (this instance is an External RA polled by CA).
- Select the CAs you wish to have on the RA.
- Click Create new role.
- Access the RA Web on the RA server and the profiles you selected that exist on the CA should appear in the RA Web.