Azure
Begin by starting two EJBCA Enterprise Cloud for Microsoft Azure instances. In this example we will have the following 2 nodes:
- Node 1 - CA using IP 10.2.0.4 – WestUS – 10.2.0.0/16 address space
- Node 2 - RA using IP 10.4.0.4 – EastUS – 10.4.0.0/16 address space
One of the nodes is in WestUS and the other in EastUS. For the purposes of this guide we are going to be using the instance ID from Node 1 as the password. You can obtain this from loading Azure Explorer or run the following command on the instance itself:
# curl -sH Metadata:true "http://169.254.169.254/metadata/instance/network/interface/0/macAddress?api-version=2017-08-01&format=text"
CODE
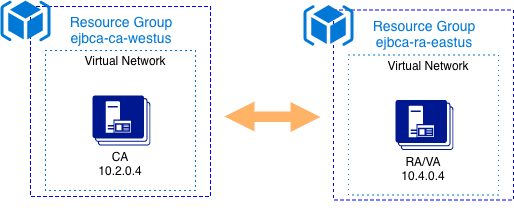
Virtual Network Configuration
To get the nodes to communicate, it is assumed a vNet-to-vNet VPN will need to be configured. This topic will be covered in the next section. For additional information, beyond whats covered in this guide, configuring a vNet-to-vNet VPN, refer to Azure's vNet-to-vNet Configuration Guide.
Optionally, for testing purposes, all nodes can be setup within the same Virtual Network. This is not ideal since it does not provide any availability guarantees if one of the Azure sites has an outage.
A network security group is also needed in each virtual network. That configuration will be outlined below since it pertains directly to the Galera communication.