Managing Truststores and Keystores
There may be times when users need to edit the truststore or TLS keystore of EJBCA SaaS deployments. Certificates and/or keys are supplied to update the truststore or TLS keystore of the EJBCA SaaS Deployment. These certificates and keys are used for EJBCA SaaS to communicate with other systems or devices. Use the TLS truststore feature if you would like this EJBCA deployment to trust an additional CA such as an Issuing CA.
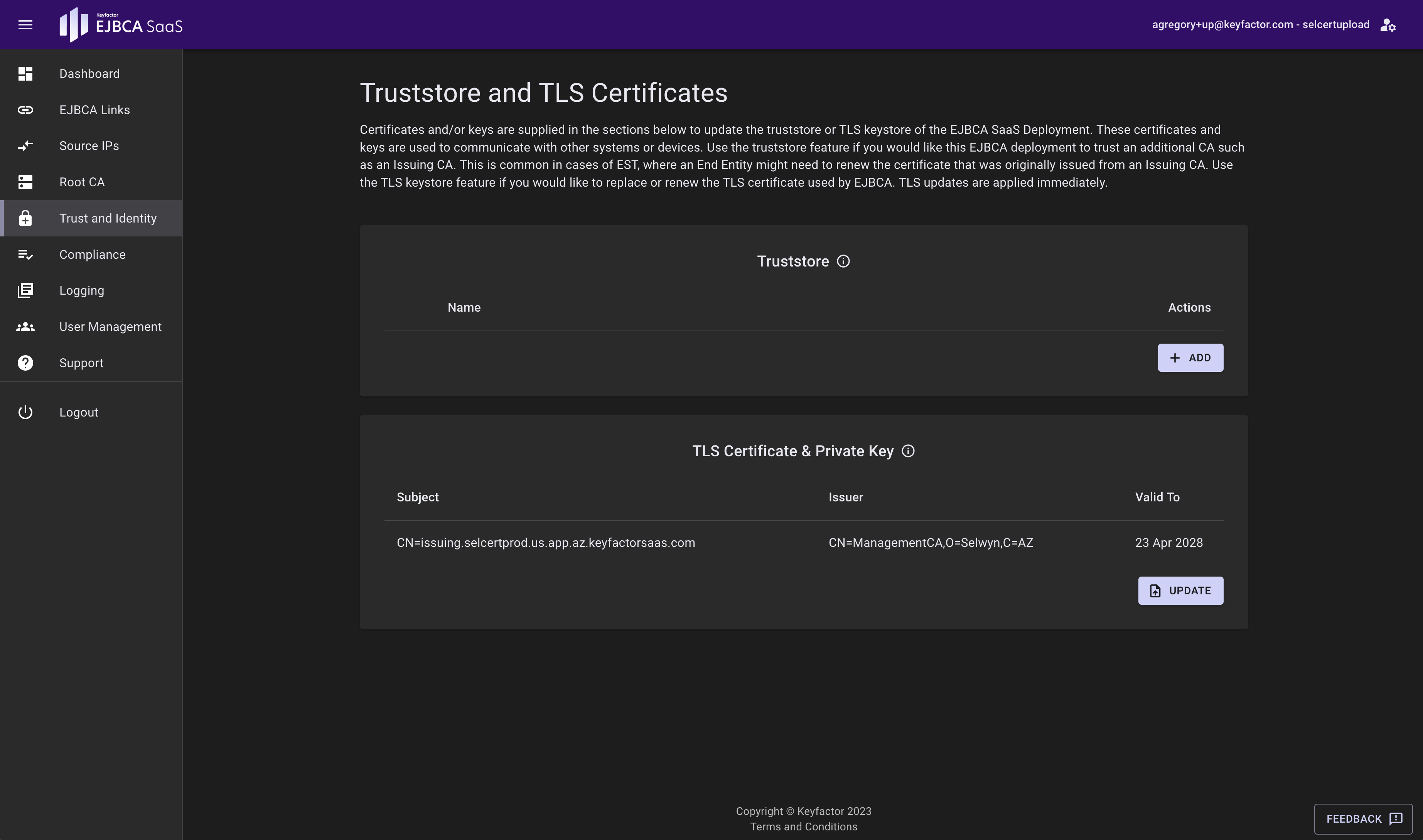
Truststore
The truststore contains the certificate authority certificates trusted by EJBCA. Updating the truststore here adds to the truststore in the deployment and does not replace the existing truststore that was provisioned with the system.
A typical use case is for EST, when an End Entity needs to renew a certificate issued previously via EST. For EST, the existing certificate is used to authenticate to the system and renew it. In order to do that, the Issuing CA's publicly trusted certificate chain needs to be added to the SaaS deployment's truststore. If EJBCA SaaS does not trust that CA certificate chain, TLS cannot be established and the renewal will fail.
Adding Certificates to the Truststore
When adding a truststore the full chain is required.
To add a certificate chain file to the EJBCA SaaS deployment, click the + ADD button. A dialog will appear asking for the Name of the truststore being added and a place to drag and drop the file into place, or click to browse to the file:
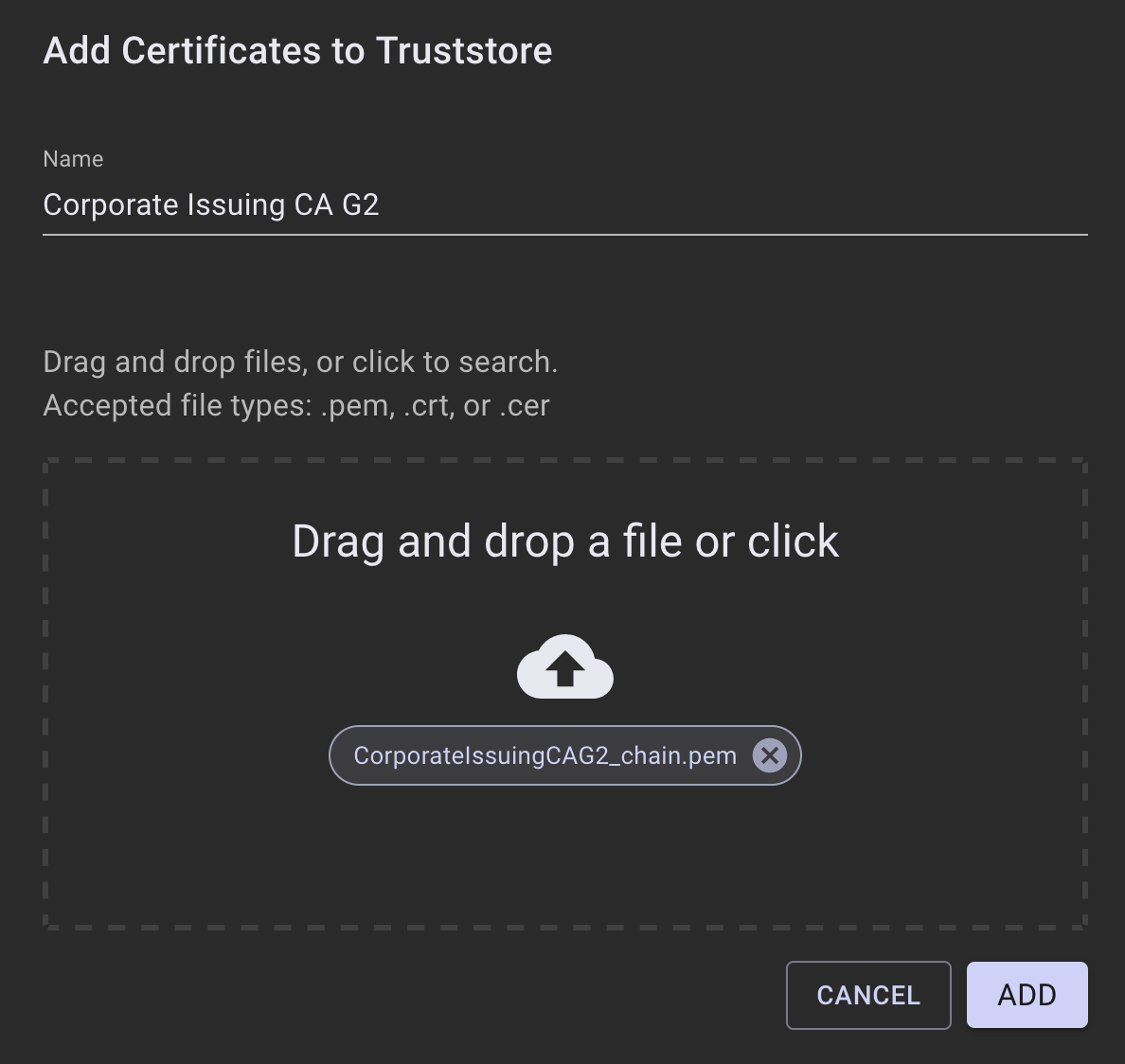
Click ADD to add them to the list of truststore additions. Repeat the process above for any other certificate chains that need to be added. A dialog at the top will indicate that there are unprocessed changes that need to be submitted and any added truststore certificates will appear in green.
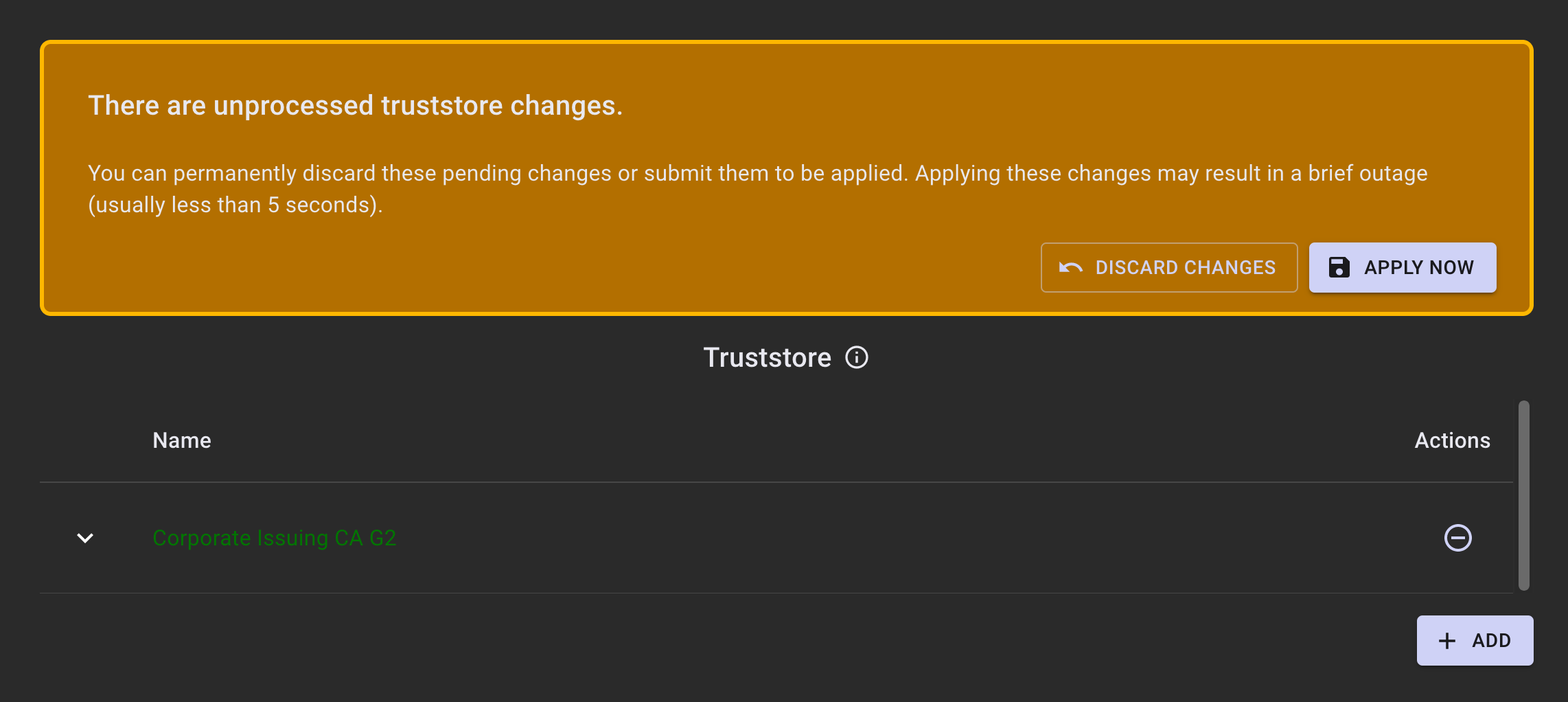
Once the changes are completed, click APPLY NOW. A notification will appear, indicating that the change is in progress.
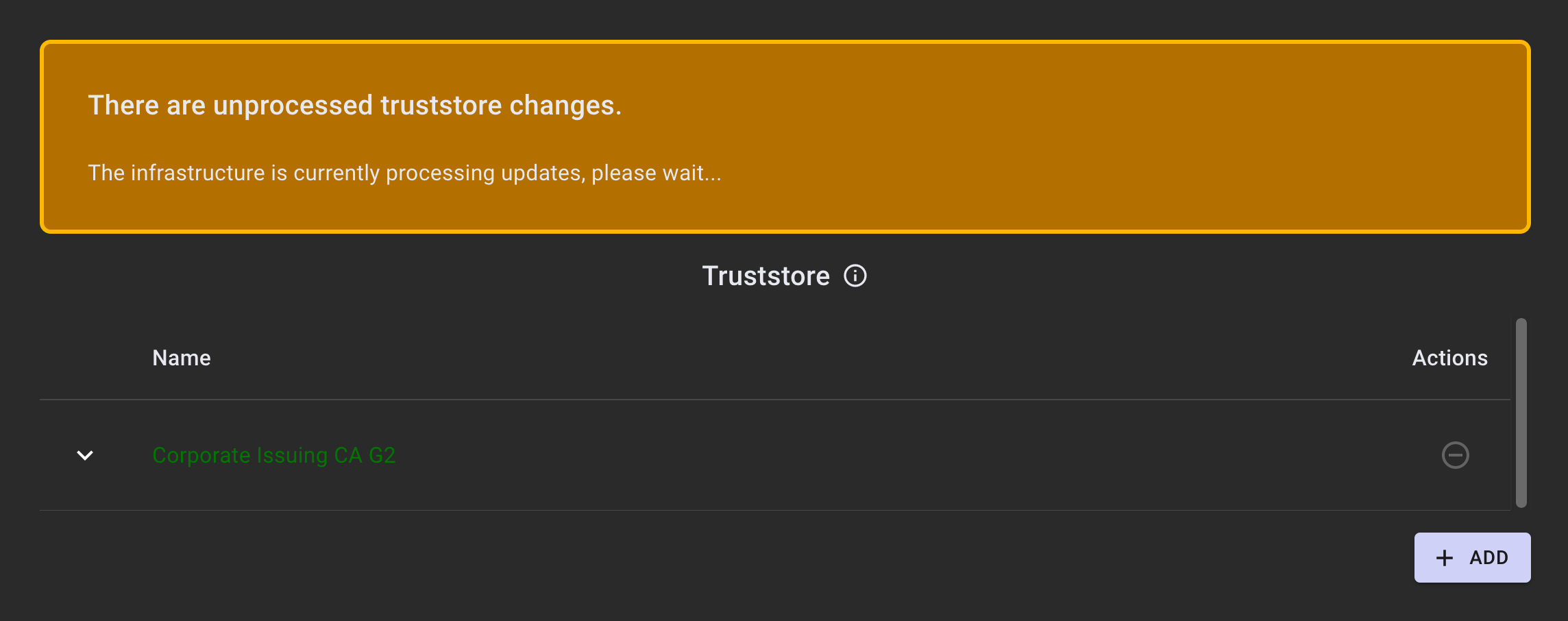
When the changes are complete, the entries in green will change back to white (black in light mode). To see the DN information in the certificates that were added, click the down arrow to expand them.
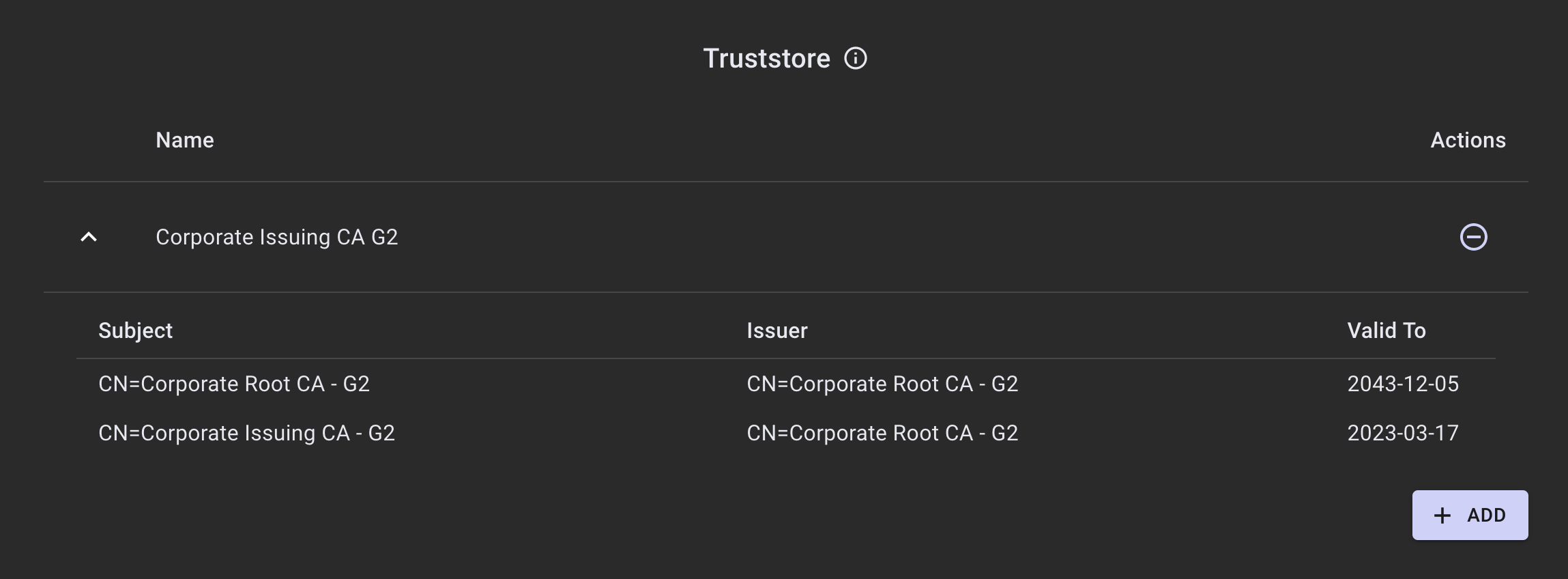
Removing Certificates from the Truststore
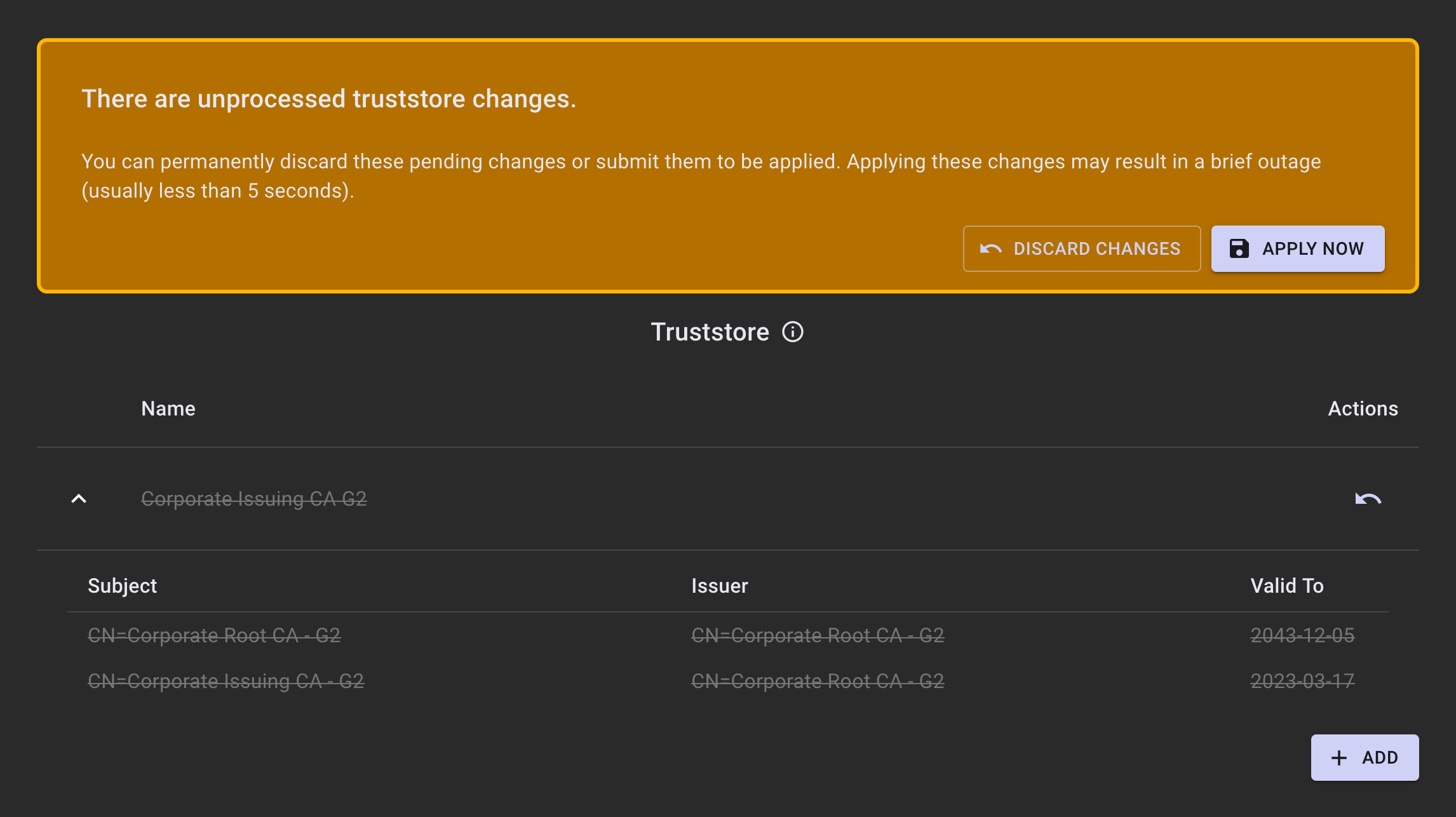
To remove a truststore entry, click the minus button on the row of the truststore entry you would like to remove. A banner will appear providing a notification that there are changes that are unprocessed. Click APPLY NOW to send them to the infrastructure for processing, or DISCARD CHANGES to remove them.
TLS Certificate and Private Key (aka Keystore)
Use the TLS keystore feature if you would like to replace or renew the TLS certificate used by EJBCA. TLS updates are applied immediately.
A keystore is used to store private keys and identity certificates that EJBCA SaaS should present for verification. This can be a CA certificate, key and issued certificate bundle. Please have the CA and issued certificate in a single chain file. TLS updates are applied immediately.
- Go to Search End Entities in the EJBCA Admin UI.
- In the Search end entity with username field, search for "apache".
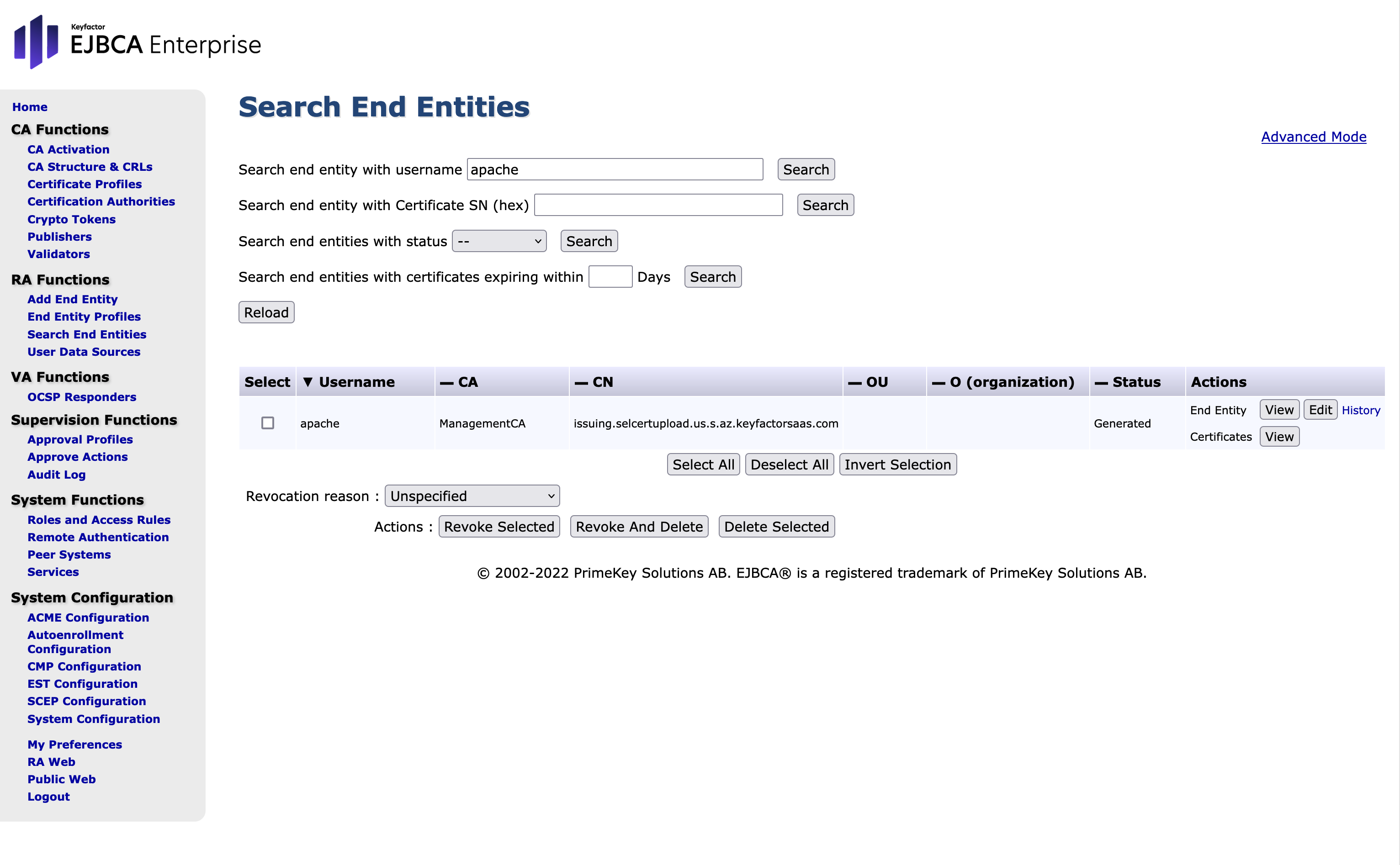
- Click Edit on the "apache" end entity.
- A dialog will pop up with the end entity details (please allow popups on this site if nothing appears). In the Status list, select New.
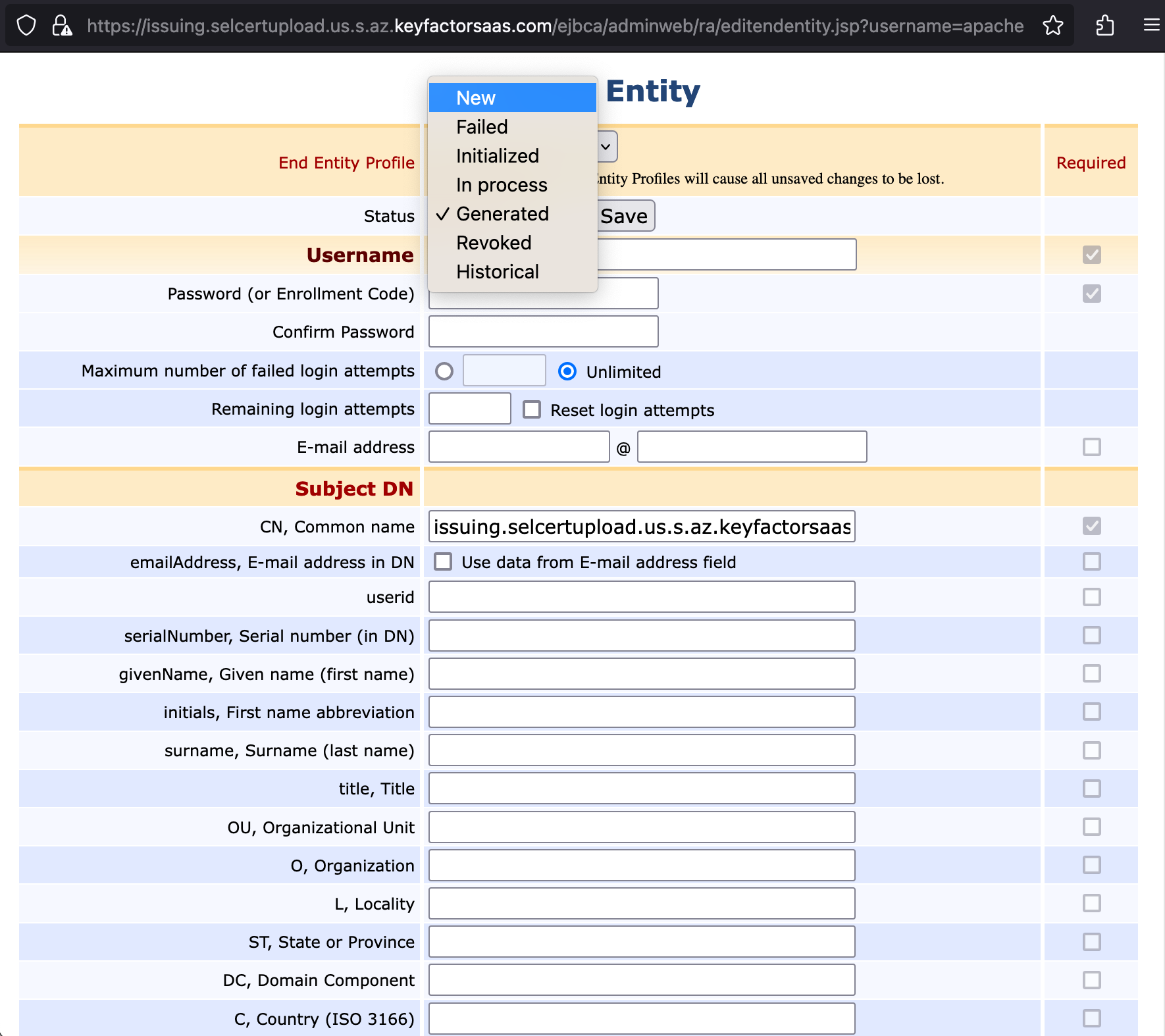
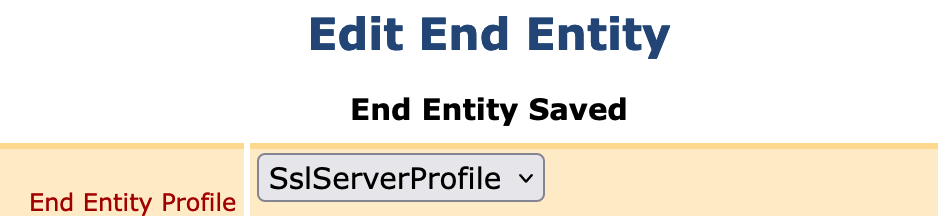
- Enter a password in the password and password confirmation fields.This will be the password used to retrieve the certificate in a later step. Click Save.
- A confirmation End Entity Saved will appear at the top. Close the end entity dialog.
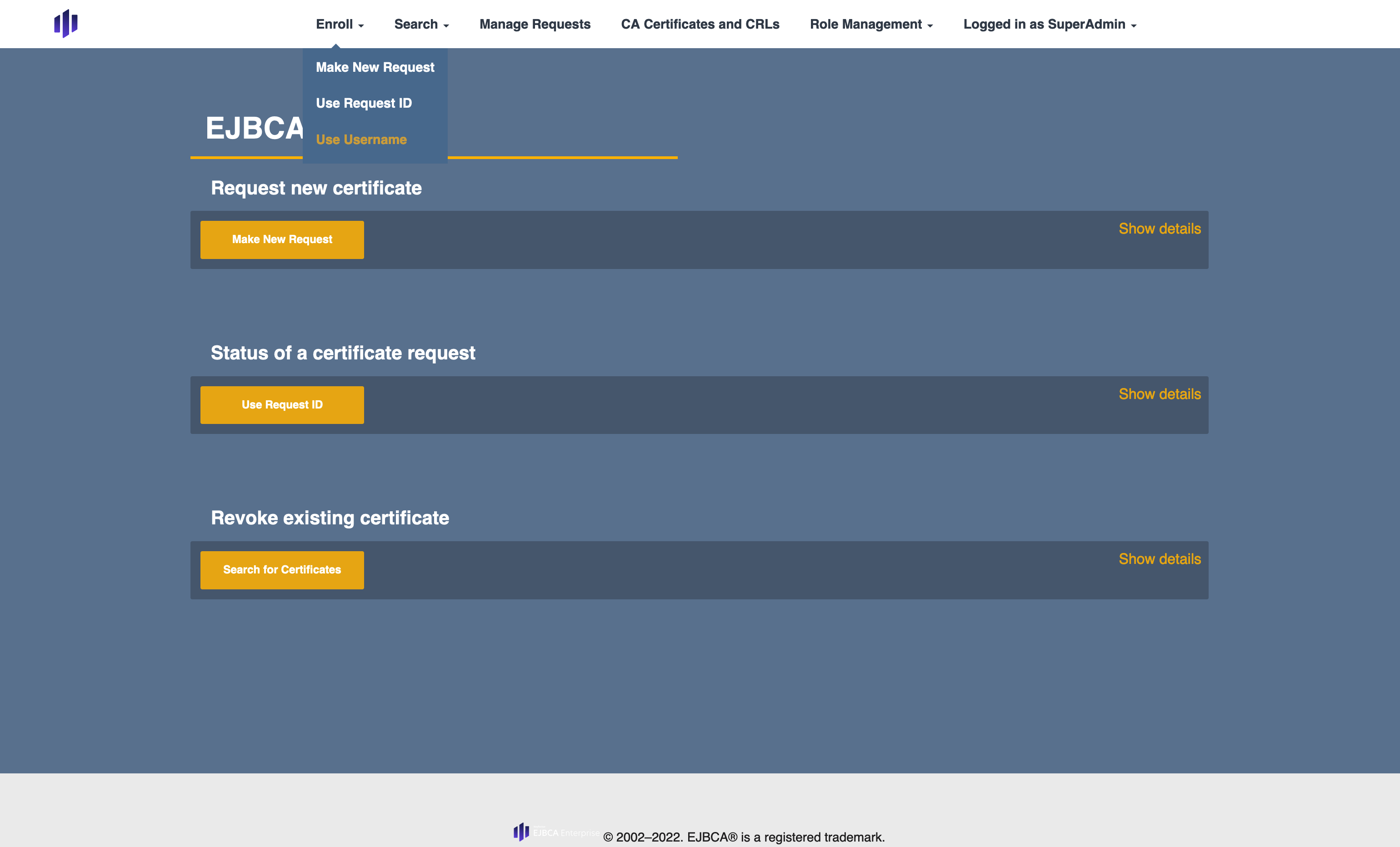
- Navigate to the RA web, in the Enroll list, select Use Username.
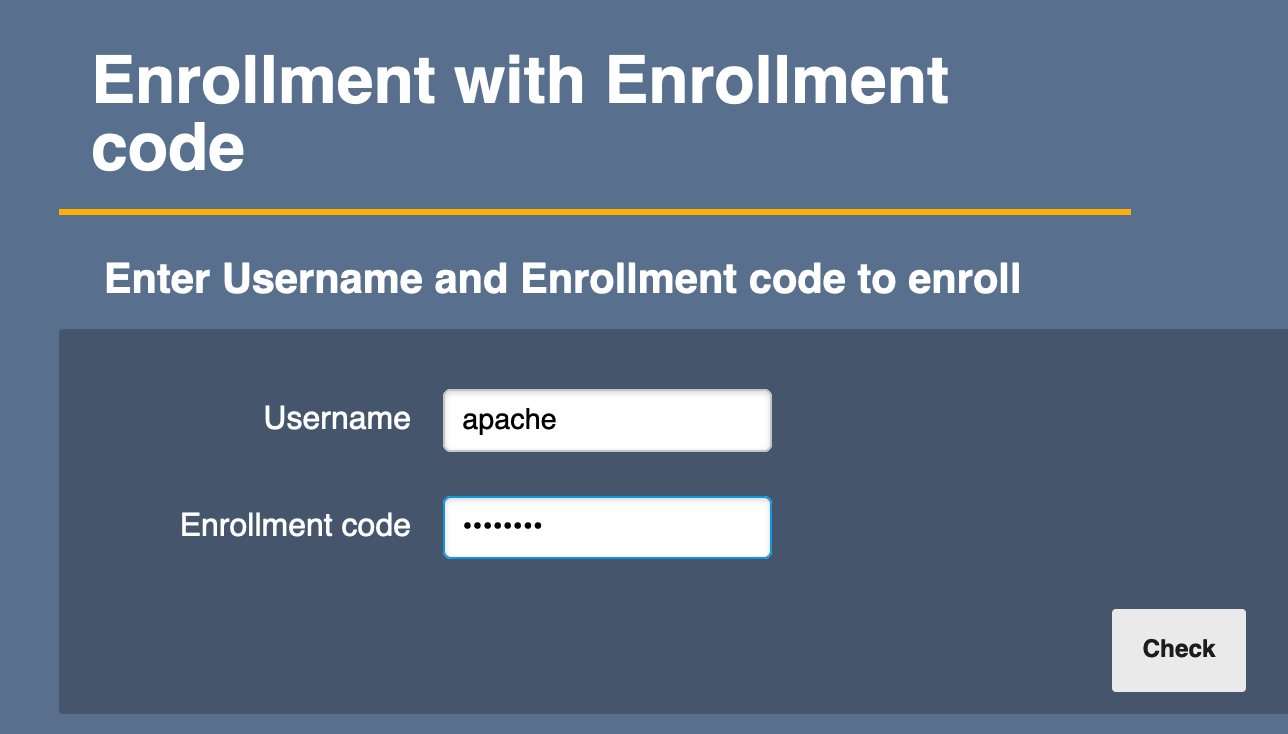
- For the Username, enter "apache", and for the Enrollment code, enter the password that was entered on step 5. Click Check.
- Select the desired Key algorithm and click Download PEM.
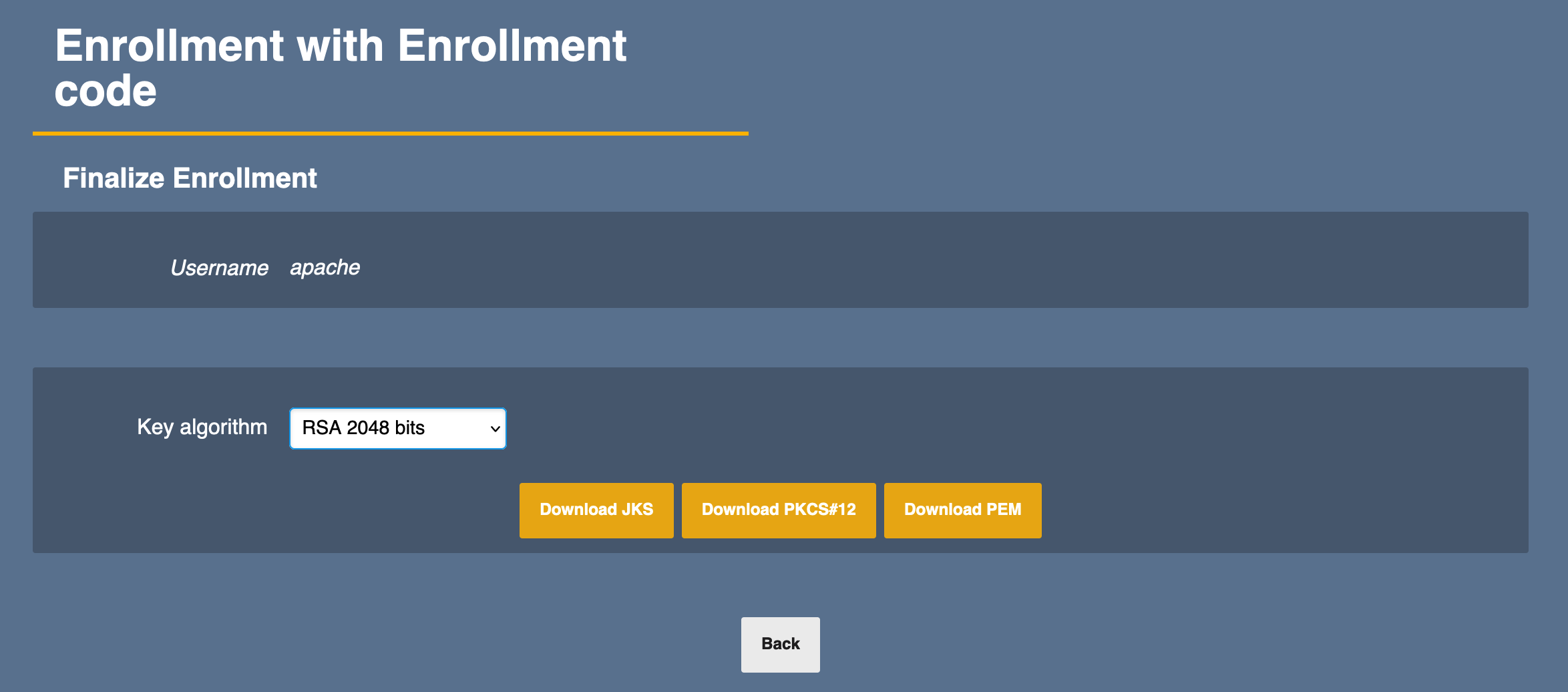
- A new PEM file will be downloaded to your local computer. Save this to a location so it can be edited.
- Open the PEM file in an editor and locate the Private Key lines.
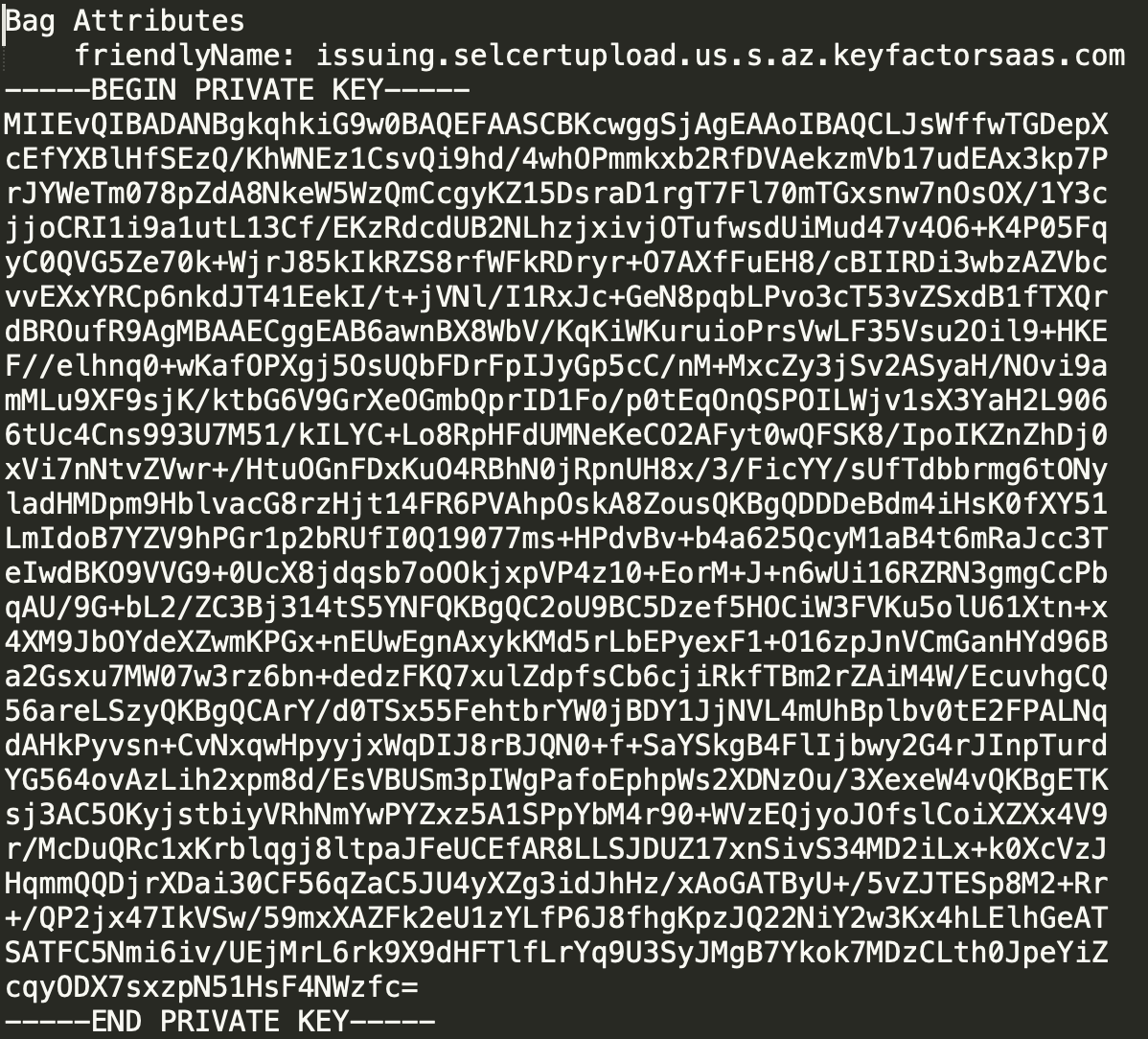
- Copy these lines to a new file that can be uploaded to the EJBCA SaaS Portal.
Once the private key is saved to a new file, remove it from the original file. Save the file without the private key.
If you are creating your own file for the certificate and issuer (chain) file, make sure the file is created with the issued certificate first and then the issuer certificate after. For example,
issuing.deployment.us.app.az.keyfactorsaas.com → chain.crt → combined.crt
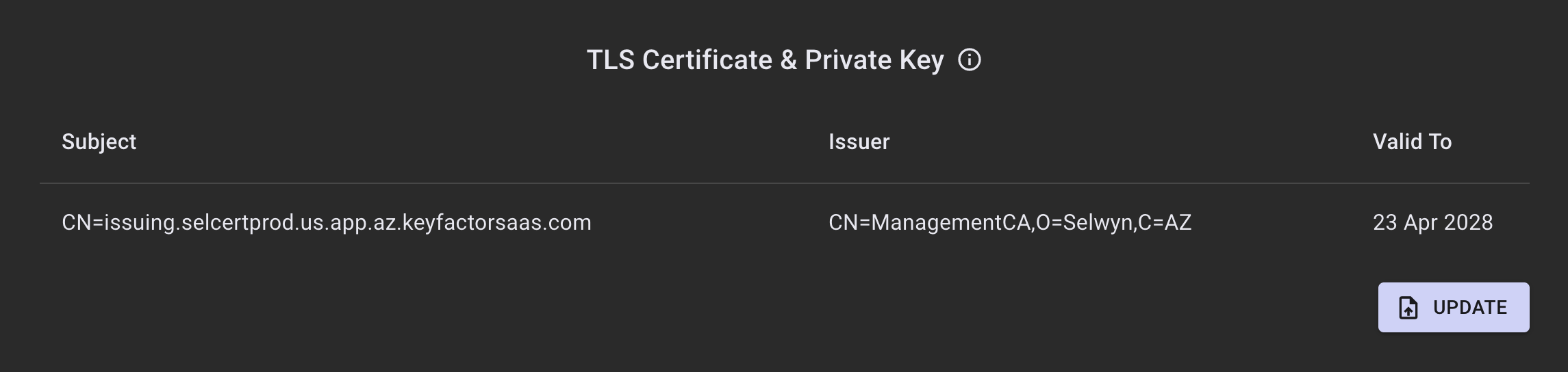
- Return to the EJBCA SaaS Portal. Navigate to the Trust and Identity pane and click UPDATE.
- A dialog appears that allows the two files just created to be uploaded. Browse or drag and drop each of these files. If the files validate correctly, the SUBMIT button will enable.
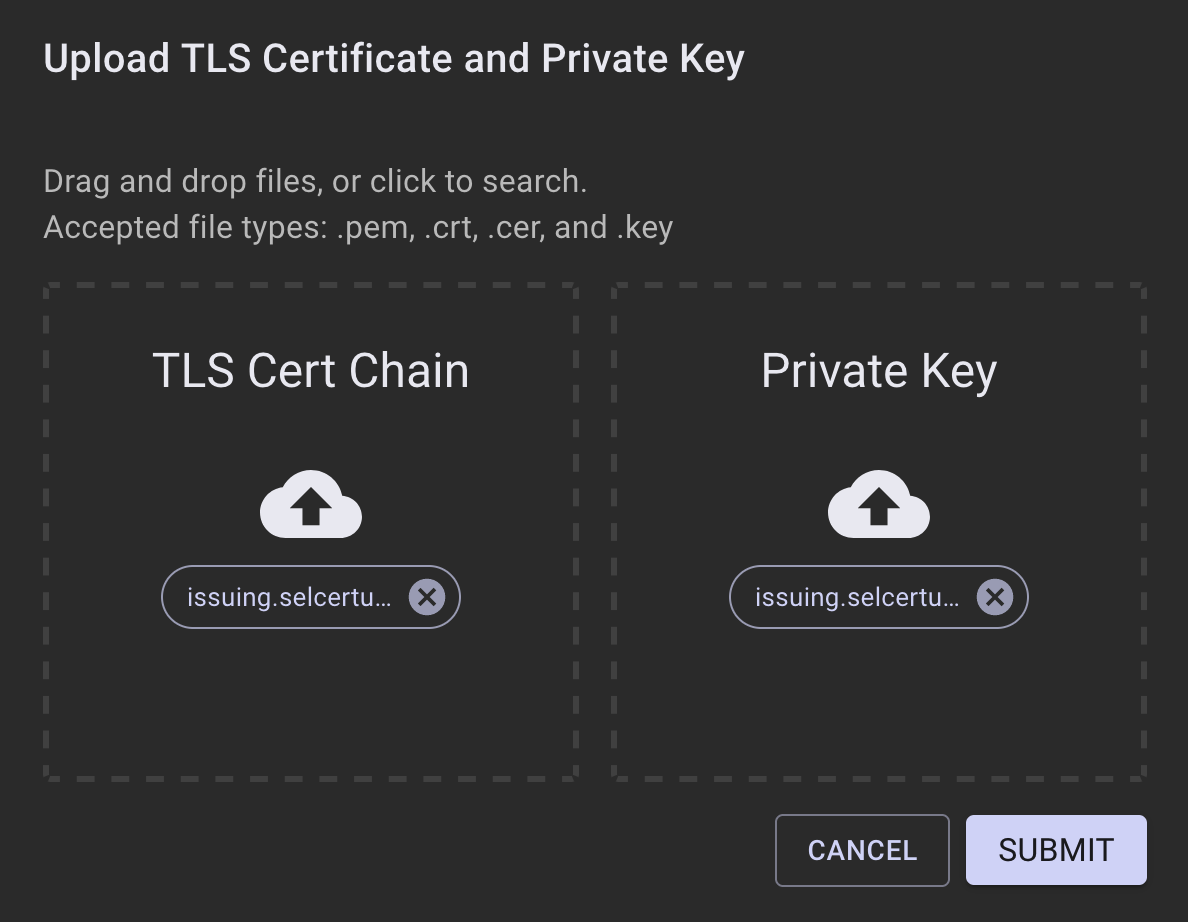
Click Submit.
There will be a brief outage while the deployment restarts to put the newly generated certificate into production
- Refresh the EJBCA Admin Web or RA Web and check to ensure that the certificate was replaced.