EJBCA and Cisco IOS
Cisco IOS uses SCEP to enroll and retrieve certificates for EJBCA. The following provides some basic information and tips that have been submitted to us by users over the years.
Configure Cisco IOS and EJBCA
Compatibility Notes
Cisco IOS has some minor eccentricities when interacting with EJBCA. Keep the following in mind when configuring Cisco IOS:
- The key and trustpoint must match the CA name, and Cisco does not allow spaces.
- The key must be created manually. For whatever reason enrolling with auto-generated keys fails.
Cisco Configuration
The following displays the Cisco configuration.
conf t
crypto key generate rsa exportable general-keys modulus 2048 label <Sub_CA_Name>
crypto pki trustpoint <Sub_CA_Name>
enrollment url http://<EJBCA_FQDN>:80/ejbca/publicweb/apply/scep
serial-number none
ip-address none
subject-name CN=<Device_FQDNH>
subject-alt-name <Device_FQDN>
revocation-check none
source interface Vlan#
rsakeypair <Sub_CA_Name> 2048 2048
exit
cry pki auth <Sub_CA_Name>
yes
cry pki enr <Sub_CA_Name>
<password>
<password>
yes
end
show crypto pki certificate verbose <Sub_CA_Name>
<treat this like a pause to ensure certificate is registered>
show crypto pki certificate verbose <Sub_CA_Name>
wr mem
conf t
ip http secure-trustpoint <Sub_CA_Name>
end
wr memThese commands were tested on WLC2504, WLC3504, WLC9800, 2960x, 3650, 3850, 9200, 9300, 9300X.
EJBCA Configuration
The following sections cover the EJBCA configuration.
End Entity Profile Configuration
To configure End Entity Profiles in EJBCA, go to RA Functions > End Entity Profiles. For more information, see End Entity Profile Operations.
The Subject DN fields must match what the Cisco device is configured to send. Cisco IOS requires the subject DN attributes to align exactly with what it expects, thus only the following Subject DN fields should be allowed:
- Common Name or Serial Number
- unstructuredName, Domain Name (FQDN)
In addition, DNS Name and IP Adress Subject Alternative Name fields may be used.
Certificate Profile Configuration
To configure Certificate Profiles in EJBCA, go to CA Functions > Certificate Profiles. For more information, see Certificate Profile Operations.
When enrolling the IOS device with a server certificate (VPN server for example), a server certificate profile should be used. Normally both Client Authentication and Server Authentication are configured as Extended Key Usage.
CA Configuration
To configure CAs in EJBCA, go to CA Functions > Certification Authorities. For more information, see Certificate Authority Operations.
- LDAP DN Order may need to be cleared.
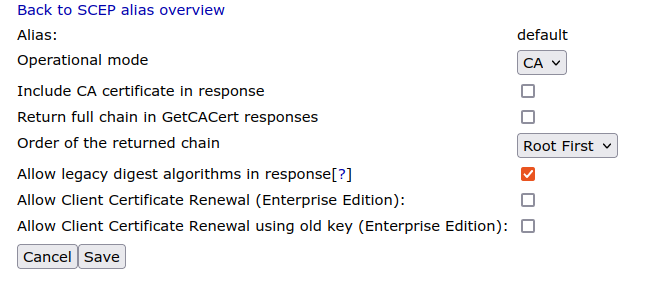
SCEP Alias Configuration
To configure SCEP in EJBCA, go to System Configuration > SCEP Configuration. For more information, see SCEP Operations Guide.
Cisco IOS does not expect the CA certificate to be part of the response, and thus the Include CA certificate in response option should be disabled in the SCEP alias configuration.
Also, Cisco IOS, at least up to and including 16.3.4, does not support using SHA256 in SCEP response messages, so Allow legacy digest algorithm in response must be selected to allow using SHA1 (even if the certificate is issued using SHA512WithRSA as the certificate signature algorithm).
Cisco IOS Simulator
Note that the instructions in this section have not been tested for some time, and may no longer be applicable.
There is a Cisco 7200 emulator called dynamips available and the graphical front-end GNS3, refer to GNS3 for more information.
The following describes how to configure and enroll directly with EJBCA using GNS3 on Ubuntu 8.10.
Install the packages:
sudo apt-get install gns3 uml-utilities bridge-utils Configure the host and gns3 to be able to communicate with each other, allowing the router to connect to EJBCA on the host computer.
Create a tap interface:
sudo tunctl -t tap0BASHRemove ip addressing and set eth0 and tap0 to promiscuous mode:
sudo ifconfig tap0 0.0.0.0 promisc up sudo ifconfig eth0 0.0.0.0 promisc upBASHCreate a new bridge interface:
sudo brctl addbr br0BASHAdd tap0 and eth0 to the bridge group:
sudo brctl addif br0 tap0 sudo brctl addif br0 eth0BASHEnable the bridge interface and give it an ip address:
sudo ifconfig br0 up sudo ifconfig br0 10.10.10.99/24BASHConfigure the default route:
sudo route add default gw 10.10.10.254CODE
Start gns3:
sudo gns3 Configure with IOS image, for example c7200-jk9s-mz.124-13b.bin (an image with crypto commands). Also configure a simple topology:
- drag cloud to topology window
- drag c7200 to topology window
- configure cloud and add tap0 interface
- add manual link from cloud to c7200
- start c7200
- open console on c7200
- enter configuration and configure FastEthernet0/0 with ip 10.10.10.98/255.255.255.0
Next, ping the host computer, where EJBCA is running.
To perform the actual enrollment as described above, use the following commands:
Router>enable
Router#configure terminal
Router(config)#
Router(config)#crypto ca trustpoint ScepCA
Router(ca-trustpoint)#enrollment url http://10.10.10.99:8080/ejbca/publicweb/apply/scep
Router(ca-trustpoint)#serial-number
Router(ca-trustpoint)#ip-address none
Router(ca-trustpoint)#subject-name OU=Network Management, O=PrimeKey Solutions AB, C=SE
Router(ca-trustpoint)#revocation-check none
Router(ca-trustpoint)#exit
Router(config)#crypto ca authenticate ScepCA
Router(config)#crypto ca enroll ScepCA Check the log for the username of the user you must create, create end entity profile and user with DN containing SN=FFFFFF and unstructuredName=Router, as seen in the log file (FFFFFF and Router are the default values in the simulator).
Router(config)#crypto ca enroll ScepCA
Router(config)#exit
Router#show crypto ca certificateTo look at the defined trust points, use the following command:
Router#show crypto ca trustpointsIf you are enrolling towards an RA instead, issue the following commands. For more information on how to set up an external RA for SCEP, see SCEP.
Router>enable
Router#configure terminal
Router(config)#
Router(config)#crypto ca trustpoint ScepRA
Router(ca-trustpoint)#enrollment url http://10.10.10.99:8080/scepraserver/scep
Router(ca-trustpoint)#enrollment mode ra
Router(ca-trustpoint)#serial-number
Router(ca-trustpoint)#ip-address none
Router(ca-trustpoint)#subject-name OU=Network Management, O=PrimeKey Solutions AB, C=SE
Router(ca-trustpoint)#revocation-check none
Router(ca-trustpoint)#exit
Router(config)#crypto ca authenticate ScepRA
Router(config)#crypto ca enroll ScepRANote that this is only applicable for EJBCA 3.8.1 and later and may generate the following error in Cisco:
Router#debug crypto pki API
Router#debug crypto pki messages
Router#debug crypto pki server
Router#debug crypto pki transactions
Router#debug crypto pki validation
...
*Jan 16 21:47:32.546: CRYPTO_PKI: make trustedCerts list for ScepRA
*Jan 16 21:47:32.550: CRYPTO_PKI: subject="c=SE,o=Foo,cn=Scep RA" serial number= 3A 46 2F B4 5B AC 06 47
*Jan 16 21:47:32.554: CRYPTO_PKI: subject="c=SE,o=EJBCA Sample,cn=ScepCA" serial number= 19 A6 7D 78 AF 9D 3B 27
*Jan 16 21:47:32.566: E ../cert-c/source/p7digdat.c(377) : Error #703h
*Jan 16 21:47:32.566: E ../cert-c/source/p7spprt.c(589) : Error #703h
*Jan 16 21:47:32.582: pkcs7 verify data returned status 0x703
*Jan 16 21:47:32.582: CRYPTO_PKI: status = 1795: failed to verify
*Jan 16 21:47:32.582: %PKI-6-CERTFAIL: Certificate enrollment failed.
*Jan 16 21:47:32.582: CRYPTO_PKI: All enrollment requests completed for trustpoint ScepRA.