Subject Name Log Redaction
Subject Name Log Redaction is useful for organizational compliance and for ensuring that specific data related to users is not logged, such as personal information.
As of EJBCA 8.1, you can configure EJBCA to not log Subject Distinguished Name (SubjectDN) and Subject Alternate Name (SAN) for configured end entities.
EJBCA supports extensive audit logging which may be configured to log events to files, databases, or custom devices. Additionally, EJBCA logs various information for debugging purposes similar to other software applications. Logging for both of these is redacted based on the configuration made.
Configure Log Redaction
To enable EJBCA to not log the SubjectDN and SAN of associated end entities and certificates, select the End Entity Profile option Redact Subject Name from logs under Other Data on the End Entity Profile page:

Limitations and recommended settings
For cases when the End Entity Profile is not known, administrators can enable Redact Subject Name from logs under System Configuration>Basic Configurations on EJBCA node or instance level to:
- Redact Subject Name when End Entity Profile data is unavailable
- Always redact Subject Name irrespective of End Entity Profile settings
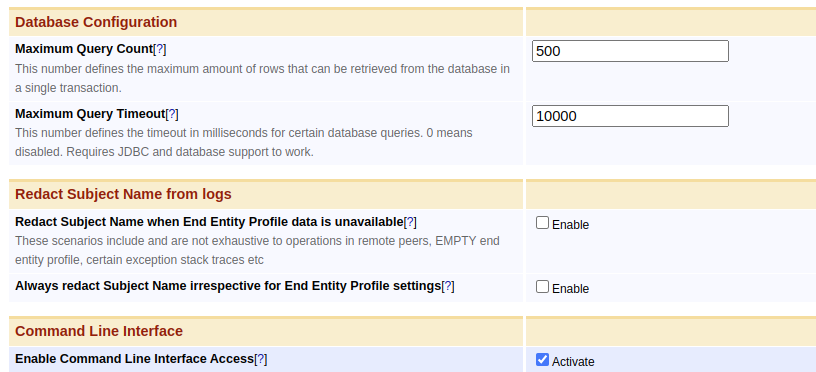
Administrators are recommended to use these settings when redaction is desired. The CA nodes may be set to redact subject names when End Entity Profile information is unavailable, while remote peers may always redact since they lack End Entity Profiles.
Scope and Limitations
In addition to Subject Distinguished Name (SubjectDN) and Subject Alternate Name (SubjectAltName), Certificate Signing Request (CSR) and certificates are redacted since the subject names can be easily recovered from them.
The following is redacted when configured:
- Subject Distinguished Name (SubjectDN)
- Subject Alternate Name (SubjectAltName)
- Certificate Signing Request (CSR)
- Certificates
The following which may contain subject names partially or completely, are considered out of scope and are not redacted:
- End entity or user name
- Pre-certificates are always audit-logged when certificate transparency is enabled
- Usernames extracted and/or derived from CSR from the requested SubjectDN for protocols like EST, CMP, or SCEP
- Email of an End Entity
- Request sender IP address in OCSP
customLogSoap API is considered trusted and may log any arbitrary message
Also note that the scope of redaction is only limited to "org.ejbca", "org.cesecore", and "com.keyfactor" packages. Other libraries such as JBoss ("org.jboss") or Hibernate ("org.hibernate") are known to log the whole request content or database transactions often even at INFO level. They should be explicitly turned off or limited to WARN level.
Logs from other libraries should also be disabled or limited. The following lists libraries and packages known to log sensitive content. Note that the list is non-exhaustive.
- org.jboss
- org.hibernate
- org.xnio
- org.apache (org.apache.cxf.phase.PhaseInterceptorChain → logs SOAP exceptions at INFO level)
- org.infinispan
Ensure the standalone.xml file is properly configured to stop unintended loggings in case of standalone server deployments. In case of container deployment, "LOG_LEVEL_SERVER_SUBSYSTEMS" is recommended to be configured at the default WARN level when log redaction is intended.