Azure Blob Storage Publisher
ENTERPRISE This is an EJBCA Enterprise feature.
The Azure Blob Storage publisher stores certificates and CRLs generated in EJBCA to an Azure Blob Storage space.
Prerequisites
Before configuring an Azure Blob Storage Publisher, you will need:
- An Azure Storage Account. This can be created in the Azure Portal under the Storage Accounts service, or using the Azure CLI with the command:
az storage account create --name STORAGE_ACCOUNT_NAME --resource-group RESOURCE_GROUP --location westus --sku Standard_LRS --allow-blob-public-access true - A blob container in the storage account. This can be created in the Azure Portal in the Storage Accounts service, or using Azure CLI with the command:
az storage container create --name CONTAINER_NAME --public-access blob --account-name STORAGE_ACCOUNT_NAME - A registered application that can write to the blob container. This can be created in the Azure Portal in the Microsoft Entra ID service, or using the Azure CLI with the command:
az ad sp create-for-rbac
You should note down the application ID, tenant ID and password for the registered application. - The registered application will need to have the Storage Blob Data Contributor Role assignment for the storage account created. This can be assigned in the Azure Portal under the "Access Control (IAM)" section of the Storage Accounts page for the storage account created above, or using the Azure CLI with the command:
az role assignment create --assignee OBJECT_ID --role "Storage Blob Data Contributor" --scope /subscriptions/SUBSCRIPTION_ID/resourceGroups/RESOURCE_GROUP/providers/Microsoft.Storage/storageAccounts/STORAGE_ACCOUNT_NAME
The OBJECT_ID is the ID of the registered application. It can be found using:az ad sp show --id APPLICATION_ID
The scope value can be found using:az storage account show --resource-group RESOURCE_GROUP --name STORAGE_ACCOUNT_NAME - The storage account you have created will make published files available at https://STORAGE_ACCOUNT_NAME.blob.core.windows.net/CONTAINER_NAME. To choose a different URL, consult the Azure documentation.
Configuration
To configure an Azure Blob Storage publisher to write to your Storage Account, do the following:
- Go to CA Functions > Publishers.
- Select the Azure Blob Storage publisher from the List of Publishers and click Edit Publisher.
- On the Edit Publisher page, select the Publisher Type AzureCrlPublisher (Custom Publisher).
- Specify the publisher settings (described in Azure CRL Publisher Settings below).
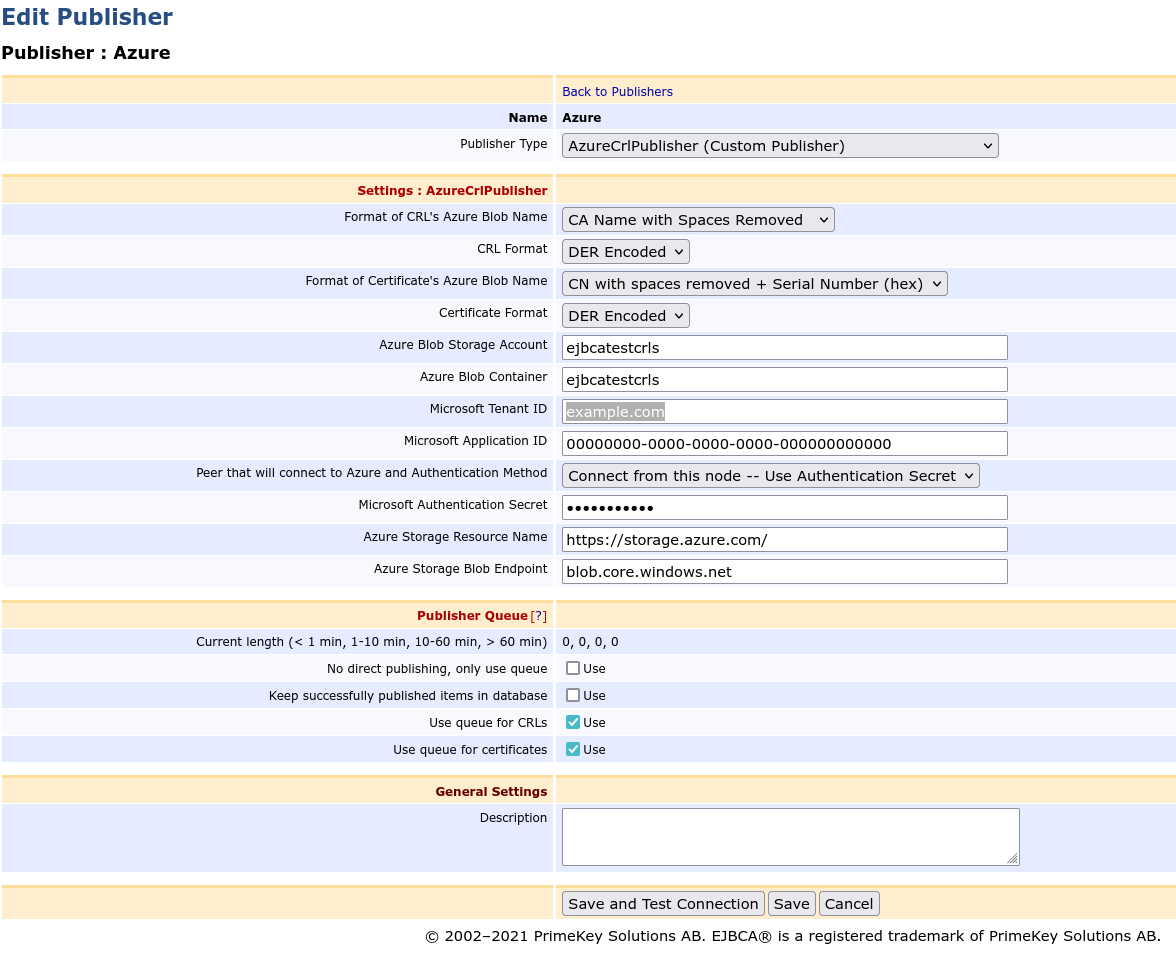
- Complete the remaining publisher settings (described in Publishers Overview).
- Click Save and Test Connection to perform input validation or click Save to store the configuration.
For more information on different publishers and their purposes, see Publishers Overview.
Azure CRL Publisher Settings
The following lists available Azure Blob Storage publisher (AzureCrlPublisher) settings.
Setting | Description |
|---|---|
Format of CRL's Azure Blob Name | Select how the name of the Azure Blob object will be formatted (EJBCA CA name with spaces removed, CA CN or OU if there is no CN, with the spaces removed, or CA SHA-1 Fingerprint as hex digits). |
CRL format | Select the encoding method for CRLs (DER or PEM). |
Format of Certificate's Azure Blob Name | Select how the name of the Azure Blob object will be formatted (CN with spaces removed, followed by the certificate serial number as hexadecimal digits, or the certificate's SHA-1 or SHA-256 fingerprint in hexadecimal digits). |
Certificate format | Select the encoding method for certificates (DER or PEM). |
Azure Blob Storage Account | Name chosen when the storage account was created. |
Azure Blob Container | Name of the Azure container in which the blobs will be created. |
Microsoft Tenant ID | The tenant ID for the Microsoft Azure subscription. This can be found in the Azure Portal under the Azure Active Directory section. |
Microsoft Application ID | This is the ID for an application registered with Azure Active Directory. |
Peer that will connect to Azure and Authentication Method | This list shows the peer names and key bindings available to use when connecting to Azure. For each peer, there is also an option to use Authentication Secret. If connections to Azure will be made from the CA, instead of a peer name, select one of the Connect from this node options. A key binding can be selected here if you are using Certificate to authenticate to Azure. The certificate for the chosen key binding should be added under the Certificates and Secrets section of the settings for the application identified by the Microsoft Application ID above. If using a shared secret instead of certificate authentication, the Microsoft Authentication Secret value will be used. |
Microsoft Authentication Secret | The shared secret value from the Certificates and Secrets properties for the application identified by the Microsoft Application ID above. This value is ignored if a key binding ID is chosen above. |
| Azure Storage Resource URL | The URL that Azure uses as a key when authenticating EJBCA's access to Azure Blob Storage. The default value is https://storage.azure.com/. |
| Azure Storage Blob Endpoint | The base URL, which when combined with the Azure Blob Storage Account ID above is the base address for CRLs and certificates stored by this publisher. The default Azure location is blob.core.windows.net. |
For more information on different publishers and their purposes, see Publishers Overview.
The Azure CRL Publisher is written for Azure Storage API version "2019-12-12".