EJBCA 8.2 Release Notes
DECEMBER 2023
The EJBCA team is pleased to announce the release of EJBCA 8.2. This release adds support for key archival and recovery in Microsoft auto-enrollment, RA chaining for hybrid deployments as well as HSM integration support for post-quantum certificate issuance. The release also includes various improvements and error corrections.
Deployment options include EJBCA Software Appliance, EJBCA Hardware Appliance, and EJBCA Cloud.
Highlights
Post-Quantum Certificate Issuance with HSM Support
EJBCA supports the Dilithium and Falcon NIST candidate post-quantum algorithms since EJBCA 8.0. EJBCA 8.2 now introduces support for the use of a hardware security module (HSM) with support for the Dilithium algorithm.
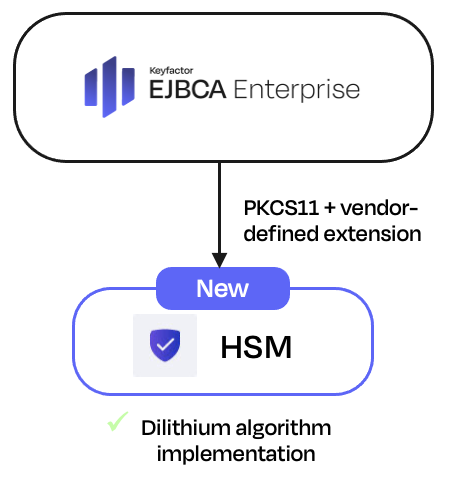
Since Dilithium is not part of the PKCS11 standard, it requires an HSM vendor-defined extension in the PKCS11 interface. For information about supported HSM vendors and models, contact Keyfactor.
Note that the Dilithium algorithm is suitable for non-production use only. NIST standardization is planned for completion in 2024 and the Dilithium algorithm can be used for proof-of-concept (PoC) and post-quantum transition preparation activities until then. For more information, see Post-quantum Cryptography Keys and Signatures.
Microsoft Auto-Enrollment Key Archival
EJBCA 8.2 introduces a new option in Microsoft auto-enrollment enabling administrators to configure key archival in the EJBCA setup for MSAE. Key archival is typically used in use cases like certificates for Encrypted File Systems (EFS) and encrypted e-mails using S/MIME certificates.
Key Archival can be enabled per end entity profile. For profiles with key archival enabled, the private keys corresponding to issued certificates will be encrypted and stored in EJBCA. If a private key is lost, EJBCA allows a CA administrator to recover the key for a user.
For information on how to set up EJBCA for key archival in Microsoft Auto-enrollment, refer to EJBCA Configuration.
RA Chaining
EJBCA 8.2 implements RA chaining support to enable zero trust hybrid and multi-cloud PKI deployments based on extended flexibility in distributed EJBCA deployments. The established EJBCA security model for separating the Registration Authority (RA) and Validation Authority (VA) from the Certificate Authority (CA) in EJBCA deployments is based on setting up mTLS-secured peer connections initiated from the CA to the RA and the VA. The associated network setup will normally not accept any incoming connections to the CA. Instead, all external communication is targeting the RA and VA and these communicate with the CA through the mTLS peer connections.
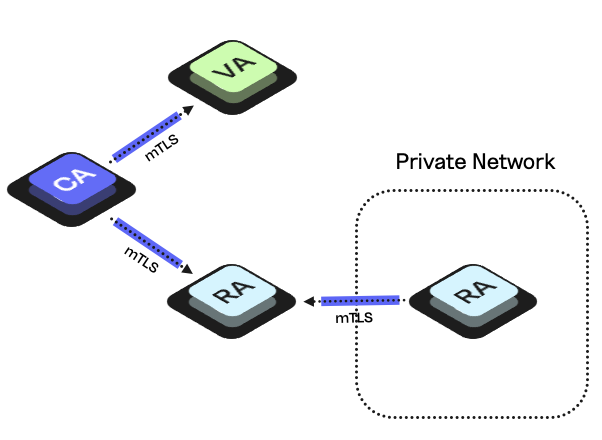
For certain deployment scenarios, customers want to deploy an EJBCA RA in a network environment that is set up not to accept incoming connections from where the EJBCA CA is deployed. The RA chaining feature is introduced to support such deployments. An RA chaining-based setup uses the same principles for the separation of CA, RA, and VA as described above. One or more additional RAs are then deployed in an external environment. These additional EJBCA RAs use outgoing mTLS-secured peer connections to an EJBCA RA traditionally connected to the EJBCA CA. For details on how to set up EJBCA instances in your PKI infrastructure as described above, see RA Chaining.
Announcements
Deprecation of DSA Algorithm
The use of the DSA algorithm in EJBCA is deprecated as of EJBCA 8.2. DSA algorithm support is scheduled to be removed in an upcoming release, and users are advised to use other algorithms in its place.
Upgrade Information
Review the EJBCA Upgrade Notes for important information about this release. For upgrade instructions and information on upgrade paths, see Upgrading EJBCA.
EJBCA 8.2 is included in EJBCA Software Appliance 2.5, EJBCA Hardware Appliance 3.13, and EJBCA Cloud 3.4.
Change Log: Resolved Issues
The following lists implemented features and fixed issues in EJBCA 8.2.
Issues Resolved in 8.2
Released December 2023
New Features
ECA-11720 - P11NG-CLI ability to list and delete data objects
ECA-11844 - Capability to issue CA Exchange Certificate via MSAE
ECA-11849 - Add Utimaco PKCS#11 R3 to defaultvalues.properties
ECA-11850 - Support AWS Service Roles for AWSKMS Crypto Tokens
ECA-11851 - Handle Key Exchange Token request / response from MSAE Servlet
ECA-11862 - Add dropdown in MSAE alias config for Exchange Certificate Profile
ECA-11863 - Add x509 extensions for MS Exchange Certificate to certificate profiles
ECA-11864 - Allow caller to customize whats checked in health checks
ECA-11876 - SOAP WS API: Support more fields when creating CAs
ECA-11883 - Background Service Renewing CA Exchange Certificate
ECA-11907 - Add keyusage flag to cryptotoken generatekey ability to modify attributes in p11ng-cli
ECA-11911 - Integrate MSAE key archival workflow with createCertficiateWs
ECA-11929 - Documentation for RA Chaining
ECA-11937 - Add keyusage flag to REST API generateKeyPair
ECA-11938 - Add p11 attribute override ability in p11ng-cli
Improvements
ECA-6415 - Searching for certificates in the RA web is slow
ECA-10698 - Inspect Certificate/CSR in RA UI
ECA-11613 - DER format CSR enrolment via REST API
ECA-11620 - Normalize the CMP Configuration page according to UX design conventions
ECA-11621 - Normalize the EST Configuration page according to UX design conventions
ECA-11622 - Normalize the SCEP Configuration page according to UX design conventions
ECA-11646 - Extended flexibility in CMP RA mode validation logic
ECA-11662 - Add a new REST endpoint to trigger Service workers
ECA-11798 - Improve handling of HSM connection timeouts
ECA-11804 - OCSP response pre-production during issuance/revocation
ECA-11846 - Peer publisher should always publish certificate contents for CA and OCSP certificates
ECA-11852 - Upgrade JackNJI11 to improve error handling in FindObjects and work with cloudHSM with more than 1024 key pairs
ECA-11882 - Create RA side cache for MSAE Key Exchange Certificate
ECA-11894 - Language update by David Carella
ECA-11913 - Exchange certificate DN should be based on issuers CN
ECA-11914 - Allow non-Bouncycastle keypairs to be recovered from SOAP APIs
ECA-11939 - Add a feature toggle presigned OCSP responses upon issuance & revocation generation
ECA-11943 - Force reload cached JS and CSS files when EJBCA version changes
ECA-11961 - Fix testRedactionPatterns test in CE
ECA-11984 - L10n: Add Document-Signing EKU in RA GUI (English)
Bug Fixes
ECA-10858 - EE profile change in RA web
ECA-11665 - Can not use PEM cert download in RA Web if key recovery is enabled
ECA-11729 - BE Publisher - we can add any property via REST
ECA-11818 - End Entity is being updated even when nothing was changed
ECA-11825 - NPE when trying to import CA certificate response when MS CA compatibility is enabled
ECA-11828 - IllegalStateException when starting EJBCA with MS CA compatibility enabled and cryptotoken auto-activation disabled
ECA-11842 - RA - only key algorithm section is visible
ECA-11847 - FE RA - unify fields in end entity.
ECA-11855 - FE PeerConnector - cancel works like save
ECA-11861 - Add/Remove buttons in EST View mode are clickable
ECA-11865 - Configdump import fails for /endentityprofilesrules/profileName/keyrecovery/
ECA-11871 - Restore ca.keyspec that was accidentally removed from install.properties.sample
ECA-11893 - ejbca-db-cli verify broken - no such provider BC
ECA-11896 - Regression: CrlStoreSessionBean.getLastCRLInfoLightWeight gives exception using Oracle Database
ECA-11905 - Allow non-Bouncycastle keypairs to be recovered from RA GUI
ECA-11915 - RA certificate search timeout returns "No results"
ECA-11916 - List of Vendor CAs in EST alias is not sorted
ECA-11925 - Edit CMP Alias page displays RA Name Generation Prefix/Postfix on Client Mode
ECA-11926 - Only KEC enabled certificate profiles must be shown in drop down in MSAE alias
ECA-11927 - AWX configdump import failure due to missing yaml key (should not be mandatory)
ECA-11946 - Relapsed - MSAE Alias - Removing template mapping always removes the top row
ECA-11954 - Fix missing ConfigDump default value for "Fortanix Base Address" in CryptoTokens
ECA-11955 - Fix NullPointerException in EjbcaWS method "createExternallySignedCa" when caProperties = null
ECA-11956 - Exception when trying to add an alias
ECA-11960 - Allow recovery for usergenerated tokens only if they are marked for recovery
ECA-11968 - isDeltaCrl flag in storeCrl in CertificateCrlReader is set incorrectly
ECA-11975 - Regression: Could not find key 'CMP_ALIAS/.extendedvalidation'
ECA-11977 - Log Redact ui bug in approvals for key recovery
ECA-11982 - Fix CMP alias UI - distorted vendor mode fields
ECA-11983 - RA Web Make New Request UI Bug
ECA-11986 - Make RA Web certificate search backwards compatible with older CA versions