Enable Syslog Log Streaming
EJBCA SaaS supports streaming logs to an external logging server. The following covers how to configure syslog log streaming of the Issuing and Root CA, HTTPd and EJBCA logs to remote syslog servers.
Overview
Any log management service that accepts syslog stream inputs over TCP may be used. EJBCA SaaS supports syslog log streaming over TCP or TLS (Authenticated or Unauthenticated).
- TCP logger: Since TCP connections are not encrypted, TCP should only be used for testing connectivity.
- TLS Unauthenticated Logger: TLS Unauthenticated logger configurations require a CA certificate (or trust store) to be uploaded via the portal, to perform server validation of the remote syslog server.
- TLS Authenticated Logger: TLS Authenticated loggers perform mutual TLS authentication and require a CA certificate (or trust store), client private key, and client certificate to be uploaded via the portal.
The certificates and private keys uploaded for logging are stored securely in the Secrets Manager.
For both Authenticated and Unauthenticated TLS, the TLS server certificate installed on the remote syslog server must include the FQDN or IP in the CN or dnsName SAN, depending on if the FQDN or IP is specified when adding the logger entry.
For the remote syslog server configuration, ensure that the firewall allows incoming TCP connections from the following source IPs:
| Syslog Source IP |
|---|
| 52.15.174.51 3.130.129.118 3.139.10.5 |
- <logger name>_issuing_httpd
- <logger name>_issuing (Issuing EJBCA)
- <logger name>_root_httpd
- <logger name>_root (Issuing EJBCA)
The tags can be used to filter the logs into separate log files.
Logging Format
All deployments run in a Kubernetes environment, and the logs are forwarded from the Kubernetes controller's log store. This means that the first three fields are Kubernetes specific and likely not of interest:
Field 1 - The time Kubernetes wrote the log entry
Field 2 - The source of the log entry. Only the stdout messages are of interest. EJBCA will not output logs to stderr. Httpd is currently outputting some irrelevant log entries on stderr.
Field 3 - Whether the line was wrapped
After that, there are two log streams types of interest, HTTPD and EJBCA.
Note that the httpd messages on stderr can be ignored
HTTPD (stdout):
| Field | Format | Description |
|---|---|---|
| 4 | %h | Remote IP |
| 5 | %A:%p | Local IP:Port (note that this is not likely an interesting IP, since it will be internal to the cluster) |
| 6 | %l | Remote log name |
| 7 | %u | Remote user |
| 8 | %t | Request recieved time |
| 9 | %r (in quotes) | First line of HTTP request |
| 10 | %>s | Final request status |
| 11 | %b | Request size in bytes, excluding headers |
EJBCA:
| Field | Format | Description |
|---|---|---|
| 4 | %d | DateTime |
| 5 | %-5p | Log Level |
| 6 | %c | Log category |
| 7 | %t | Thread ID that generated the log entry |
| 8 | %s%e%n | Log message text and possible exception |
Adding a TCP Logger
To add a TCP Logger:
- Click Logging to access the Logging page.
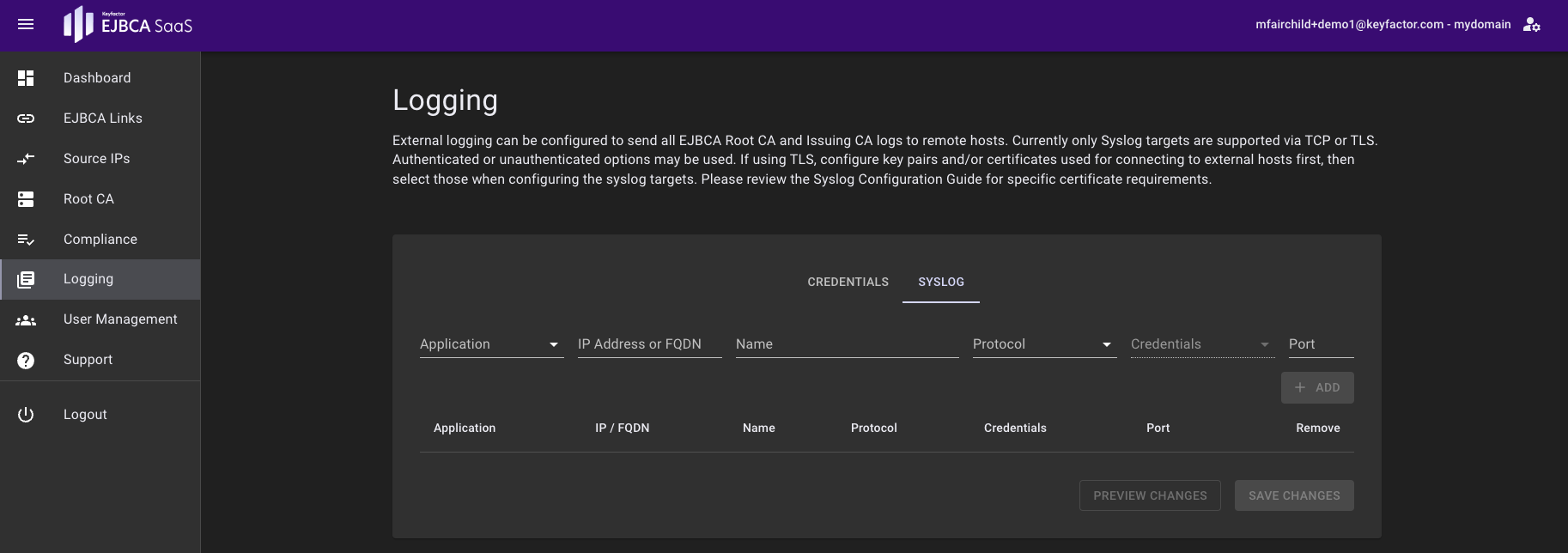
- Specify the fields for the TCP logger entry, then click Add:
- Application: Select Root, Issuing, or Both. This will restrict the logger to stream only the Root logs, only the Issuing logs, or both the Root and Issuing logs.
- IP Address or FQDN: IP Address or FQDN of the remote syslog server. See the note in the Overview for more information.
- Name: Name of the logger entry. The logger name is referenced in the syslog application tags. The name is converted to lowercase with spaces replaced with dashes (e.g. "TCP Logger" is converted to "tcp-logger").
- Protocol: Select TCP-Unencrypted.
- Credentials: This field is disabled for TCP logger entries.
- Port: Specify the syslog port. 514 is the default port for TCP.
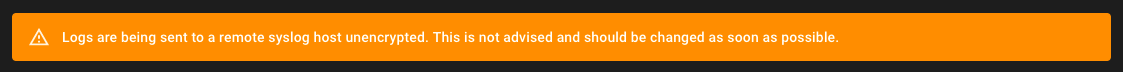
Since TCP logger entries should only be used for testing connectivity, a TCP Unencrypted Selected warning dialog is displayed. Click Yes, continue.
A warning banner is displayed on every page of the portal if a TCP logger entry is configured, and will remain until the logger entry is removed.
The Syslog entry page performs batch operations on logger entries. So, multiple entries may be added or removed from the list of loggers before saving the changes. The changes are not applied until you click Save Changes.
When there are unsaved changes, the table of logger entries will not automatically refresh.
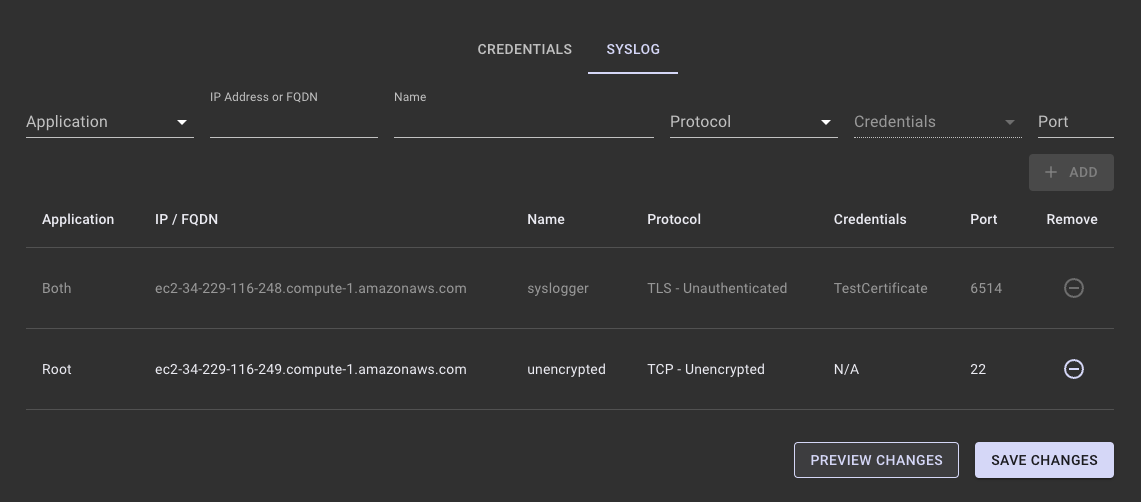
Click Preview Changes to view the list of proposed changes.
- Click Save Changes to add the logger (or click Clear Changes to undo any unsaved changes). Note that you may also click Save Changes directly.
- The logger entry is greyed out while the syslog container is being provisioned on the backend. It appears white once the logger is active.
- Once the logger is active, it is streaming logs to the specified syslog server IP address or FQDN.
Example TCP rsyslog.conf
# rsyslog configuration file
# For more information see /usr/share/doc/rsyslog-*/rsyslog_conf.html
# If you experience problems, see http://www.rsyslog.com/doc/troubleshoot.html
#### MODULES ####
# The imjournal module below is now used as a message source instead of imuxsock.
$ModLoad imuxsock # provides support for local system logging (e.g. via logger command)
$ModLoad imjournal # provides access to the systemd journal
#### GLOBAL DIRECTIVES ####
# Where to place auxiliary files
$WorkDirectory /var/lib/rsyslog
# Use default timestamp format
$ActionFileDefaultTemplate RSYSLOG_TraditionalFileFormat
# File syncing capability is disabled by default. This feature is usually not required,
# not useful and an extreme performance hit
#$ActionFileEnableSync on
# Include all config files in /etc/rsyslog.d/
$IncludeConfig /etc/rsyslog.d/*.conf
# Turn off message reception via local log socket;
# local messages are retrieved through imjournal now.
$OmitLocalLogging on
# File to store the position in the journal
$IMJournalStateFile imjournal.state
module(load="imtcp")
input(type="imtcp" port="514")
if ( $programname == "tcp-logger_issuing_httpd" ) then {
action(type="omfile" file="/var/log/tcp-logger_issuing_httpd.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tcp-logger_issuing" ) then {
action(type="omfile" file="/var/log/tcp-logger_issuing_ejbca.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tcp-logger_root_httpd" ) then {
action(type="omfile" file="/var/log/tcp-logger_root_httpd.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tcp-logger_root" ) then {
action(type="omfile" file="/var/log/tcp-logger_root.log" flushOnTXEnd="on")
stop
}
#### RULES ####
# Log all kernel messages to the console.
# Logging much else clutters up the screen.
#kern.* /dev/console
# Log anything (except mail) of level info or higher.
# Don't log private authentication messages!
*.info;mail.none;authpriv.none;cron.none /var/log/messages
# The authpriv file has restricted access.
authpriv.* /var/log/secure
# Log all the mail messages in one place.
mail.* -/var/log/maillog
# Log cron stuff
cron.* /var/log/cron
# Everybody gets emergency messages
*.emerg :omusrmsg:*
# Save news errors of level crit and higher in a special file.
uucp,news.crit /var/log/spooler
# Save boot messages also to boot.log
local7.* /var/log/boot.log
# ### begin forwarding rule ###
# The statement between the begin ... end define a SINGLE forwarding
# rule. They belong together, do NOT split them. If you create multiple
# forwarding rules, duplicate the whole block!
# Remote Logging (we use TCP for reliable delivery)
#
# An on-disk queue is created for this action. If the remote host is
# down, messages are spooled to disk and sent when it is up again.
#$ActionQueueFileName fwdRule1 # unique name prefix for spool files
#$ActionQueueMaxDiskSpace 1g # 1gb space limit (use as much as possible)
#$ActionQueueSaveOnShutdown on # save messages to disk on shutdown
#$ActionQueueType LinkedList # run asynchronously
#$ActionResumeRetryCount -1 # infinite retries if host is down
# remote host is: name/ip:port, e.g. 192.168.0.1:514, port optional
#*.* @@remote-host:514
# ### end of the forwarding rule ###Adding a TLS Unauthenticated Logger
To add a TLS Unauthenticated Logger:
- Click Logging to access the Logging page.
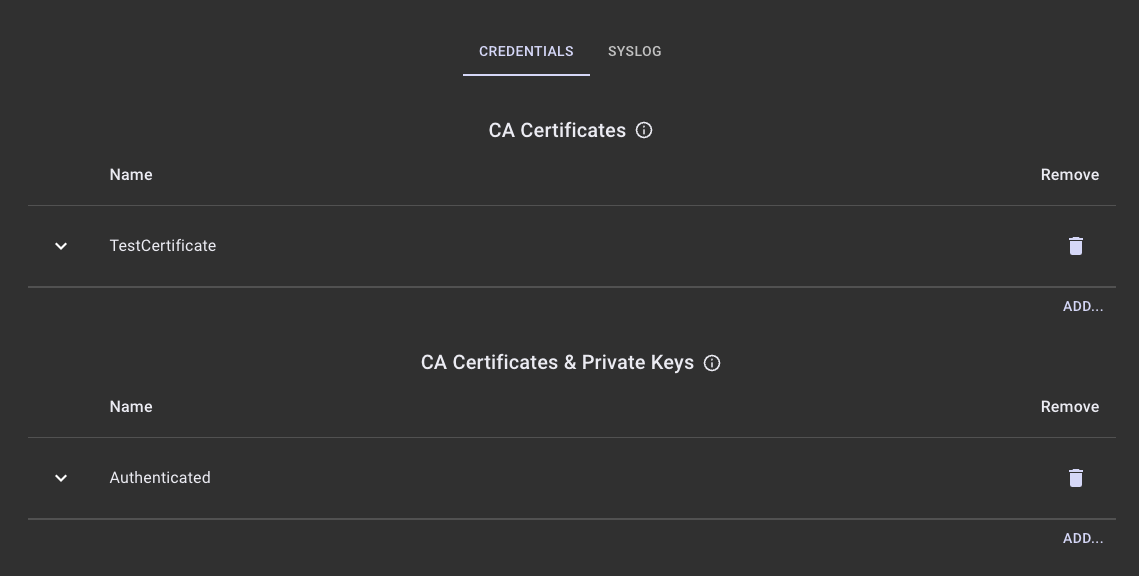
- Click Add under CA Certificates.
- Specify a name for the credential entry and drag a CA Certificate PEM file into the drop zone area, then click ADD. The PEM file must contain the trust store for the remote syslog server's TLS certificate.
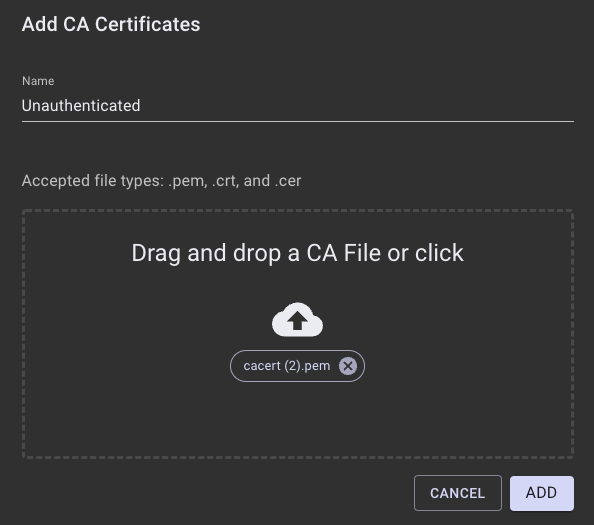
- Open the Syslog accordion.
- Specify the fields for the TLS Unauthenticated logger entry, then click Add:
- Application: Select Root, Issuing, or Both. This will restrict the logger to stream only the Root logs, only the Issuing logs, or both the Root and Issuing logs.
- IP Address or FQDN: IP Address or FQDN of the remote syslog server. See the note in the Overview for more information.
- Name: Name of the logger entry. The logger name is referenced in the syslog application tags. The name is converted to lowercase with spaces replaced with dashes (e.g. "TLS Unauth" is converted to "tls-unauth").
- Protocol: Select TLS-Unauthenticated.
- Credentials: Select the credentials added in step 4. CA Certificate credentials must be added before adding a TLS Unauthenticated logger.
- Port: Specify the syslog port. 6514 is the default port for TLS.
- Click Save Changes to add the logger. Note that you may also preview the proposed changes before saving the changes by clicking Preview Changes.
- The logger entry is greyed out while the syslog container is being provisioned on the backend. It appear swhite once the logger is active.
- Once the logger is active, it is streaming logs to the specified syslog server IP address or FQDN.
Example TLS Unauthenticated rsyslog.conf
# rsyslog configuration file
# For more information see /usr/share/doc/rsyslog-*/rsyslog_conf.html
# If you experience problems, see http://www.rsyslog.com/doc/troubleshoot.html
#### MODULES ####
# The imjournal module below is now used as a message source instead of imuxsock.
$ModLoad imuxsock # provides support for local system logging (e.g. via logger command)
$ModLoad imjournal # provides access to the systemd journal
#### TLS ####
$MaxOpenFiles 2048
# make gtls driver the default
$DefaultNetstreamDriver gtls
# certificate files generated on RHEL6 and stored in /root
$DefaultNetstreamDriverCAFile /etc/pki/rsyslog/cacert.pem
$DefaultNetstreamDriverCertFile /etc/pki/rsyslog/servercert.pem
$DefaultNetstreamDriverKeyFile /etc/pki/rsyslog/serverkey.pem
# Provides TCP syslog reception
# for parameters see http://www.rsyslog.com/doc/imtcp.html
module(load="imtcp"
MaxSessions="2000"
StreamDriver.mode="1"
StreamDriver.authmode="anon")
input(type="imtcp" port="6514" name="tcp-tls")
#### GLOBAL DIRECTIVES ####
# Where to place auxiliary files
$WorkDirectory /var/lib/rsyslog
# Use default timestamp format
$ActionFileDefaultTemplate RSYSLOG_TraditionalFileFormat
# File syncing capability is disabled by default. This feature is usually not required,
# not useful and an extreme performance hit
#$ActionFileEnableSync on
# Include all config files in /etc/rsyslog.d/
$IncludeConfig /etc/rsyslog.d/*.conf
# Turn off message reception via local log socket;
# local messages are retrieved through imjournal now.
$OmitLocalLogging on
# File to store the position in the journal
$IMJournalStateFile imjournal.state
if ( $programname == "tls-unauth_issuing_httpd" ) then {
action(type="omfile" file="/var/log/tls-unauth_issuing_httpd.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tls-unauth_issuing" ) then {
action(type="omfile" file="/var/log/tls-unauth_issuing.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tls-unauth_root_httpd" ) then {
action(type="omfile" file="/var/log/tls-unauth_root_httpd.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tls-unauth_root" ) then {
action(type="omfile" file="/var/log/tls-unauth_root.log" flushOnTXEnd="on")
stop
}
#### RULES ####
# Log all kernel messages to the console.
# Logging much else clutters up the screen.
#kern.* /dev/console
# Log anything (except mail) of level info or higher.
# Don't log private authentication messages!
*.info;mail.none;authpriv.none;cron.none /var/log/messages
# The authpriv file has restricted access.
authpriv.* /var/log/secure
# Log all the mail messages in one place.
mail.* -/var/log/maillog
# Log cron stuff
cron.* /var/log/cron
# Everybody gets emergency messages
*.emerg :omusrmsg:*
# Save news errors of level crit and higher in a special file.
uucp,news.crit /var/log/spooler
# Save boot messages also to boot.log
local7.* /var/log/boot.log
# ### begin forwarding rule ###
# The statement between the begin ... end define a SINGLE forwarding
# rule. They belong together, do NOT split them. If you create multiple
# forwarding rules, duplicate the whole block!
# Remote Logging (we use TCP for reliable delivery)
#
# An on-disk queue is created for this action. If the remote host is
# down, messages are spooled to disk and sent when it is up again.
#$ActionQueueFileName fwdRule1 # unique name prefix for spool files
#$ActionQueueMaxDiskSpace 1g # 1gb space limit (use as much as possible)
#$ActionQueueSaveOnShutdown on # save messages to disk on shutdown
#$ActionQueueType LinkedList # run asynchronously
#$ActionResumeRetryCount -1 # infinite retries if host is down
# remote host is: name/ip:port, e.g. 192.168.0.1:514, port optional
#*.* @@remote-host:514
# ### end of the forwarding rule ###Adding a TLS Authenticated Logger
To add a TLS Authenticated Logger:
- Click Logging to access the Logging page.

- Click Add under CA Certificates and Private Keys.
- Specify a name for the credential entry and drag a CA file, a client certificate, and a client private key PEM file into the drop zone area, and then click Add. The CA file must contain the trust store for the remote syslog server's TLS certificate. The client certificate will be verified against the CA file configured on the remote syslog server.
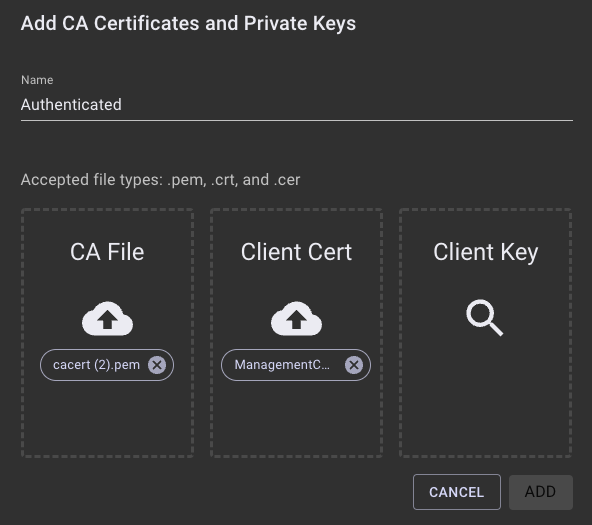
- Click the credential row to expand it and view the Subject DN, Issuer DN, and expiration date of the uploaded certificates.
- Click the SYSLOG tab.
- Specify the fields for the TLS Unauthenticated logger entry, then click Add:
- Application: Select Root, Issuing, or Both. This will restrict the logger to stream only the Root logs, only the Issuing logs, or both the Root and Issuing logs.
- IP Address or FQDN: IP Address or FQDN of the remote syslog server. See the note in the Overview for more information.
- Name: Name of the logger entry. The logger name is referenced in the syslog application tags. The name is converted to lowercase with spaces replaced with dashes (e.g. "TLS Auth" is converted to "tls-auth").
- Protocol: Select TLS-Authenticated.
- Credentials: Select the credentials added in step 4. The credentials must be added before adding a TLS Authenticated logger.
- Port: Specify the syslog port. 6514 is the default port for TLS.
- Click Save Changes to add the logger. Note that you may also preview the proposed changes before saving the changes by clicking Preview Changes.
- The logger entry is greyed out while the syslog container is being provisioned on the backend. It appears white once the logger is active.
- Once the logger is active, it is streaming logs to the specified syslog server IP address or FQDN.
The example rsyslog configuration file below validates that client certificate CN matches "sysclient", using the x509/name StreamDriver auth mode with PermittedPeer = "sysclient".
Example TLS Authenticated rsyslog.conf
# rsyslog configuration file
# For more information see /usr/share/doc/rsyslog-*/rsyslog_conf.html
# If you experience problems, see http://www.rsyslog.com/doc/troubleshoot.html
#### MODULES ####
# The imjournal module below is now used as a message source instead of imuxsock.
$ModLoad imuxsock # provides support for local system logging (e.g. via logger command)
$ModLoad imjournal # provides access to the systemd journal
# Provides UDP syslog reception
#$ModLoad imudp
#$UDPServerRun 514
# Provides TCP syslog reception
#$ModLoad imtcp
#$InputTCPServerRun 514
#### TLS ####
$MaxOpenFiles 2048
# make gtls driver the default
$DefaultNetstreamDriver gtls
# certificate files generated on RHEL6 and stored in /root
$DefaultNetstreamDriverCAFile /etc/pki/rsyslog/cacert.pem
$DefaultNetstreamDriverCertFile /etc/pki/rsyslog/servercert.pem
$DefaultNetstreamDriverKeyFile /etc/pki/rsyslog/serverkey.pem
# Provides TCP syslog reception
# for parameters see http://www.rsyslog.com/doc/imtcp.html
module(load="imtcp"
MaxSessions="2000"
StreamDriver.mode="1"
StreamDriver.authmode="x509/name"
PermittedPeer="sysclient")
input(type="imtcp" port="6514" name="tcp-tls")
#### GLOBAL DIRECTIVES ####
# Where to place auxiliary files
$WorkDirectory /var/lib/rsyslog
# Use default timestamp format
$ActionFileDefaultTemplate RSYSLOG_TraditionalFileFormat
# File syncing capability is disabled by default. This feature is usually not required,
# not useful and an extreme performance hit
#$ActionFileEnableSync on
# Include all config files in /etc/rsyslog.d/
$IncludeConfig /etc/rsyslog.d/*.conf
# Turn off message reception via local log socket;
# local messages are retrieved through imjournal now.
$OmitLocalLogging on
# File to store the position in the journal
$IMJournalStateFile imjournal.state
#module(load="imtcp")
#input(type="imtcp" port="514")
if ( $programname == "tls-auth_issuing_httpd" ) then {
action(type="omfile" file="/var/log/tls-auth_issuing_httpd.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tls-auth_issuing" ) then {
action(type="omfile" file="/var/log/tls-auth_issuing_ejbca.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tls-auth_root_httpd" ) then {
action(type="omfile" file="/var/log/tls-auth_root_httpd.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tls-auth_root" ) then {
action(type="omfile" file="/var/log/tls-auth_root_ejbca.log" flushOnTXEnd="on")
stop
}
#### RULES ####
# Log all kernel messages to the console.
# Logging much else clutters up the screen.
#kern.* /dev/console
# Log anything (except mail) of level info or higher.
# Don't log private authentication messages!
*.info;mail.none;authpriv.none;cron.none /var/log/messages
# The authpriv file has restricted access.
authpriv.* /var/log/secure
# Log all the mail messages in one place.
mail.* -/var/log/maillog
# Log cron stuff
cron.* /var/log/cron
# Everybody gets emergency messages
*.emerg :omusrmsg:*
# Save news errors of level crit and higher in a special file.
uucp,news.crit /var/log/spooler
# Save boot messages also to boot.log
local7.* /var/log/boot.log
# ### begin forwarding rule ###
# The statement between the begin ... end define a SINGLE forwarding
# rule. They belong together, do NOT split them. If you create multiple
# forwarding rules, duplicate the whole block!
# Remote Logging (we use TCP for reliable delivery)
#
# An on-disk queue is created for this action. If the remote host is
# down, messages are spooled to disk and sent when it is up again.
#$ActionQueueFileName fwdRule1 # unique name prefix for spool files
#$ActionQueueMaxDiskSpace 1g # 1gb space limit (use as much as possible)
#$ActionQueueSaveOnShutdown on # save messages to disk on shutdown
#$ActionQueueType LinkedList # run asynchronously
#$ActionResumeRetryCount -1 # infinite retries if host is down
# remote host is: name/ip:port, e.g. 192.168.0.1:514, port optional
#*.* @@remote-host:514
# ### end of the forwarding rule ###Next - Manage Users
To learn how to create users and edit or delete existing users, see Manage Users.
EJBCA SaaS supports streaming logs to an external logging server. The following covers how to configure syslog log streaming of the Issuing and Root CA, HTTPd and EJBCA logs to remote syslog servers.
Overview
Any log management service that accepts syslog stream inputs over TCP may be used. EJBCA SaaS supports syslog log streaming over TCP or TLS (Authenticated or Unauthenticated).
- TCP logger: Since TCP connections are not encrypted, TCP should only be used for testing connectivity.
- TLS Unauthenticated Logger: TLS Unauthenticated logger configurations require a CA certificate (or trust store) to be uploaded via the portal, to perform server validation of the remote syslog server.
- TLS Authenticated Logger: TLS Authenticated loggers perform mutual TLS authentication and require a CA certificate (or trust store), client private key, and client certificate to be uploaded via the portal.
The certificates and private keys uploaded for logging are stored securely in the Secrets Manager.
For both Authenticated and Unauthenticated TLS, the TLS server certificate installed on the remote syslog server must include the FQDN or IP in the CN or dnsName SAN, depending on if the FQDN or IP is specified when adding the logger entry.
For the remote syslog server configuration, ensure that the firewall allows incoming TCP connections from the following source IPs:
| Syslog Source IP |
|---|
| 52.15.174.51 3.130.129.118 3.139.10.5 |
- <logger name>_issuing_httpd
- <logger name>_issuing (Issuing EJBCA)
- <logger name>_root_httpd
- <logger name>_root (Issuing EJBCA)
The tags can be used to filter the logs into separate log files.
Adding a TCP Logger
To add a TCP Logger:
- Click Logging to access the Logging page.
- Specify the fields for the TCP logger entry, then click Add:
- Application: Select Root, Issuing, or Both. This will restrict the logger to stream only the Root logs, only the Issuing logs, or both the Root and Issuing logs.
- IP Address or FQDN: IP Address or FQDN of the remote syslog server. See the note in the Overview for more information.
- Name: Name of the logger entry. The logger name is referenced in the syslog application tags. The name is converted to lowercase with spaces replaced with dashes (e.g. "TCP Logger" is converted to "tcp-logger").
- Protocol: Select TCP-Unencrypted.
- Credentials: This field is disabled for TCP logger entries.
- Port: Specify the syslog port. 514 is the default port for TCP.
Since TCP logger entries should only be used for testing connectivity, a TCP Unencrypted Selected warning dialog is displayed. Click Yes, continue.
A warning banner is displayed on every page of the portal if a TCP logger entry is configured, and will remain until the logger entry is removed.

The Syslog entry page performs batch operations on logger entries. So, multiple entries may be added or removed from the list of loggers before saving the changes. The changes are not applied until you click Save Changes.
When there are unsaved changes, the table of logger entries will not automatically refresh.
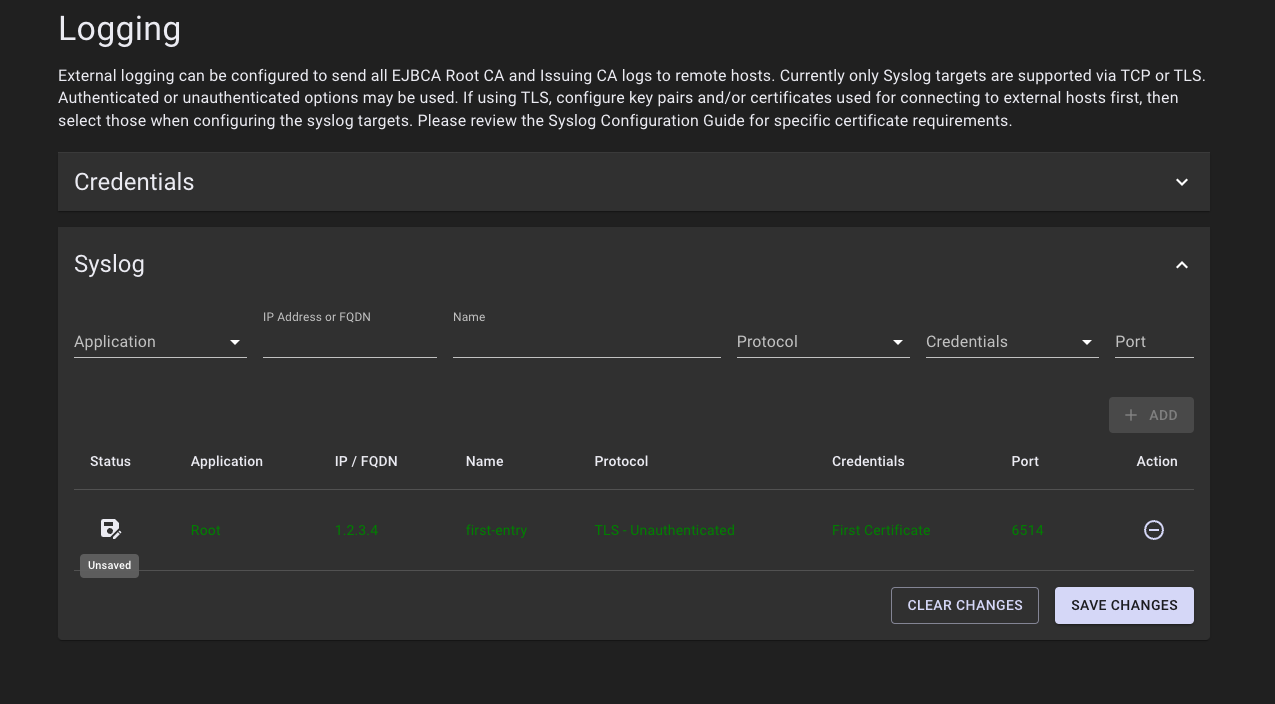
Loggers that were added to the list, but not yet saved, will display in green with a status of Unsaved.
- Click Save Changes to add the logger (or click Clear Changes to undo any unsaved changes).
- The logger entry is greyed out while the syslog container is being provisioned on the backend. It appears white once the logger is active.
- Once the logger is active, it is streaming logs to the specified syslog server IP address or FQDN.
Example TCP rsyslog.conf
# rsyslog configuration file
# For more information see /usr/share/doc/rsyslog-*/rsyslog_conf.html
# If you experience problems, see http://www.rsyslog.com/doc/troubleshoot.html
#### MODULES ####
# The imjournal module below is now used as a message source instead of imuxsock.
$ModLoad imuxsock # provides support for local system logging (e.g. via logger command)
$ModLoad imjournal # provides access to the systemd journal
#### GLOBAL DIRECTIVES ####
# Where to place auxiliary files
$WorkDirectory /var/lib/rsyslog
# Use default timestamp format
$ActionFileDefaultTemplate RSYSLOG_TraditionalFileFormat
# File syncing capability is disabled by default. This feature is usually not required,
# not useful and an extreme performance hit
#$ActionFileEnableSync on
# Include all config files in /etc/rsyslog.d/
$IncludeConfig /etc/rsyslog.d/*.conf
# Turn off message reception via local log socket;
# local messages are retrieved through imjournal now.
$OmitLocalLogging on
# File to store the position in the journal
$IMJournalStateFile imjournal.state
module(load="imtcp")
input(type="imtcp" port="514")
if ( $programname == "tcp-logger_issuing_httpd" ) then {
action(type="omfile" file="/var/log/tcp-logger_issuing_httpd.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tcp-logger_issuing" ) then {
action(type="omfile" file="/var/log/tcp-logger_issuing_ejbca.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tcp-logger_root_httpd" ) then {
action(type="omfile" file="/var/log/tcp-logger_root_httpd.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tcp-logger_root" ) then {
action(type="omfile" file="/var/log/tcp-logger_root.log" flushOnTXEnd="on")
stop
}
#### RULES ####
# Log all kernel messages to the console.
# Logging much else clutters up the screen.
#kern.* /dev/console
# Log anything (except mail) of level info or higher.
# Don't log private authentication messages!
*.info;mail.none;authpriv.none;cron.none /var/log/messages
# The authpriv file has restricted access.
authpriv.* /var/log/secure
# Log all the mail messages in one place.
mail.* -/var/log/maillog
# Log cron stuff
cron.* /var/log/cron
# Everybody gets emergency messages
*.emerg :omusrmsg:*
# Save news errors of level crit and higher in a special file.
uucp,news.crit /var/log/spooler
# Save boot messages also to boot.log
local7.* /var/log/boot.log
# ### begin forwarding rule ###
# The statement between the begin ... end define a SINGLE forwarding
# rule. They belong together, do NOT split them. If you create multiple
# forwarding rules, duplicate the whole block!
# Remote Logging (we use TCP for reliable delivery)
#
# An on-disk queue is created for this action. If the remote host is
# down, messages are spooled to disk and sent when it is up again.
#$ActionQueueFileName fwdRule1 # unique name prefix for spool files
#$ActionQueueMaxDiskSpace 1g # 1gb space limit (use as much as possible)
#$ActionQueueSaveOnShutdown on # save messages to disk on shutdown
#$ActionQueueType LinkedList # run asynchronously
#$ActionResumeRetryCount -1 # infinite retries if host is down
# remote host is: name/ip:port, e.g. 192.168.0.1:514, port optional
#*.* @@remote-host:514
# ### end of the forwarding rule ###Adding a TLS Unauthenticated Logger
To add a TLS Unauthenticated Logger:
- Click Logging to access the Logging page. Open the Credentials accordion.
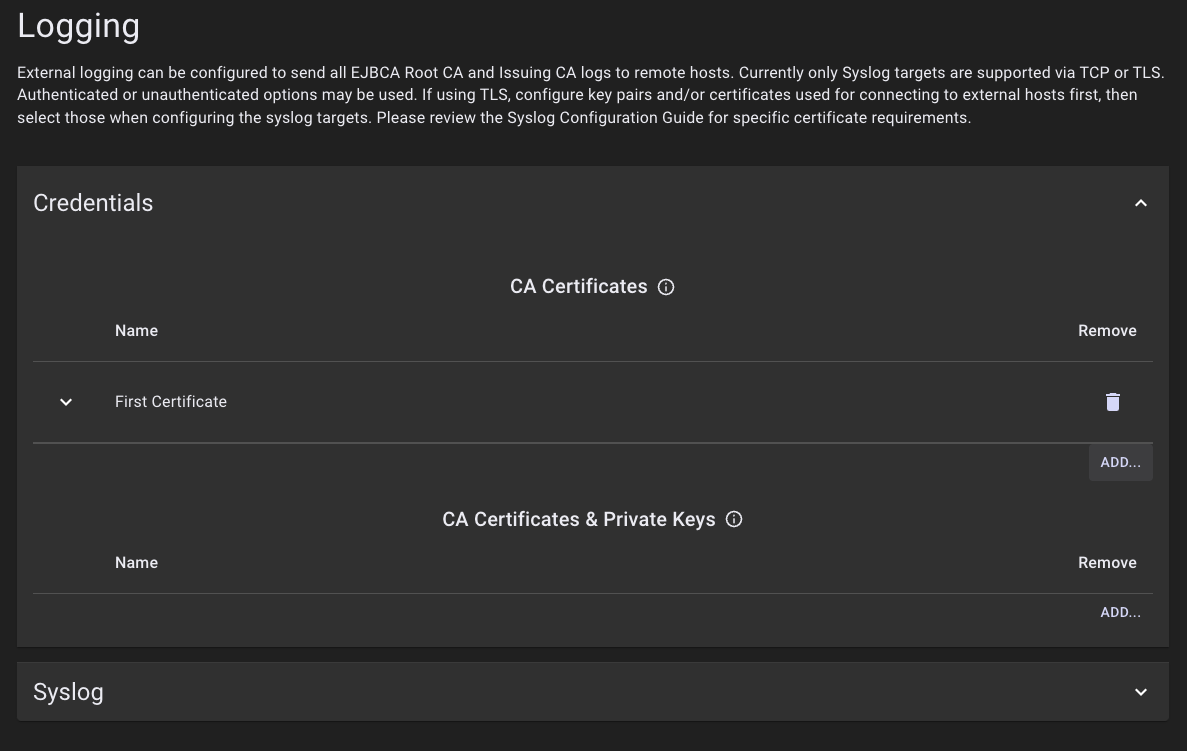
- Click Add under CA Certificates.
- Specify a name for the credential entry and drag a CA Certificate PEM file into the drop zone area, then click ADD. The PEM file must contain the trust store for the remote syslog server's TLS certificate.

- Open the SYSLOG accordion.
- Specify the fields for the TLS Unauthenticated logger entry, then click Add:
- Application: Select Root, Issuing, or Both. This will restrict the logger to stream only the Root logs, only the Issuing logs, or both the Root and Issuing logs.
- IP Address or FQDN: IP Address or FQDN of the remote syslog server. See the note in the Overview for more information.
- Name: Name of the logger entry. The logger name is referenced in the syslog application tags. The name is converted to lowercase with spaces replaced with dashes (e.g. "TLS Unauth" is converted to "tls-unauth").
- Protocol: Select TLS-Unauthenticated.
- Credentials: Select the credentials added in step 4. CA Certificate credentials must be added before adding a TLS Unauthenticated logger.
- Port: Specify the syslog port. 6514 is the default port for TLS.
- Click Save Changes to add the logger. Note that unsaved additions will display in green.
- The logger entry is greyed out while the syslog container is being provisioned on the backend. It appears white once the logger is active.
- Once the logger is active, it is streaming logs to the specified syslog server IP address or FQDN.
Example TLS Unauthenticated rsyslog.conf
# rsyslog configuration file
# For more information see /usr/share/doc/rsyslog-*/rsyslog_conf.html
# If you experience problems, see http://www.rsyslog.com/doc/troubleshoot.html
#### MODULES ####
# The imjournal module below is now used as a message source instead of imuxsock.
$ModLoad imuxsock # provides support for local system logging (e.g. via logger command)
$ModLoad imjournal # provides access to the systemd journal
#### TLS ####
$MaxOpenFiles 2048
# make gtls driver the default
$DefaultNetstreamDriver gtls
# certificate files generated on RHEL6 and stored in /root
$DefaultNetstreamDriverCAFile /etc/pki/rsyslog/cacert.pem
$DefaultNetstreamDriverCertFile /etc/pki/rsyslog/servercert.pem
$DefaultNetstreamDriverKeyFile /etc/pki/rsyslog/serverkey.pem
# Provides TCP syslog reception
# for parameters see http://www.rsyslog.com/doc/imtcp.html
module(load="imtcp"
MaxSessions="2000"
StreamDriver.mode="1"
StreamDriver.authmode="anon")
input(type="imtcp" port="6514" name="tcp-tls")
#### GLOBAL DIRECTIVES ####
# Where to place auxiliary files
$WorkDirectory /var/lib/rsyslog
# Use default timestamp format
$ActionFileDefaultTemplate RSYSLOG_TraditionalFileFormat
# File syncing capability is disabled by default. This feature is usually not required,
# not useful and an extreme performance hit
#$ActionFileEnableSync on
# Include all config files in /etc/rsyslog.d/
$IncludeConfig /etc/rsyslog.d/*.conf
# Turn off message reception via local log socket;
# local messages are retrieved through imjournal now.
$OmitLocalLogging on
# File to store the position in the journal
$IMJournalStateFile imjournal.state
if ( $programname == "tls-unauth_issuing_httpd" ) then {
action(type="omfile" file="/var/log/tls-unauth_issuing_httpd.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tls-unauth_issuing" ) then {
action(type="omfile" file="/var/log/tls-unauth_issuing.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tls-unauth_root_httpd" ) then {
action(type="omfile" file="/var/log/tls-unauth_root_httpd.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tls-unauth_root" ) then {
action(type="omfile" file="/var/log/tls-unauth_root.log" flushOnTXEnd="on")
stop
}
#### RULES ####
# Log all kernel messages to the console.
# Logging much else clutters up the screen.
#kern.* /dev/console
# Log anything (except mail) of level info or higher.
# Don't log private authentication messages!
*.info;mail.none;authpriv.none;cron.none /var/log/messages
# The authpriv file has restricted access.
authpriv.* /var/log/secure
# Log all the mail messages in one place.
mail.* -/var/log/maillog
# Log cron stuff
cron.* /var/log/cron
# Everybody gets emergency messages
*.emerg :omusrmsg:*
# Save news errors of level crit and higher in a special file.
uucp,news.crit /var/log/spooler
# Save boot messages also to boot.log
local7.* /var/log/boot.log
# ### begin forwarding rule ###
# The statement between the begin ... end define a SINGLE forwarding
# rule. They belong together, do NOT split them. If you create multiple
# forwarding rules, duplicate the whole block!
# Remote Logging (we use TCP for reliable delivery)
#
# An on-disk queue is created for this action. If the remote host is
# down, messages are spooled to disk and sent when it is up again.
#$ActionQueueFileName fwdRule1 # unique name prefix for spool files
#$ActionQueueMaxDiskSpace 1g # 1gb space limit (use as much as possible)
#$ActionQueueSaveOnShutdown on # save messages to disk on shutdown
#$ActionQueueType LinkedList # run asynchronously
#$ActionResumeRetryCount -1 # infinite retries if host is down
# remote host is: name/ip:port, e.g. 192.168.0.1:514, port optional
#*.* @@remote-host:514
# ### end of the forwarding rule ###Adding a TLS Authenticated Logger
To add a TLS Authenticated Logger:
- Click Logging to access the Logging page. Open the Credentials accordion.
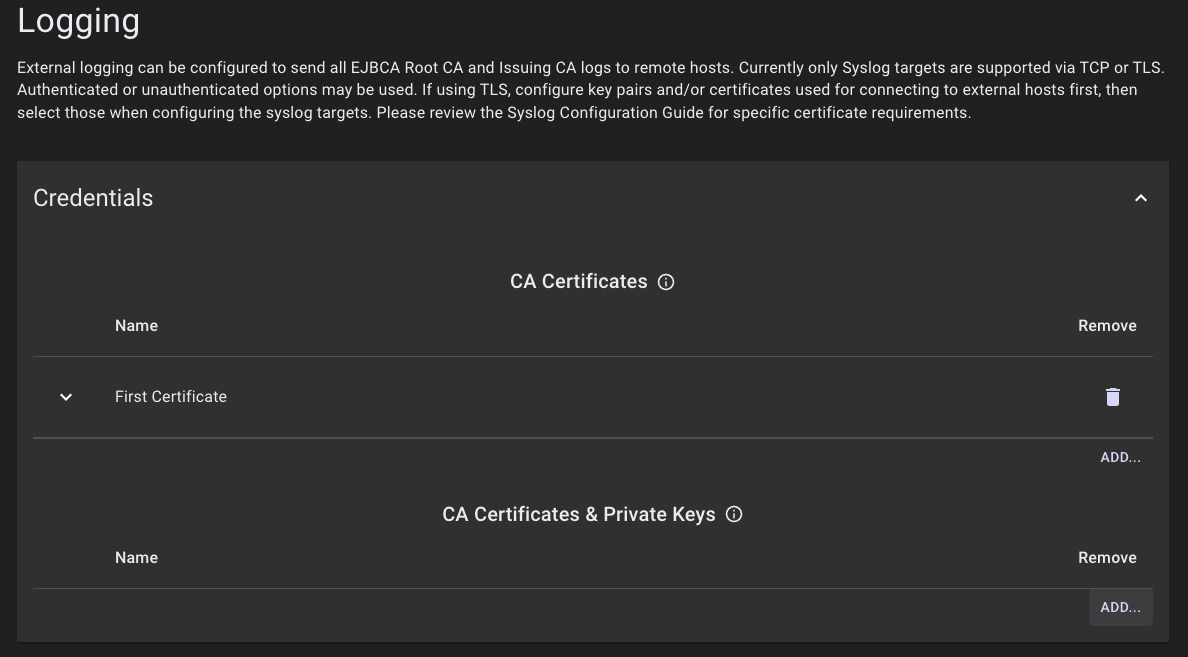
- Click Add under CA Certificates and Private Keys.
- Specify a name for the credential entry and drag a CA file, a client certificate, and a client private key PEM file into the drop zone area, and then click Add. The CA file must contain the trust store for the remote syslog server's TLS certificate. The client certificate will be verified against the CA file configured on the remote syslog server.

- Click the credential row to expand it and view the Subject DN, Issuer DN, and expiration date of the uploaded certificates.
- Open the SYSLOG accordion.
- Specify the fields for the TLS Unauthenticated logger entry, then click Add:
- Application: Select Root, Issuing, or Both. This will restrict the logger to stream only the Root logs, only the Issuing logs, or both the Root and Issuing logs.
- IP Address or FQDN: IP Address or FQDN of the remote syslog server. See the note in the Overview for more information.
- Name: Name of the logger entry. The logger name is referenced in the syslog application tags. The name is converted to lowercase with spaces replaced with dashes (e.g. "TLS Auth" is converted to "tls-auth").
- Protocol: Select TLS-Authenticated.
- Credentials: Select the credentials added in step 4. The credentials must be added before adding a TLS Authenticated logger.
- Port: Specify the syslog port. 6514 is the default port for TLS.
- Click Save Changes to add the logger. Note unsaved additions will display in green.
- The logger entry is greyed out while the syslog container is being provisioned on the backend. It appears white once the logger is active.
- Once the logger is active, it is streaming logs to the specified syslog server IP address or FQDN.
The example rsyslog configuration file below validates that client certificate CN matches "sysclient", using the x509/name StreamDriver auth mode with PermittedPeer = "sysclient".
Example TLS Authenticated rsyslog.conf
# rsyslog configuration file
# For more information see /usr/share/doc/rsyslog-*/rsyslog_conf.html
# If you experience problems, see http://www.rsyslog.com/doc/troubleshoot.html
#### MODULES ####
# The imjournal module below is now used as a message source instead of imuxsock.
$ModLoad imuxsock # provides support for local system logging (e.g. via logger command)
$ModLoad imjournal # provides access to the systemd journal
# Provides UDP syslog reception
#$ModLoad imudp
#$UDPServerRun 514
# Provides TCP syslog reception
#$ModLoad imtcp
#$InputTCPServerRun 514
#### TLS ####
$MaxOpenFiles 2048
# make gtls driver the default
$DefaultNetstreamDriver gtls
# certificate files generated on RHEL6 and stored in /root
$DefaultNetstreamDriverCAFile /etc/pki/rsyslog/cacert.pem
$DefaultNetstreamDriverCertFile /etc/pki/rsyslog/servercert.pem
$DefaultNetstreamDriverKeyFile /etc/pki/rsyslog/serverkey.pem
# Provides TCP syslog reception
# for parameters see http://www.rsyslog.com/doc/imtcp.html
module(load="imtcp"
MaxSessions="2000"
StreamDriver.mode="1"
StreamDriver.authmode="x509/name"
PermittedPeer="sysclient")
input(type="imtcp" port="6514" name="tcp-tls")
#### GLOBAL DIRECTIVES ####
# Where to place auxiliary files
$WorkDirectory /var/lib/rsyslog
# Use default timestamp format
$ActionFileDefaultTemplate RSYSLOG_TraditionalFileFormat
# File syncing capability is disabled by default. This feature is usually not required,
# not useful and an extreme performance hit
#$ActionFileEnableSync on
# Include all config files in /etc/rsyslog.d/
$IncludeConfig /etc/rsyslog.d/*.conf
# Turn off message reception via local log socket;
# local messages are retrieved through imjournal now.
$OmitLocalLogging on
# File to store the position in the journal
$IMJournalStateFile imjournal.state
#module(load="imtcp")
#input(type="imtcp" port="514")
if ( $programname == "tls-auth_issuing_httpd" ) then {
action(type="omfile" file="/var/log/tls-auth_issuing_httpd.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tls-auth_issuing" ) then {
action(type="omfile" file="/var/log/tls-auth_issuing_ejbca.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tls-auth_root_httpd" ) then {
action(type="omfile" file="/var/log/tls-auth_root_httpd.log" flushOnTXEnd="on")
stop
}
if ( $programname == "tls-auth_root" ) then {
action(type="omfile" file="/var/log/tls-auth_root_ejbca.log" flushOnTXEnd="on")
stop
}
#### RULES ####
# Log all kernel messages to the console.
# Logging much else clutters up the screen.
#kern.* /dev/console
# Log anything (except mail) of level info or higher.
# Don't log private authentication messages!
*.info;mail.none;authpriv.none;cron.none /var/log/messages
# The authpriv file has restricted access.
authpriv.* /var/log/secure
# Log all the mail messages in one place.
mail.* -/var/log/maillog
# Log cron stuff
cron.* /var/log/cron
# Everybody gets emergency messages
*.emerg :omusrmsg:*
# Save news errors of level crit and higher in a special file.
uucp,news.crit /var/log/spooler
# Save boot messages also to boot.log
local7.* /var/log/boot.log
# ### begin forwarding rule ###
# The statement between the begin ... end define a SINGLE forwarding
# rule. They belong together, do NOT split them. If you create multiple
# forwarding rules, duplicate the whole block!
# Remote Logging (we use TCP for reliable delivery)
#
# An on-disk queue is created for this action. If the remote host is
# down, messages are spooled to disk and sent when it is up again.
#$ActionQueueFileName fwdRule1 # unique name prefix for spool files
#$ActionQueueMaxDiskSpace 1g # 1gb space limit (use as much as possible)
#$ActionQueueSaveOnShutdown on # save messages to disk on shutdown
#$ActionQueueType LinkedList # run asynchronously
#$ActionResumeRetryCount -1 # infinite retries if host is down
# remote host is: name/ip:port, e.g. 192.168.0.1:514, port optional
#*.* @@remote-host:514
# ### end of the forwarding rule ###Next - Manage Users
To learn how to create users and edit or delete existing users, see Manage Users.